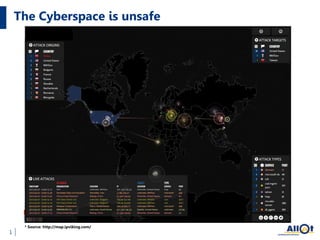
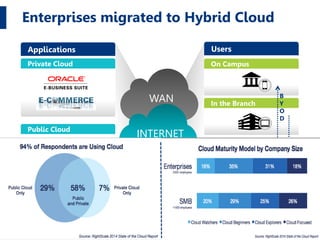
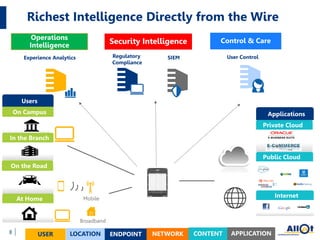
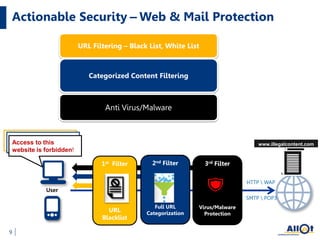
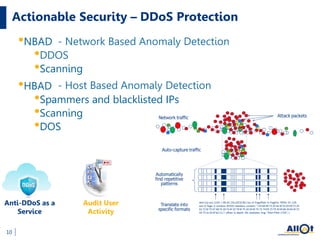
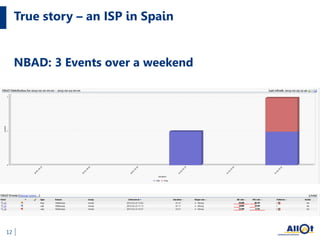
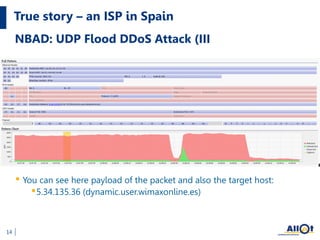
The document discusses the increasing threats to cybersecurity, such as DDoS attacks and cyber warfare, highlighting incidents involving groups like Lizard Squad and the implications of such attacks. It emphasizes the importance of securing infrastructure in a hybrid cloud environment and the emerging trend of 'Security as a Service' to combat these threats. Ultimately, the document advocates for actionable security measures and continuous intelligence for enterprises to navigate the evolving cyber landscape.