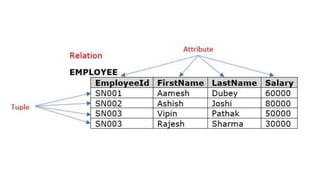
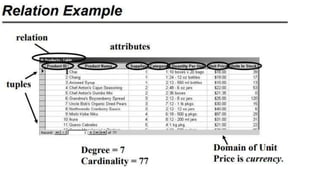
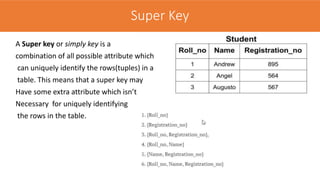
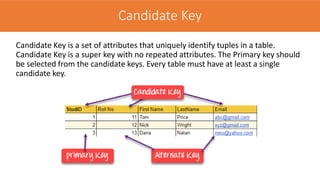
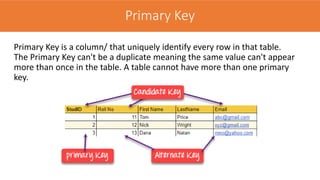
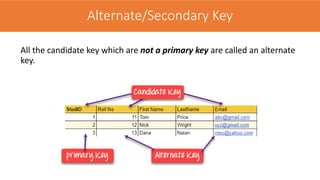
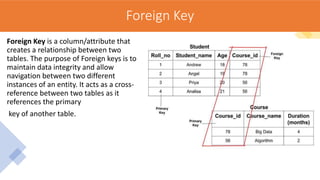
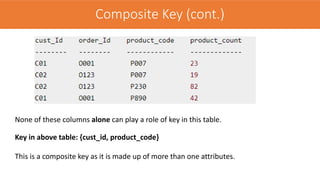
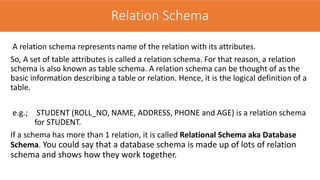
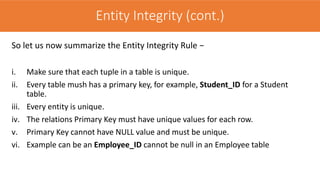
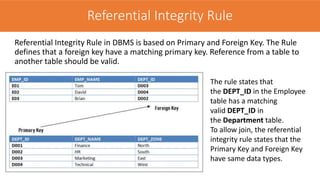
The document discusses the key concepts of the relational model and relational databases. It defines relations (tables) and their components like attributes, tuples, domains, and keys. It explains the properties of relations including distinct relation names, single values per cell, distinct attribute names, and domains. It describes the different types of keys like super keys, candidate keys, primary keys, foreign keys, and composite keys. It also covers integrity rules including entity integrity which requires each table to have a unique primary key, and referential integrity which requires foreign keys to match the primary keys in other tables they reference.