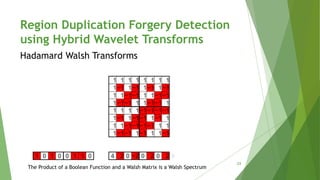
This document discusses techniques for detecting digital image forgeries. It begins by defining different types of forgeries such as image retouching, splicing, and cloning. It then discusses mechanisms for forgery detection, distinguishing between active methods that embed hidden information in images and passive methods that analyze image traces. A key technique presented is using rotation angle estimation to detect cloned regions, with details on calculating variance to determine the rotation angle. The document concludes by presenting an algorithm for region duplication detection using hybrid wavelet transforms like DCT, Walsh, and Hadamard transforms.











![𝑉𝑎𝑟 𝑋 = 𝐸[ 𝑋 − 𝜇 2
]
𝑉𝑎𝑟 𝑎𝑋 + 𝑏𝑌 = 𝑎2 𝑉𝑎𝑟 𝑋 + 𝑏2 𝑉𝑎𝑟(𝑌)
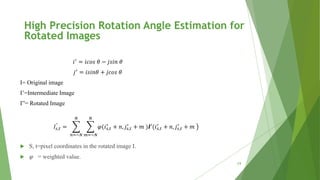
𝐼𝑠,𝑡
"
=
𝑛=−𝑁
𝑁
𝑚=−𝑁
𝑁
𝜑(𝑖 𝑠,𝑡
′
+ 𝑛, 𝑗𝑠,𝑡
′
+ 𝑚 )𝑰′(𝑖 𝑠,𝑡
′
+ 𝑛, 𝑗𝑠,𝑡
′
+ 𝑚
For a single pixel, we have:
𝐼𝑠,𝑡
"
≈
𝑛=0
1
𝑚=0
1
𝜑(𝑖 𝑠,𝑡
′
+ 𝑛, 𝑗𝑠,𝑡
′
+ 𝑚 )𝑰′(𝑖 𝑠,𝑡
′
+ 𝑛, 𝑗𝑠,𝑡
′
+ 𝑚
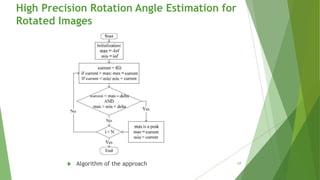
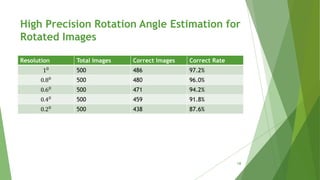
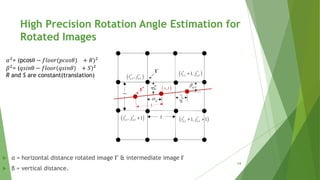
High Precision Rotation Angle Estimation for
Rotated Images
15](https://image.slidesharecdn.com/digitalimageforgerydetection-151101142154-lva1-app6892/85/Digital-image-forgery-detection-15-320.jpg)
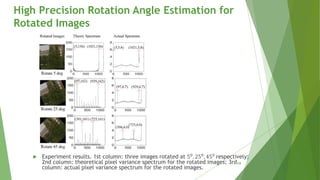
![ Plot of horizontal distance vector and
its spectrum at 𝜃 = 300.
Plot of peak frequency of distance vector
𝛼2
against all 𝜃 𝜖 [00
− 450
]. Frequency is
normalized to [0,1].
High Precision Rotation Angle Estimation for
Rotated Images
16](https://image.slidesharecdn.com/digitalimageforgerydetection-151101142154-lva1-app6892/85/Digital-image-forgery-detection-16-320.jpg)