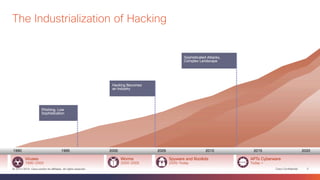
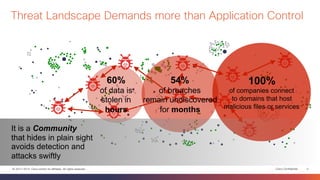
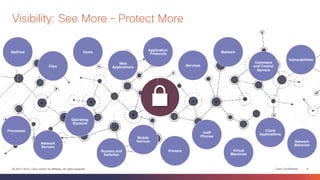
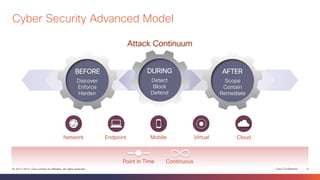
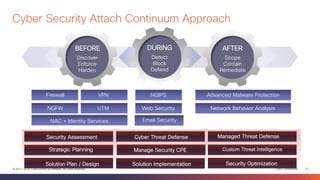
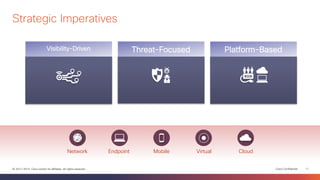
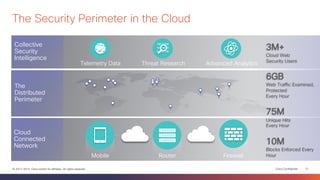
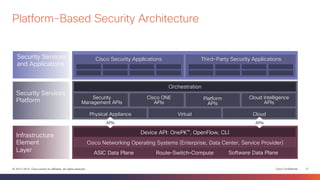
This document discusses the evolution of cyber threats from viruses in the 1990s to advanced persistent threats today. It notes that 100% of companies connect to domains hosting malicious files or services, 54% of breaches go undiscovered for months, and 60% of data is stolen within hours. The document advocates for a holistic approach to cybersecurity called the Global Security Sales Organization that covers the entire attack continuum from before, during, and after attacks. This includes visibility across the network, endpoints, mobile devices, virtual systems, and cloud to detect, block, and defend against threats.