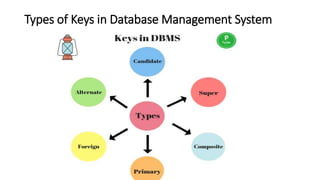
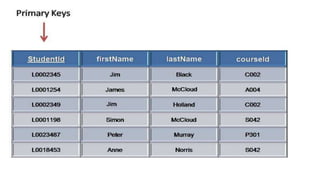
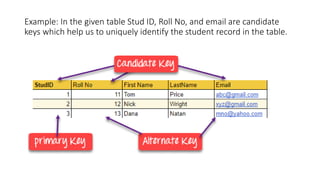
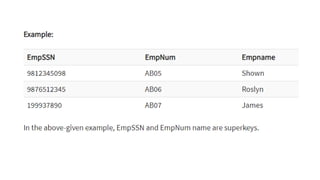
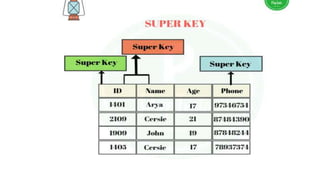
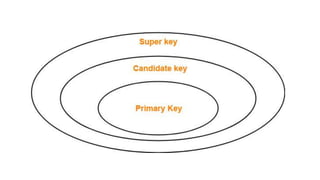
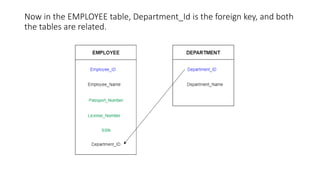
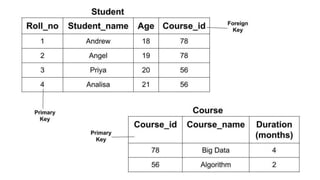
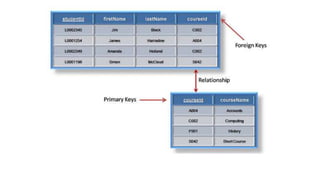
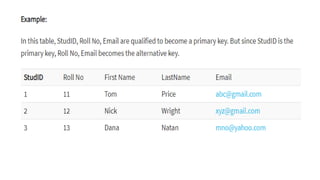
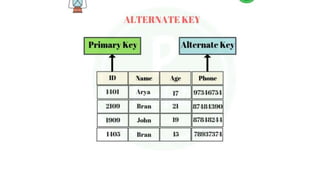
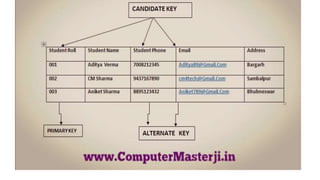
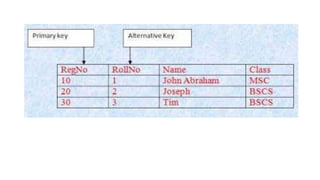
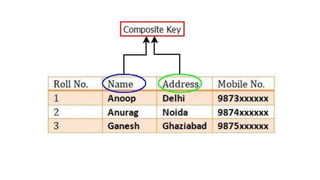
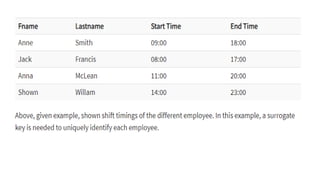
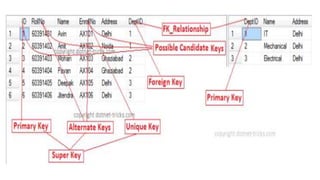
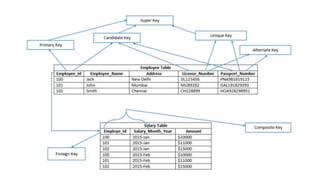
The document discusses different types of keys used in database management systems. It defines primary keys as columns that uniquely identify rows in a table and cannot contain null values. It also describes candidate keys, super keys, foreign keys, alternate keys, composite keys, and surrogate keys. The key types allow tables to be linked together and ensure uniqueness and integrity of data in the tables.