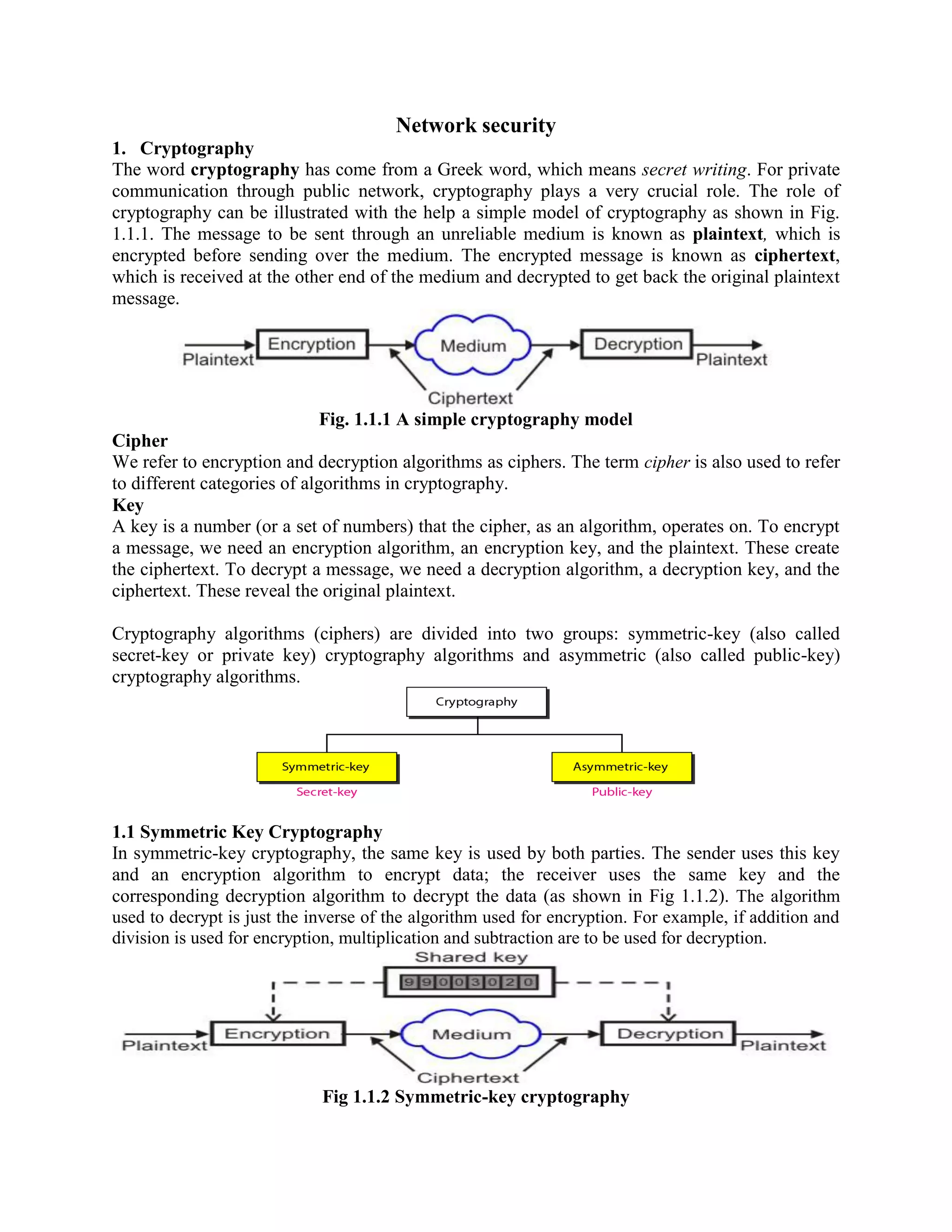
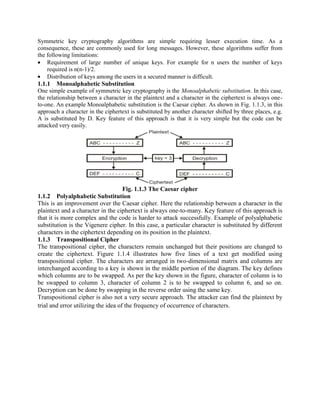
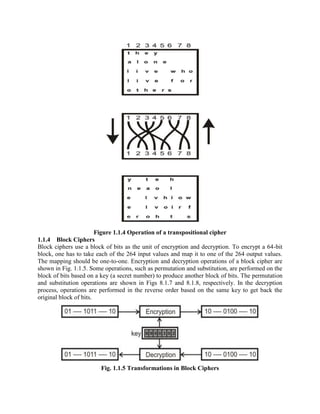
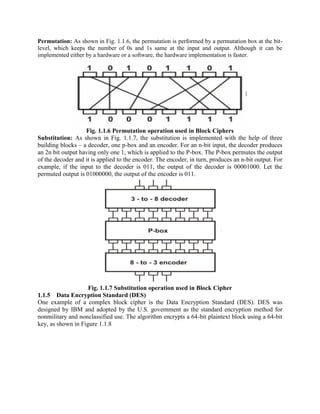
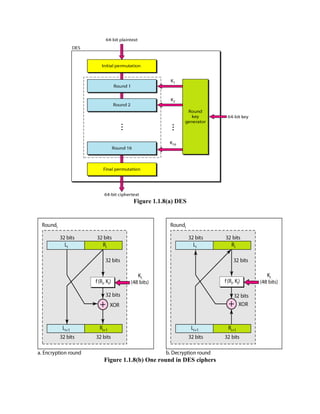
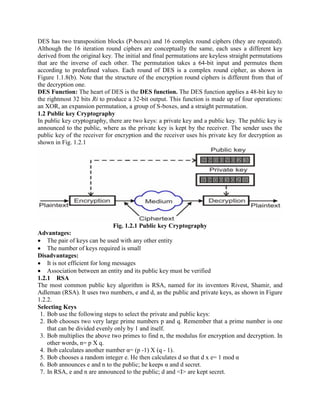
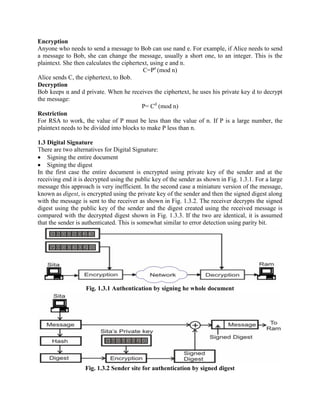
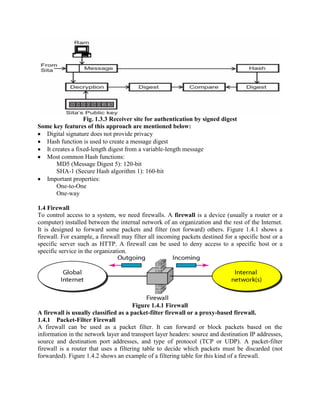
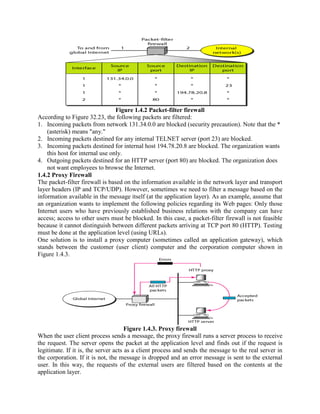
This document discusses various topics in network security including cryptography, symmetric and asymmetric encryption algorithms, digital signatures, and firewalls. It provides detailed explanations and examples of symmetric key algorithms like monoalphabetic and polyalphabetic substitution ciphers, transpositional ciphers, and block ciphers like DES. It also covers asymmetric key algorithms like RSA and their use for encryption and digital signatures. Finally, it describes packet filter and proxy based firewalls and how they can be used to control network access.