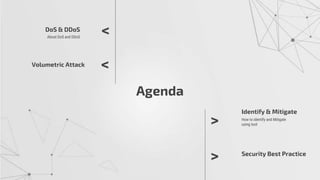
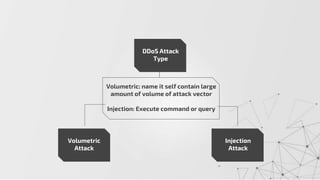
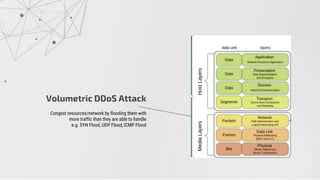
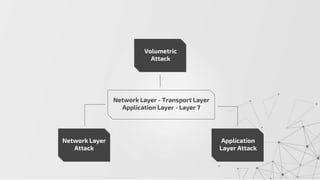
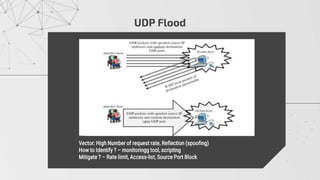
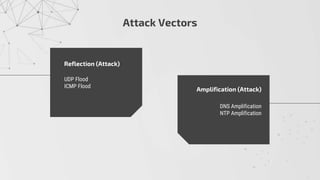
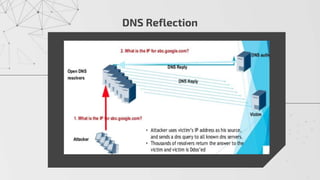
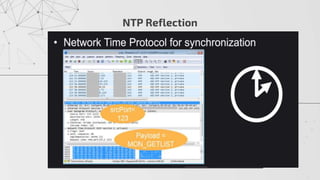
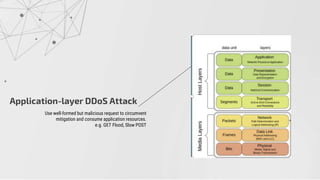
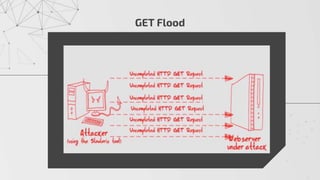
The document discusses methods to identify and mitigate Denial of Service (DoS) and Distributed Denial of Service (DDoS) volumetric attacks, specifically focusing on various attack types such as SYN flood, UDP flood, ICMP flood, and application-layer attacks like GET flood and slow POST. It details identification techniques using monitoring tools and resource utilization, as well as mitigation strategies including rate limiting, load balancing, and scaling resources. Overall, it emphasizes understanding attack vectors and implementing best security practices to protect against these threats.