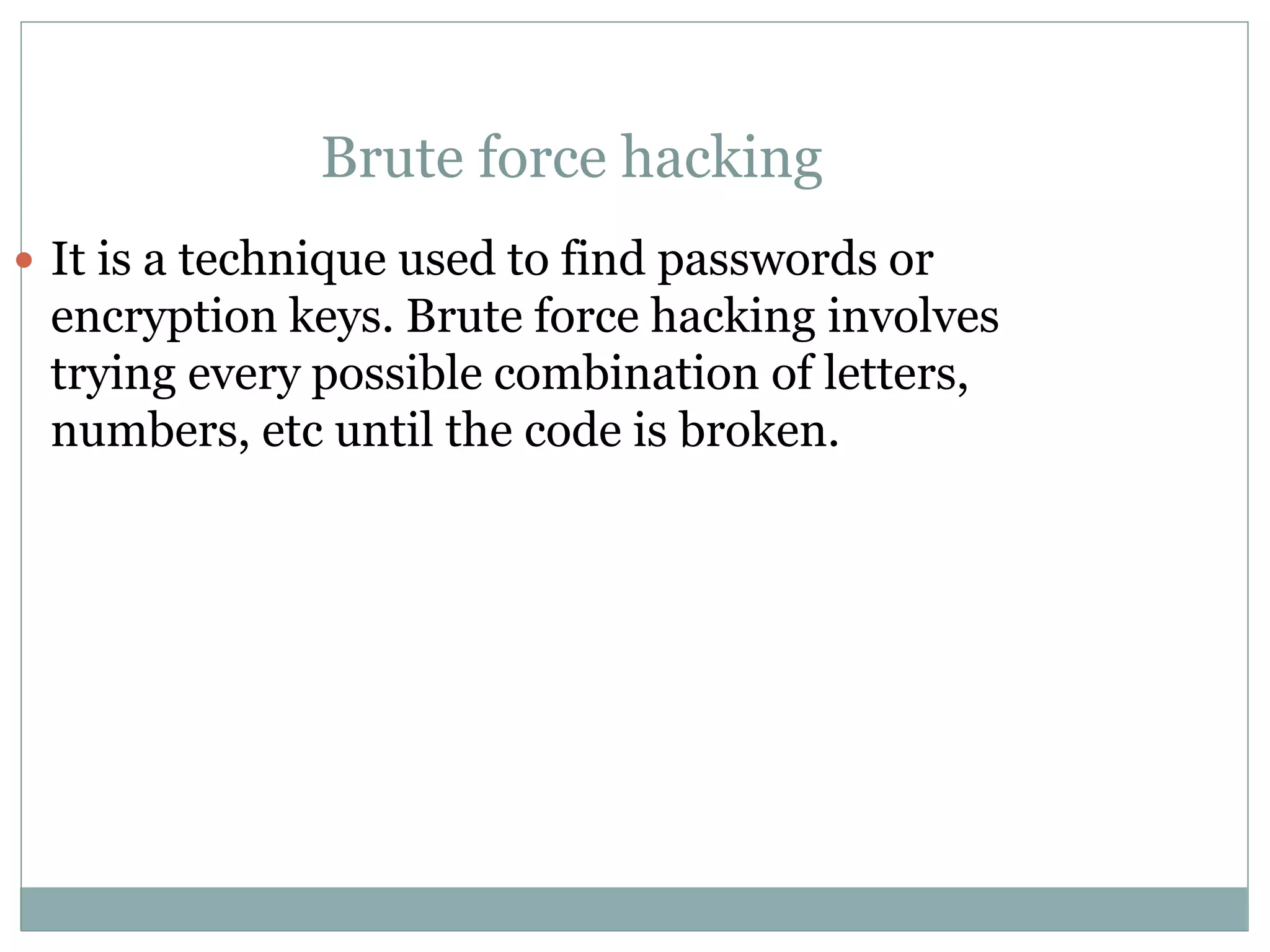
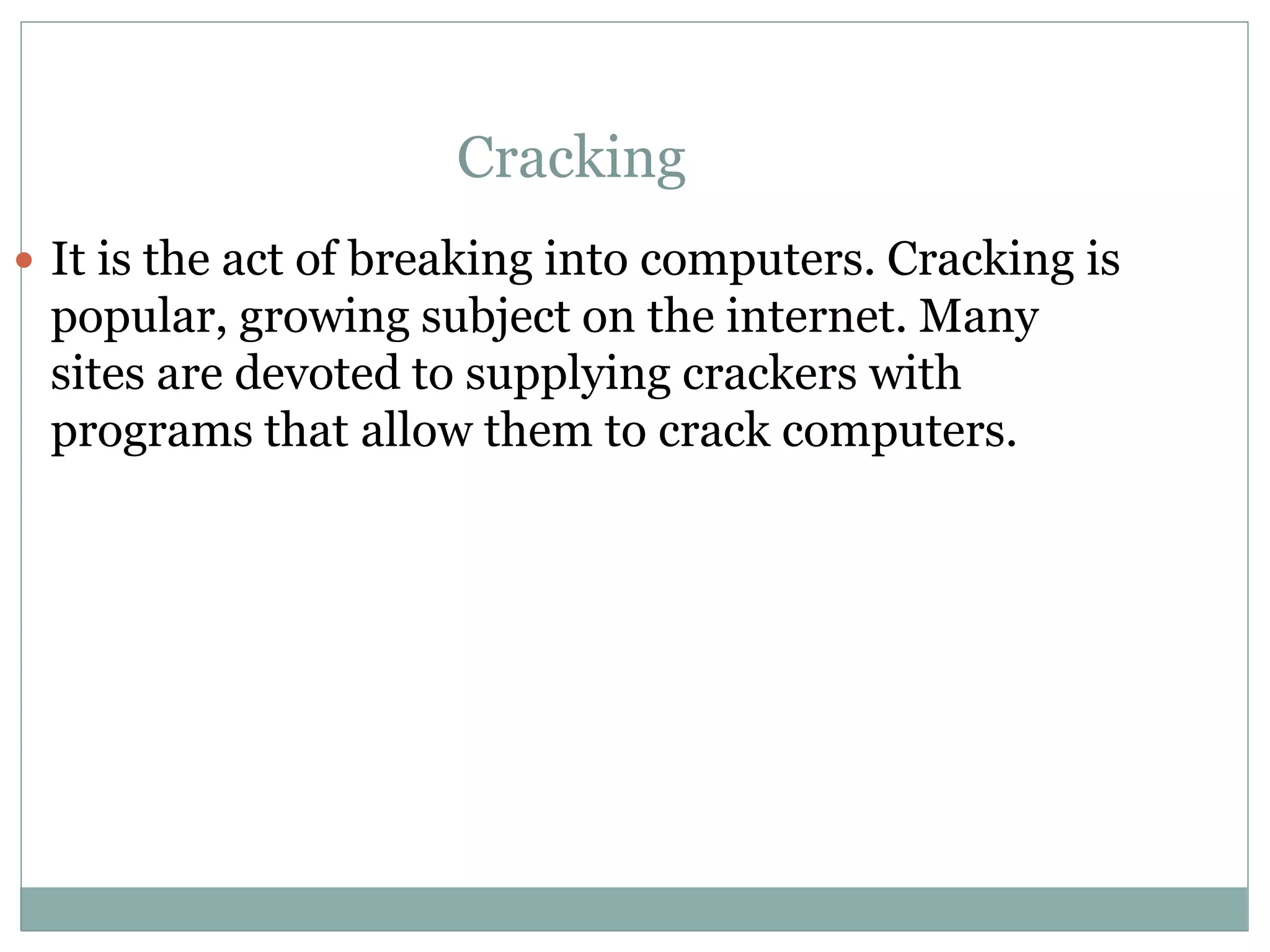
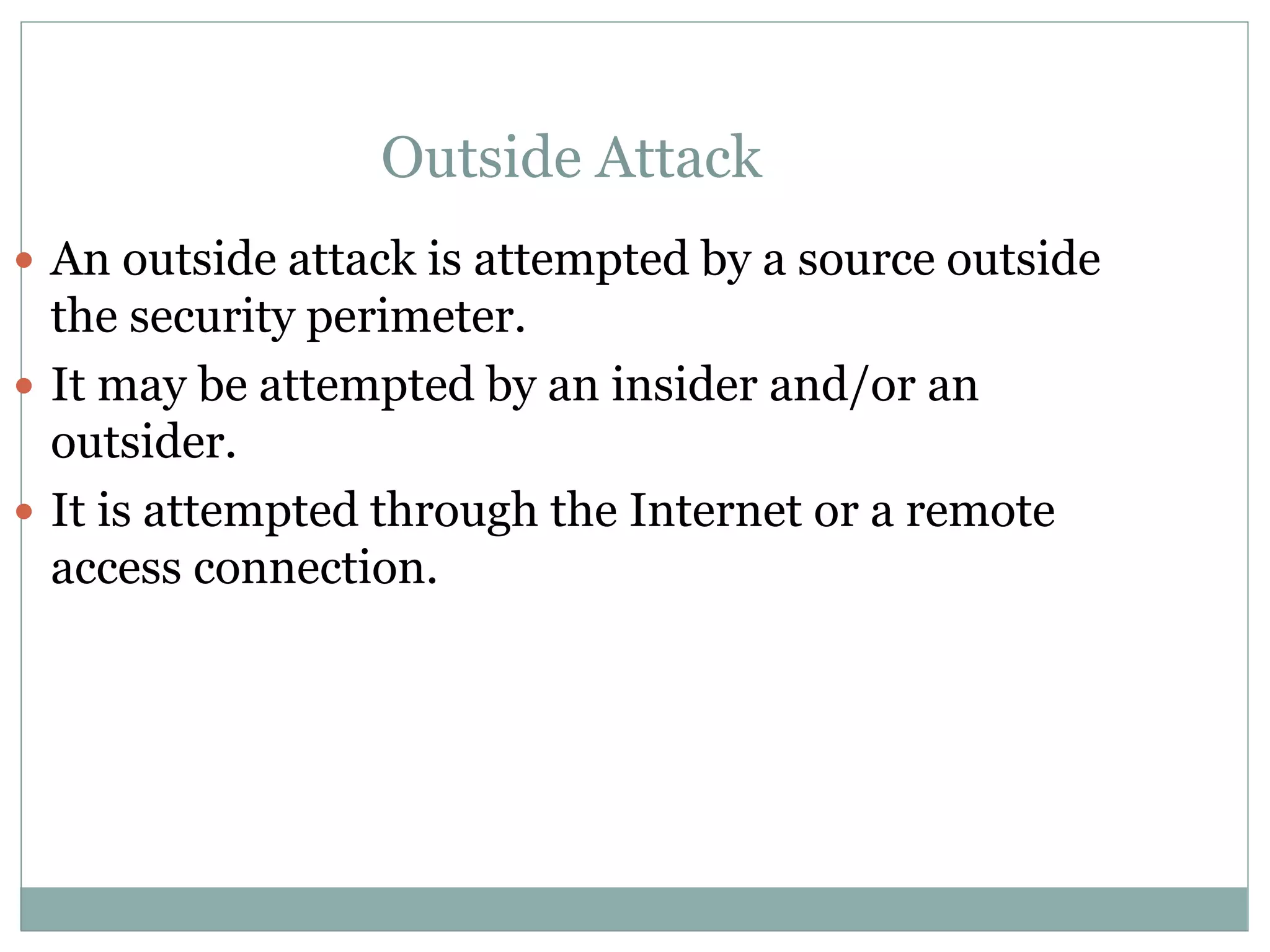
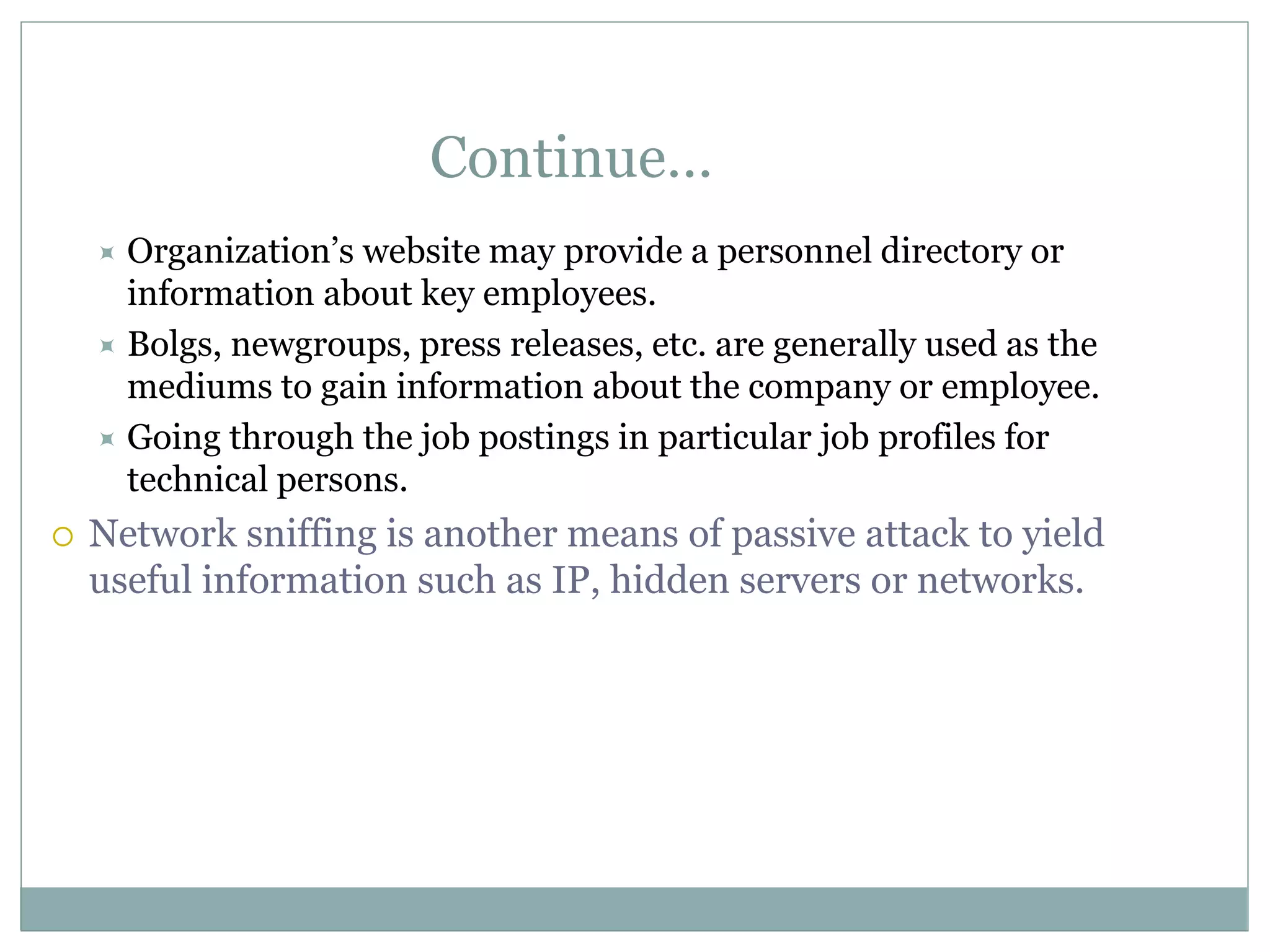
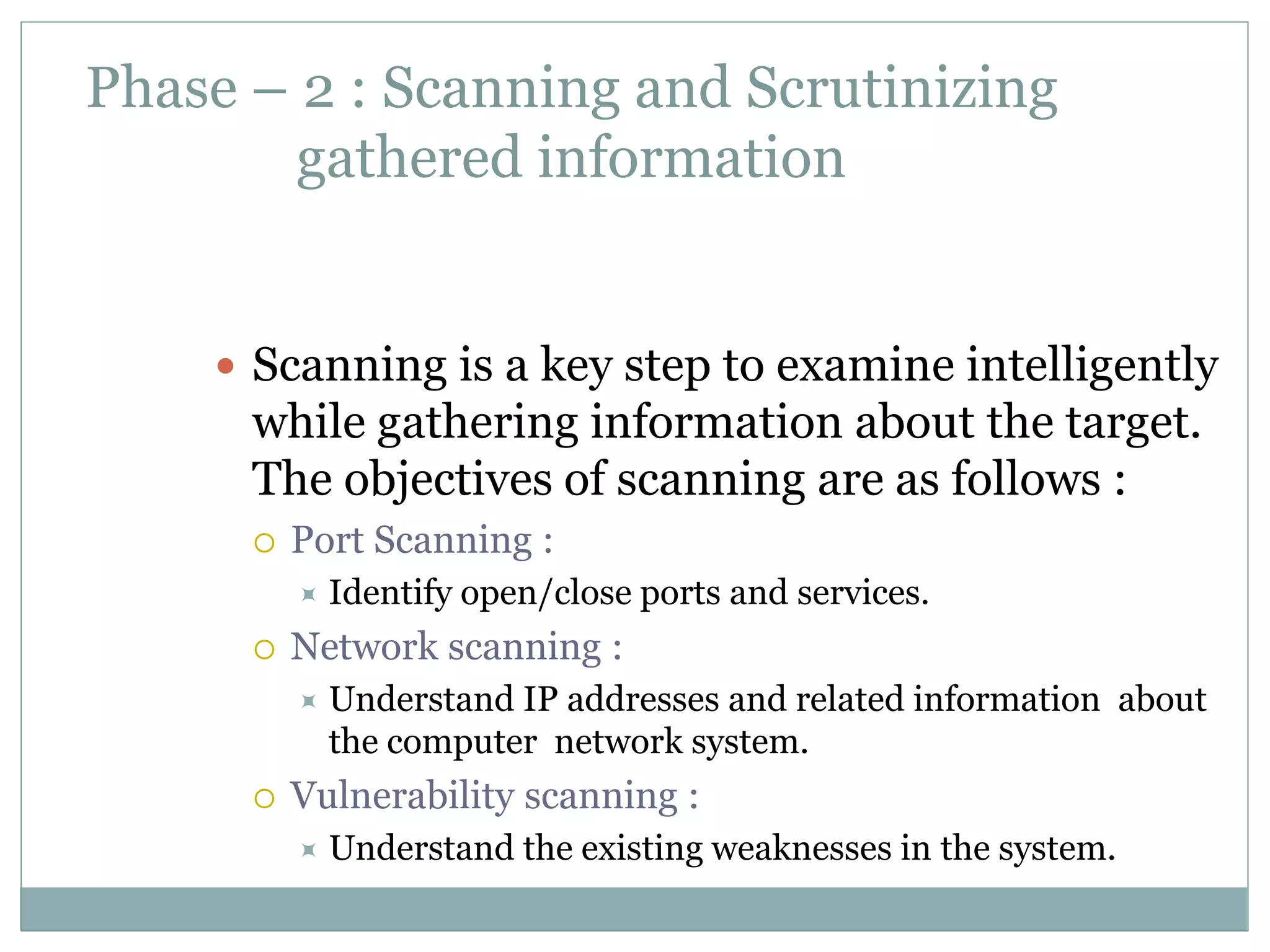
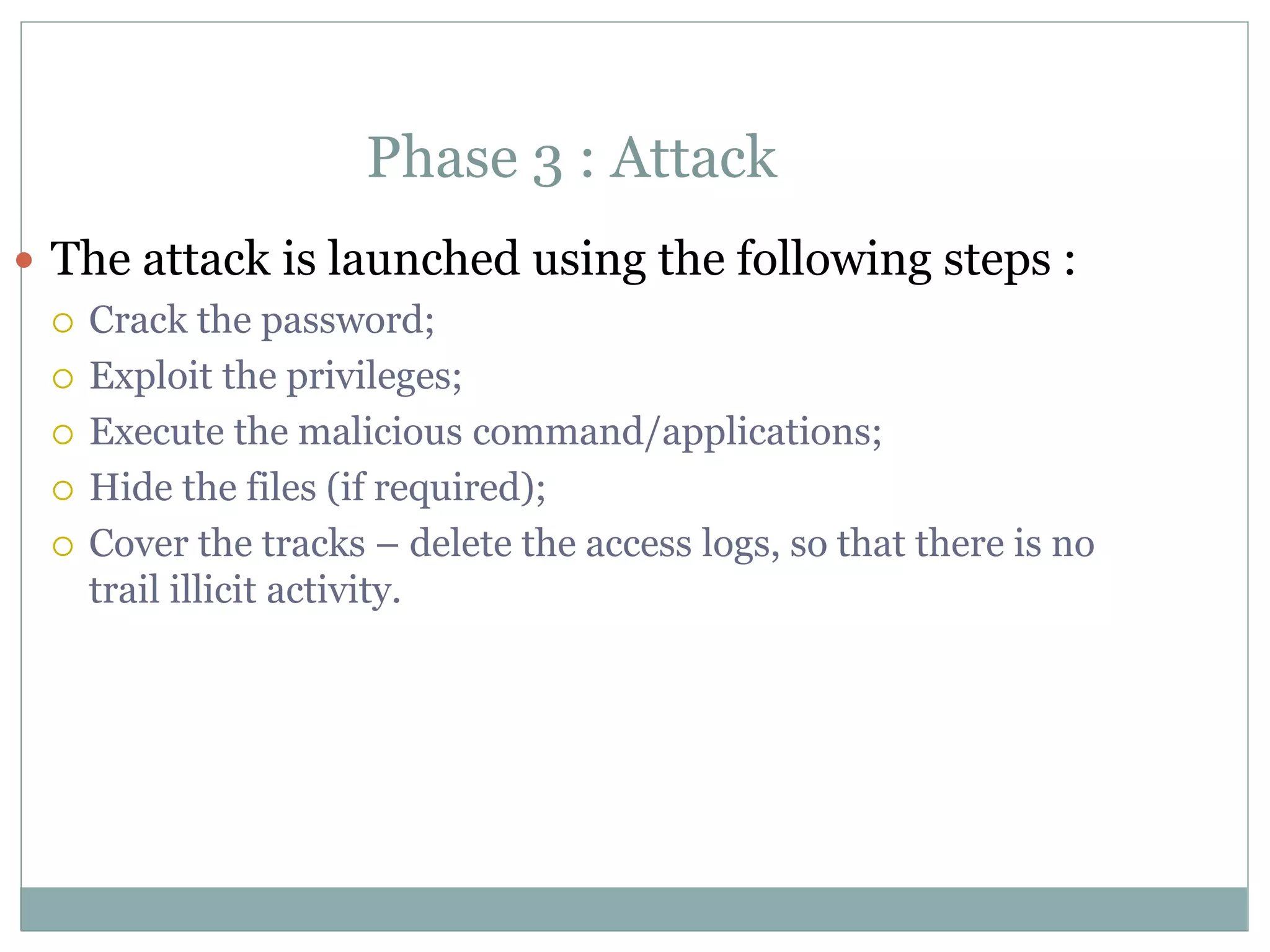
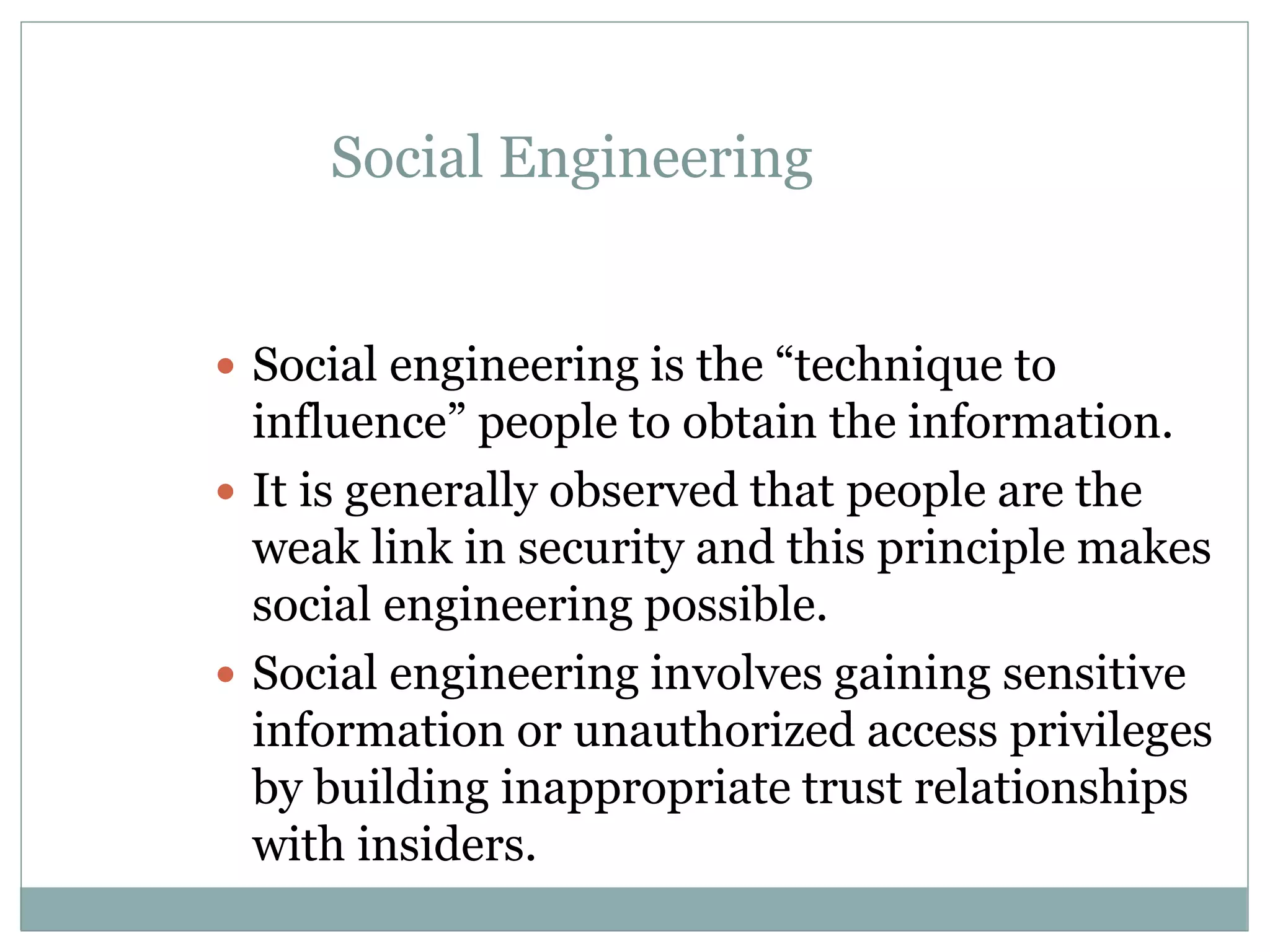
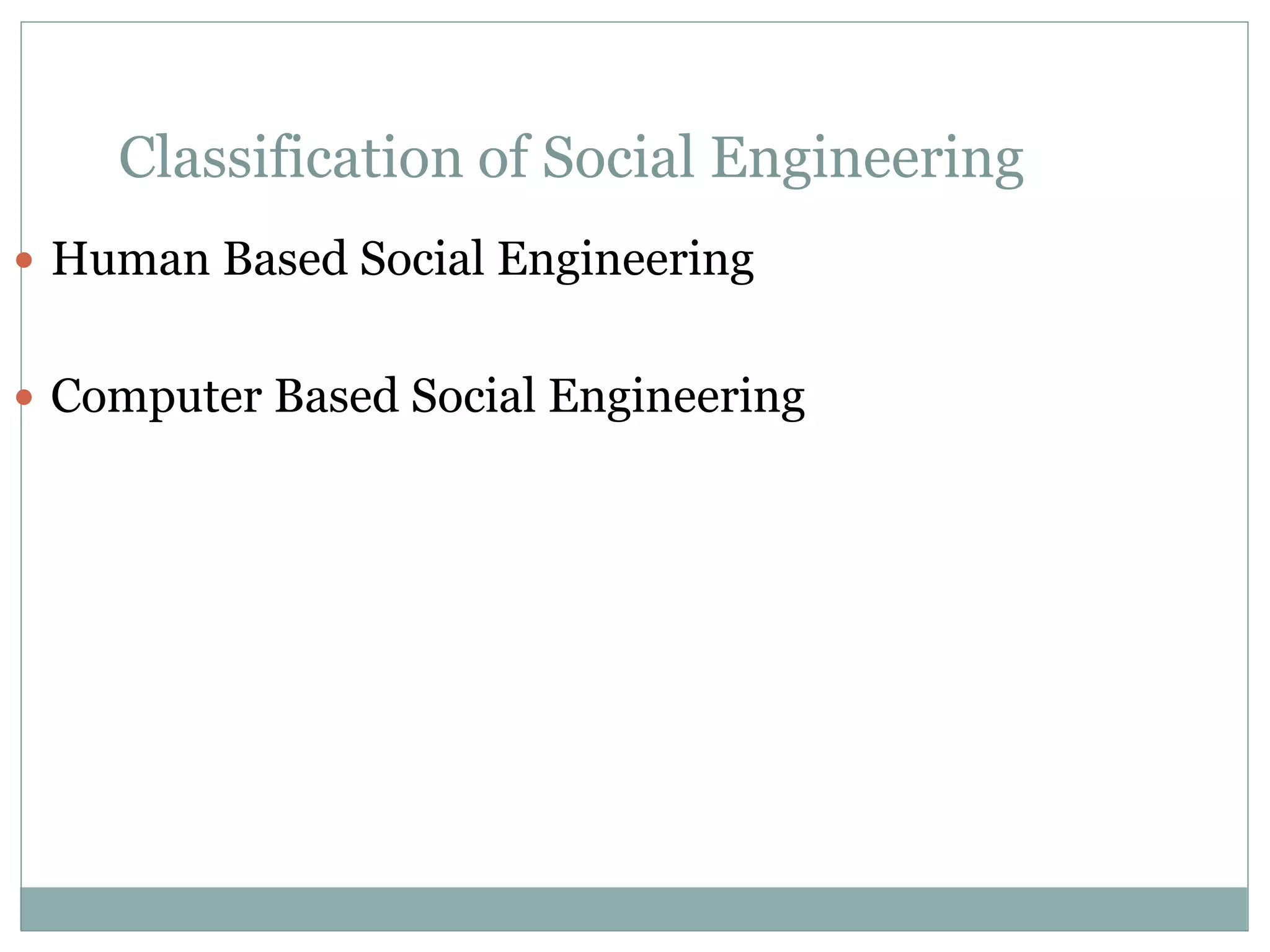
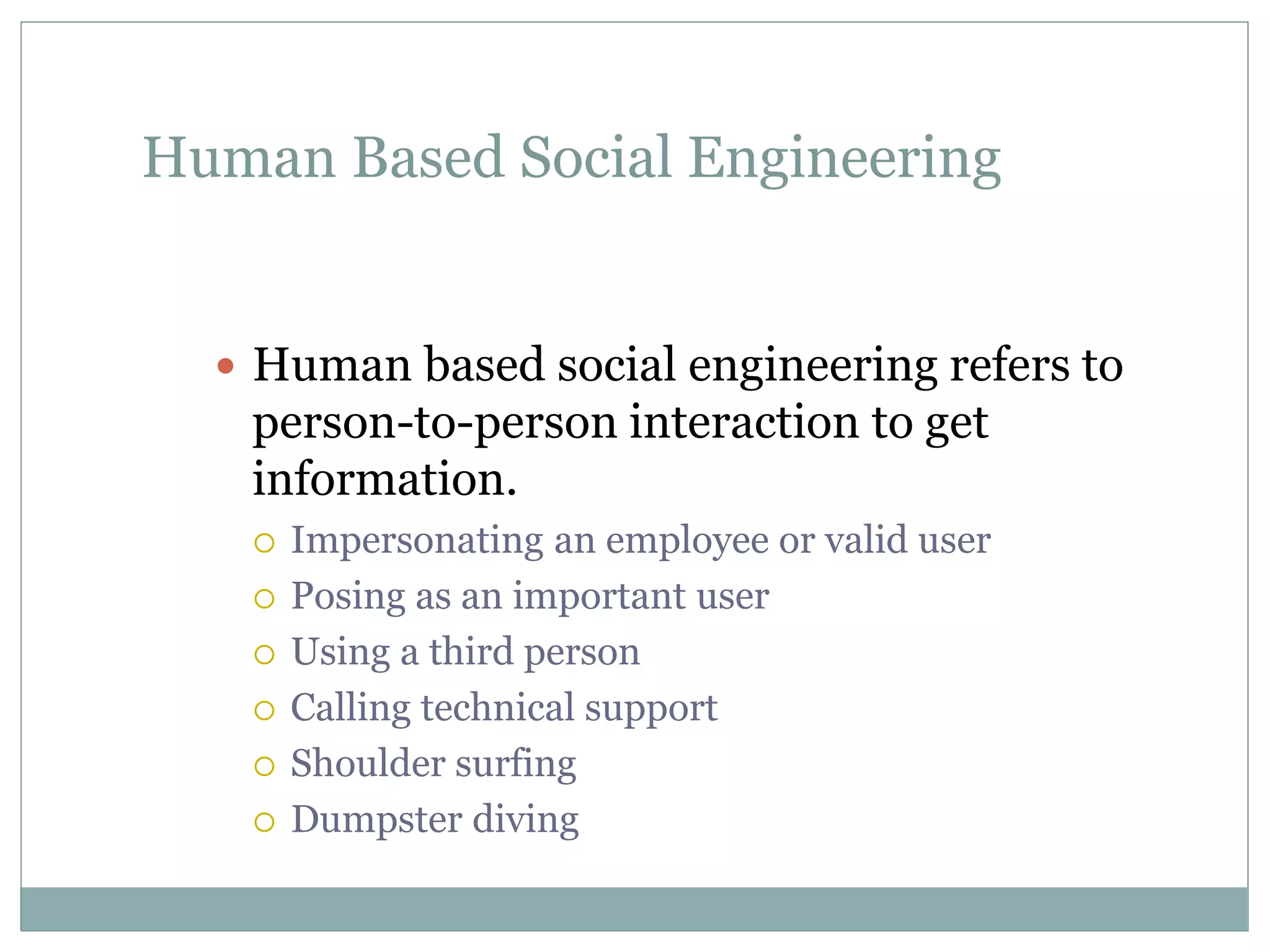
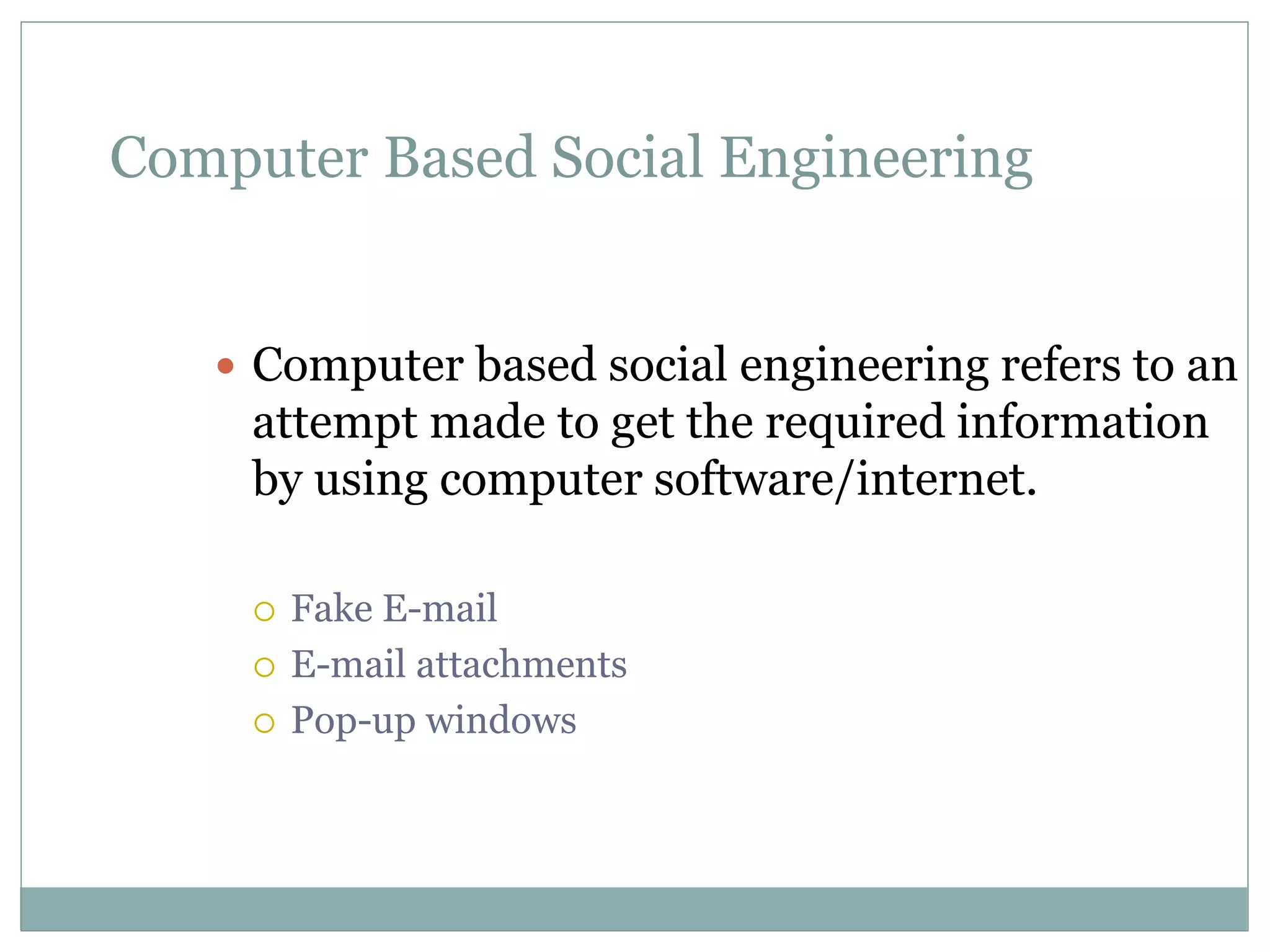
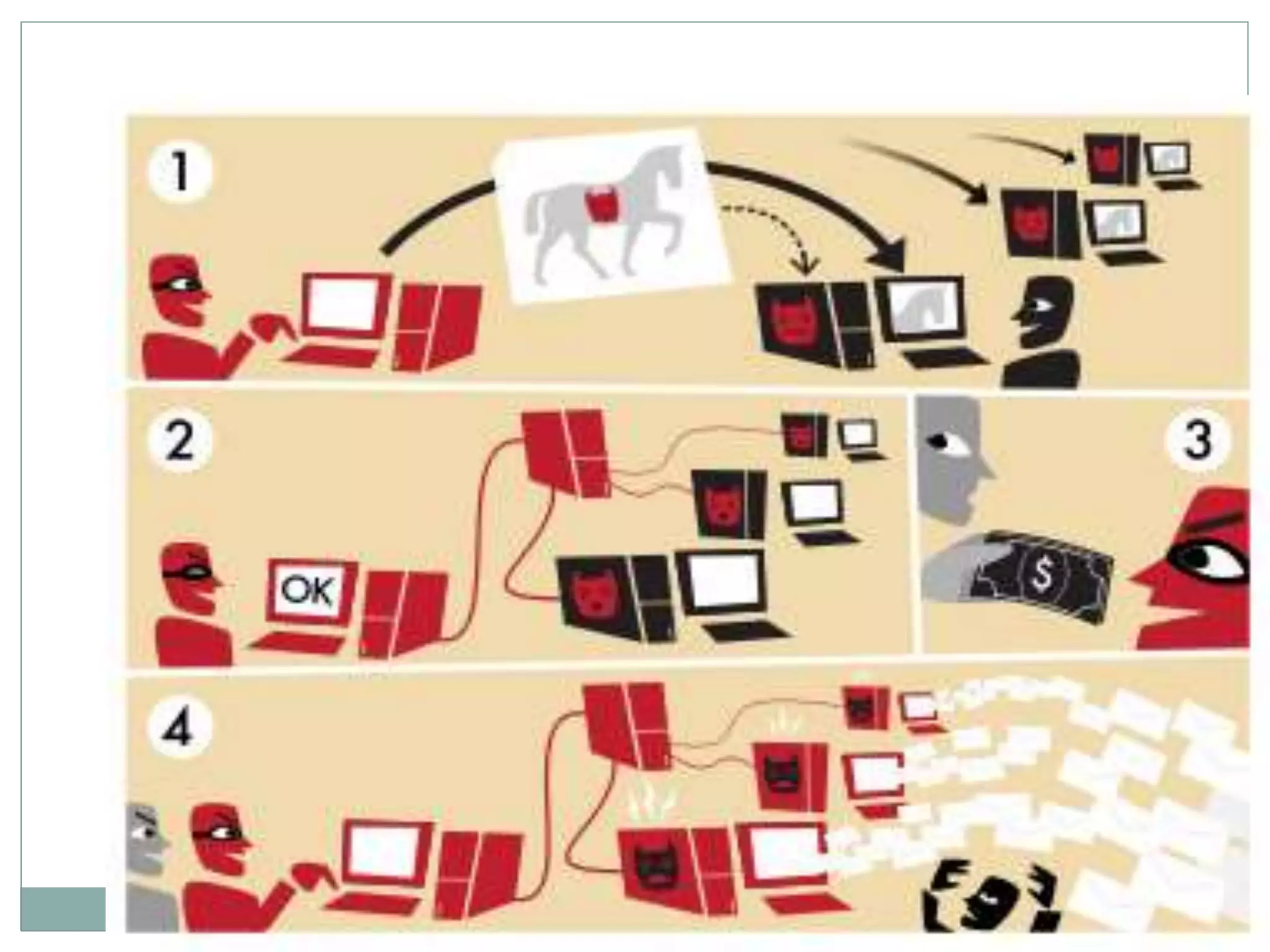
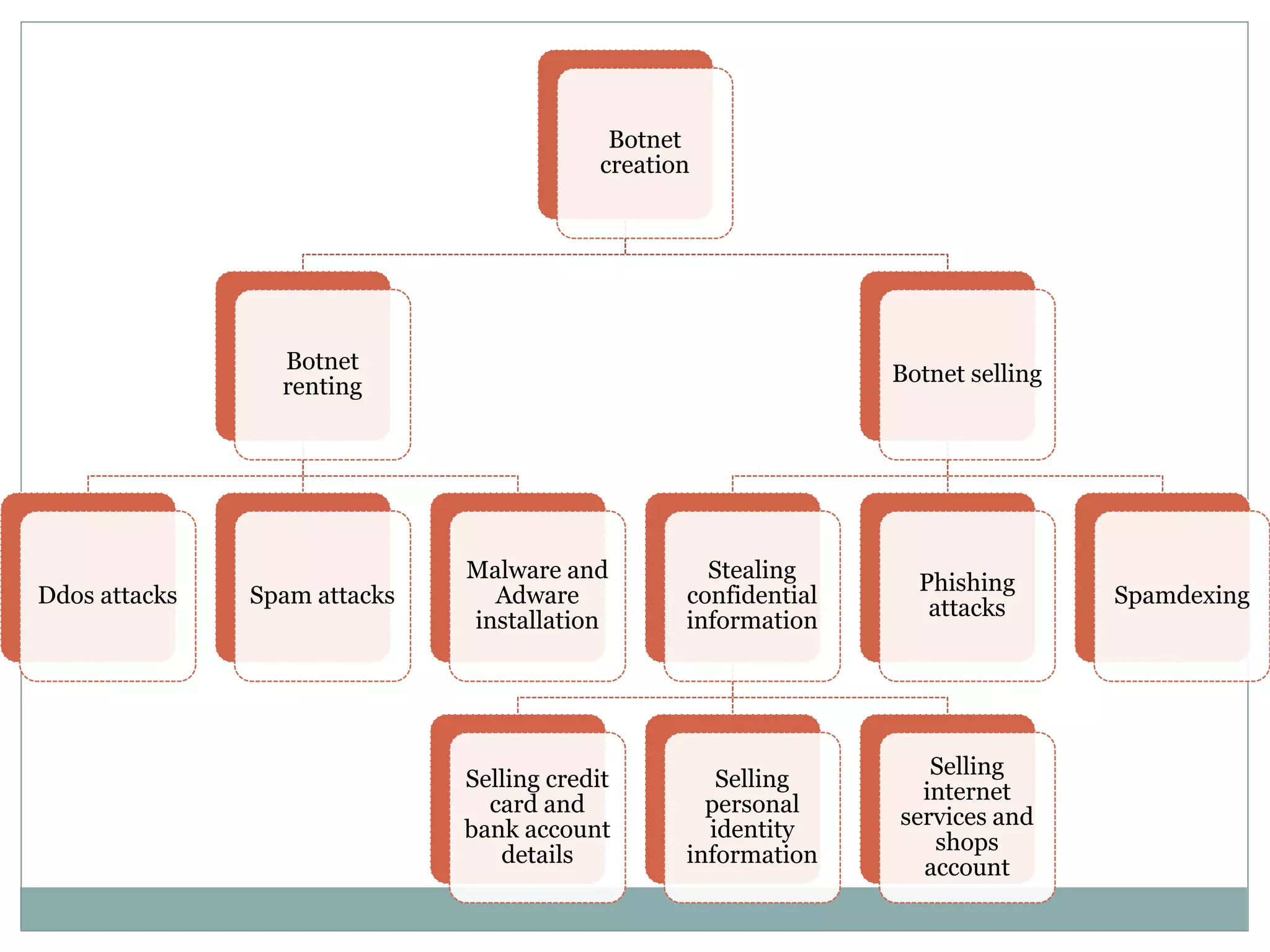
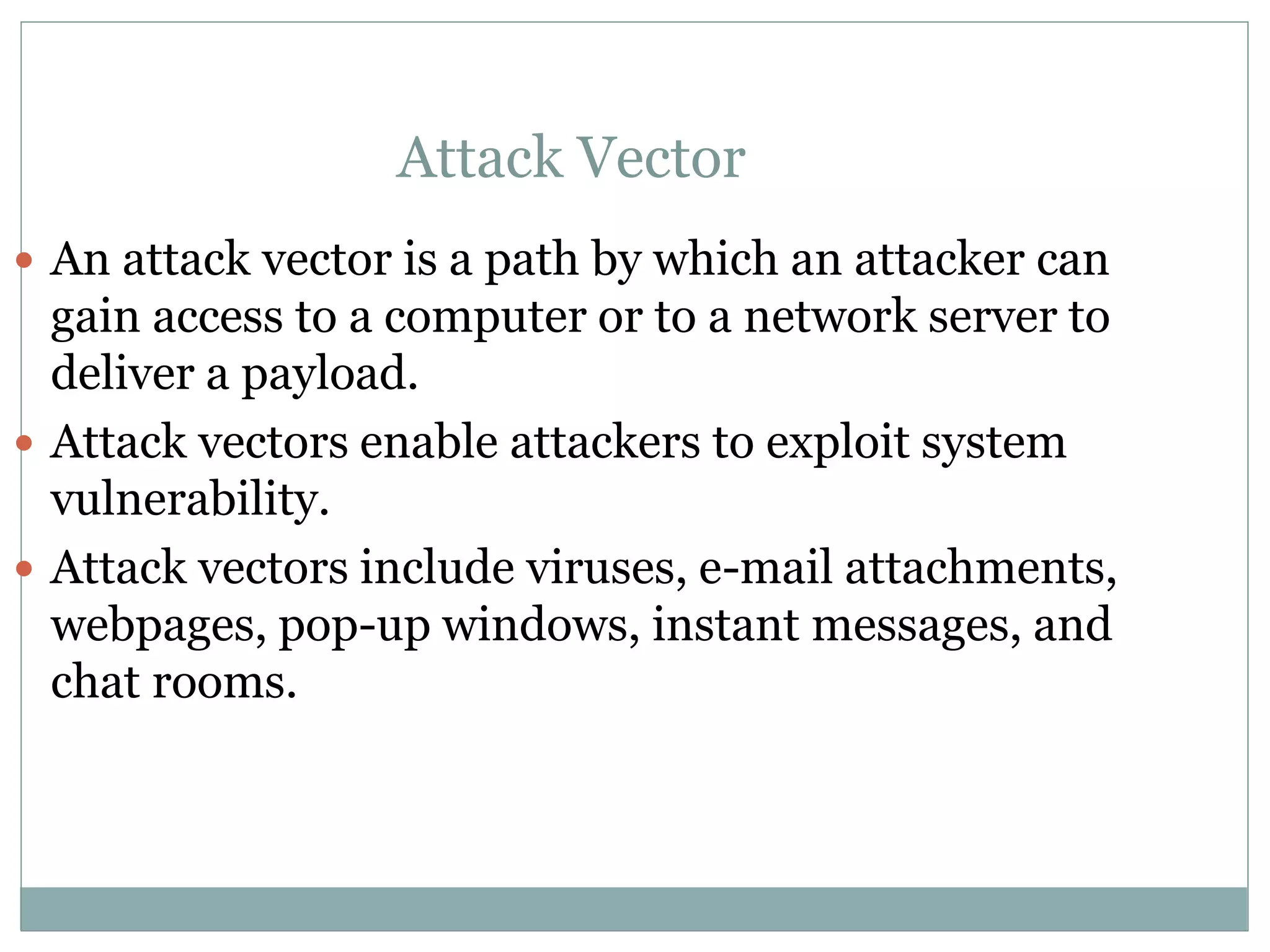
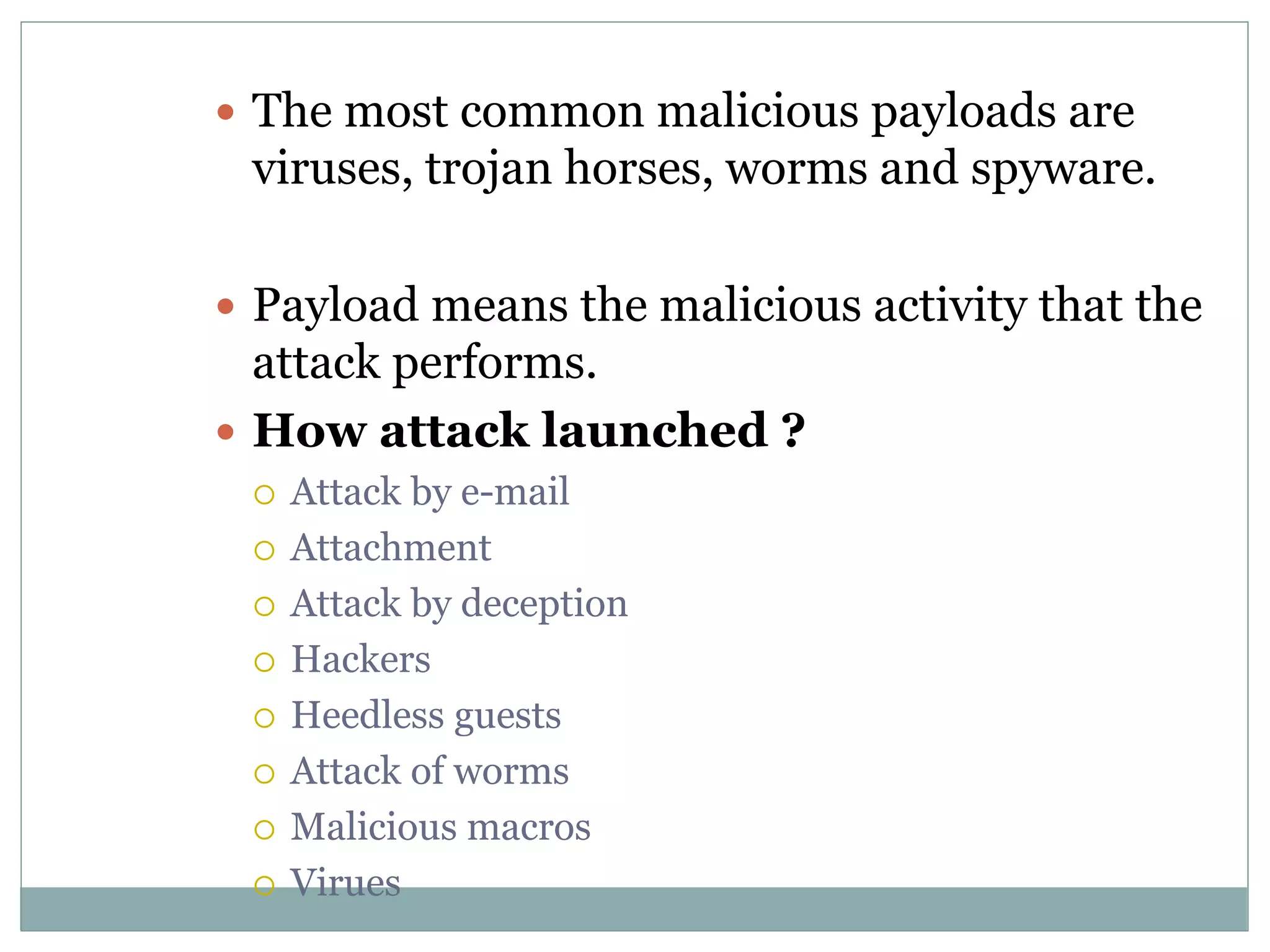
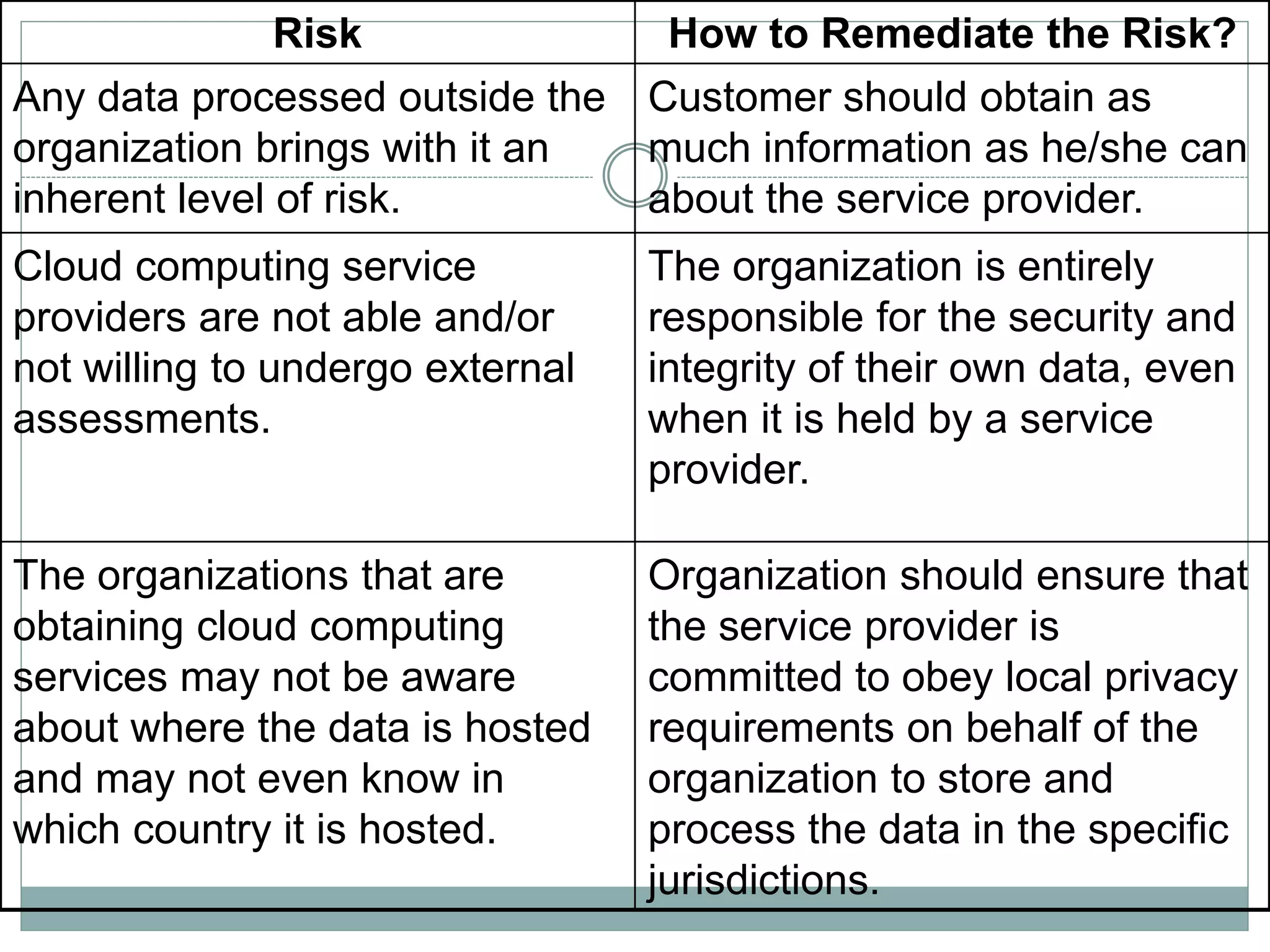
The document details various aspects of cybercrime and cybersecurity, highlighting the methods and phases criminals use to plan attacks. It discusses different types of cybercriminals (hackers, crackers, phreakers), types of attacks (active vs passive), and categorization of social engineering tactics. Additionally, it emphasizes security risks in cybercafes and cloud computing, providing security tips and addressing the implications of botnets.