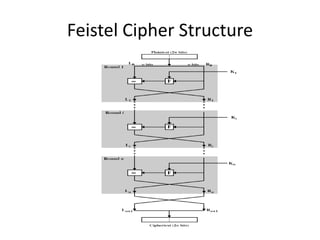
The document discusses encryption techniques, primarily focusing on the one-time pad, which is provably secure when used correctly with a random key only known to the sender and receiver. It also covers historical cryptographic methods like the Zimmerman telegram and introduces modern block ciphers, particularly the Feistel cipher structure, which allows for secure and efficient decryption. Additionally, it highlights Claude Shannon's foundational contributions to information theory and cipher design.