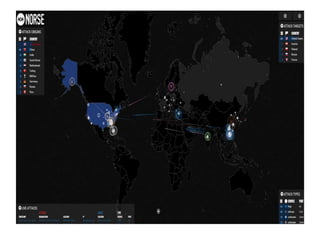
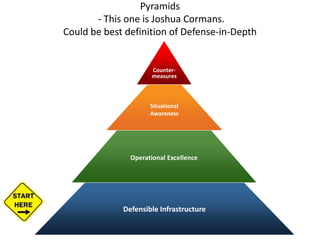
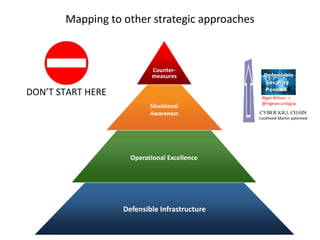
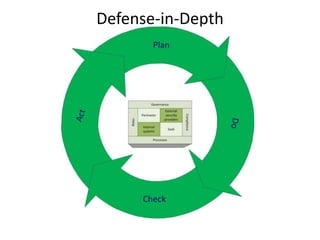
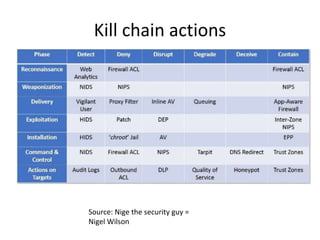
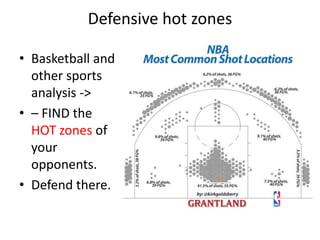
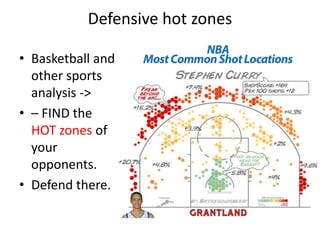
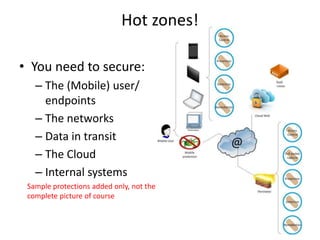
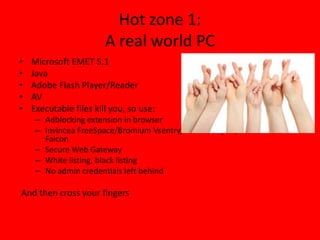
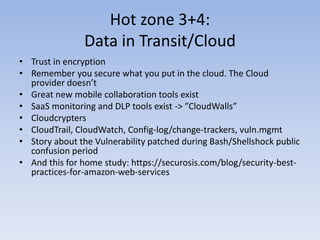
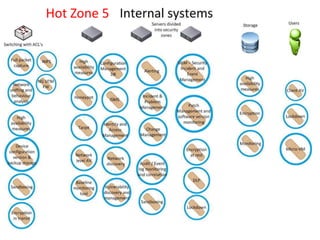
Threats from cyber attacks are increasing and becoming more sophisticated. Existing security tools and even next-generation tools are often ineffective at detecting advanced persistent threats. It is an asymmetrical conflict where defenders must focus on fundamentals like training employees, prioritizing security over compliance, and implementing defense-in-depth across endpoints, networks, data in transit, cloud systems, and internal systems to build a more defensible infrastructure and gain situational awareness of attacks. Continuous improvement is needed to counter evolving adversary techniques.