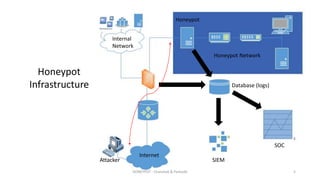
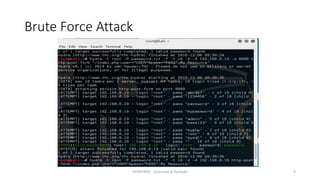
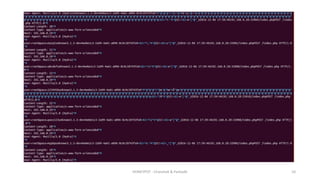
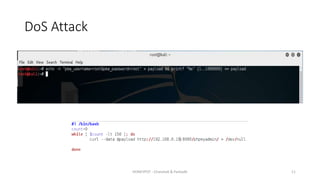
The document discusses honeypots as decoy servers used to gather information and enhance security by resembling real systems. It outlines the principles of honeypots, various types, and provides a demonstration of attacks on a honeypot, including brute force and denial of service attacks. Different types of honeypots are listed, such as WordPress honeypots and those for other protocols like RDP and SMTP.