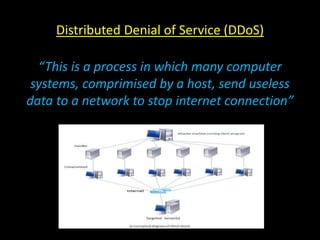
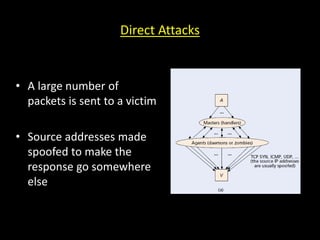
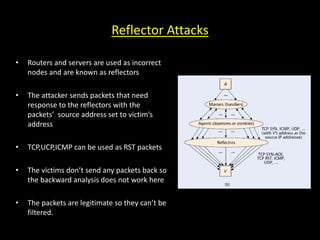
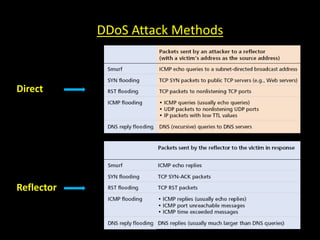
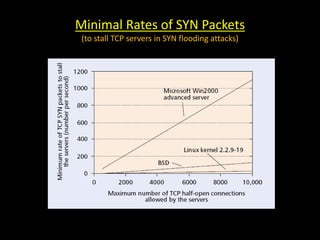
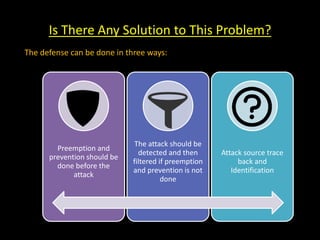
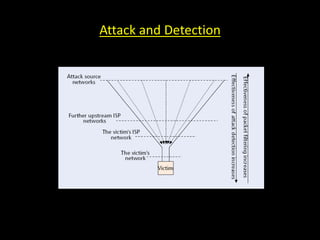
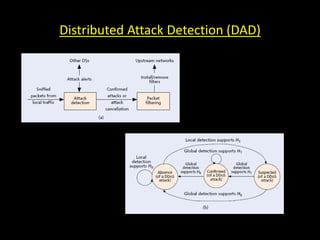
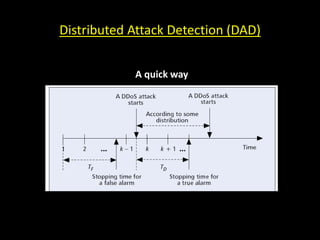
This document discusses distributed denial of service (DDoS) attacks and potential defenses. It describes how DDoS attacks work by flooding a victim with useless traffic from many compromised systems to overwhelm the victim's bandwidth or resources. The document outlines different types of DDoS attacks like direct and reflector attacks. It also discusses challenges with detection and prevention, such as the difficulty of filtering reflected packets or widely deploying packet filters across networks. Promising defense approaches include developing a global firewall infrastructure with distributed detection systems that can identify anomalies and coordinate response. However, effective DDoS defense remains an ongoing challenge.