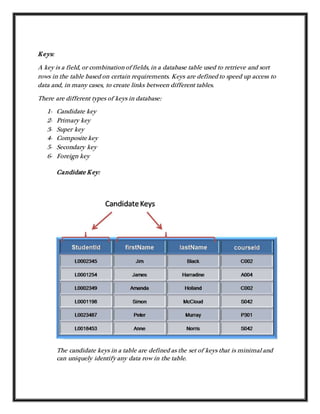
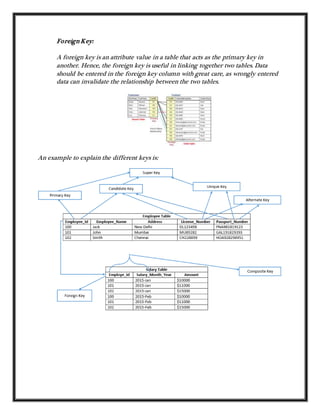
The document discusses different types of keys used in database tables. It defines keys as fields that retrieve and sort table rows based on requirements. The main types of keys discussed are candidate keys, primary keys, super keys, composite keys, secondary keys, and foreign keys. It provides examples of each key type and their properties, such as candidate keys uniquely identifying rows, primary keys being selected from candidate keys, and foreign keys linking tables by matching primary keys.