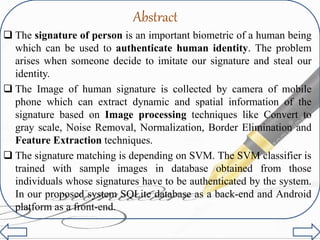
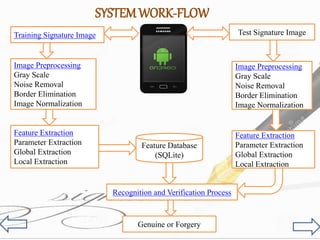
This document presents a system for signature verification using image processing techniques to combat identity theft through forgery. The method involves capturing signature images via a mobile camera, applying preprocessing and feature extraction, and using SVM classifiers for authentication, with SQLite as the database backend. It discusses the workflow, software and hardware requirements, and potential applications, while also acknowledging limitations in matching accuracy.


















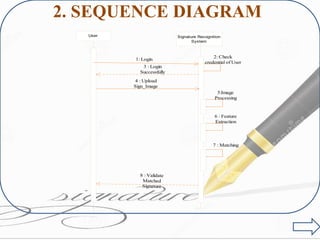
![3. ACTIVITY DIAGRAM
Login
Select Image
Login Failed
Image Processing
[From]
[From]
Camera
Gallery
I) For Login:-](https://image.slidesharecdn.com/finalprojectpresenetation8thsem-160628064957/85/Fraud-Detection-Using-Signature-Recognition-23-320.jpg)














![REFERENCES
[1] Ashish Dhawan, Aditi R. Ganesan, “Handwritten Signature Verification”,
The University of Wisconsin.
[2] Brooks, F. (1995) The Mythical Man Month, Addison-Wesley.
[3] Dr. S. Adebayo Daramola, Prof. T. Samuel Ibiyemi, “Offline Signature Using Hidden
Markov Model(HMM)”, International Journal of Computer Application, Nigeria,
November-2010.
[4] K.A. Vala, N. P. Joshi, “A Survey on Offline Signature Recognition and Verification
Schemes”, International Journal of Advanced Research in Electrical, Electronics and
Instrumentation Engineering, Gujarat, India, March-2014.
[5] Madhuri Yadav, Alok Kumar, Tushar Patnaik, Bhupendra Kumar, “A Survey on Offline
Signature Verification”, International Journal of Engineering and Innovative Technology
(IJEIT), January-2013.](https://image.slidesharecdn.com/finalprojectpresenetation8thsem-160628064957/85/Fraud-Detection-Using-Signature-Recognition-39-320.jpg)
