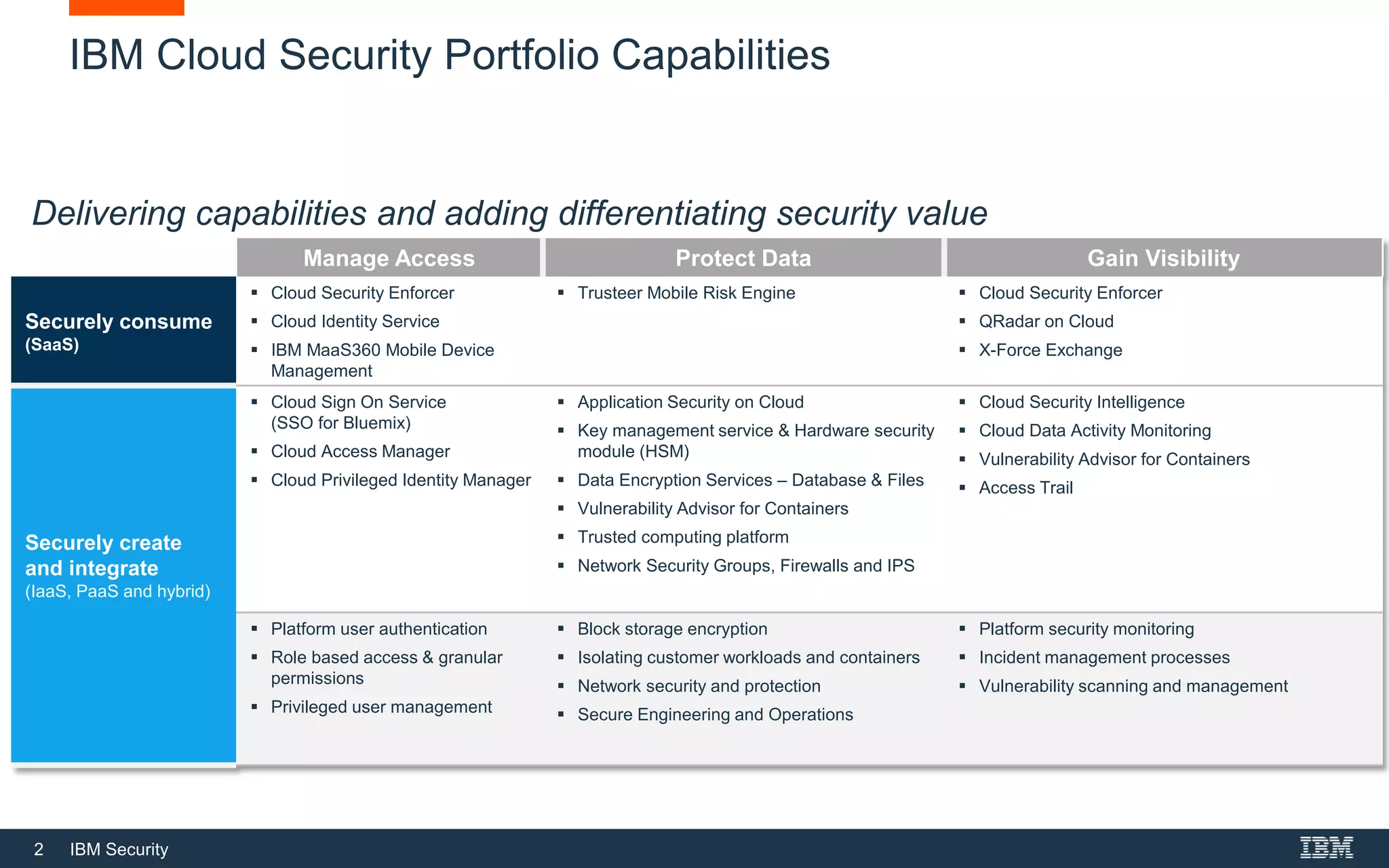
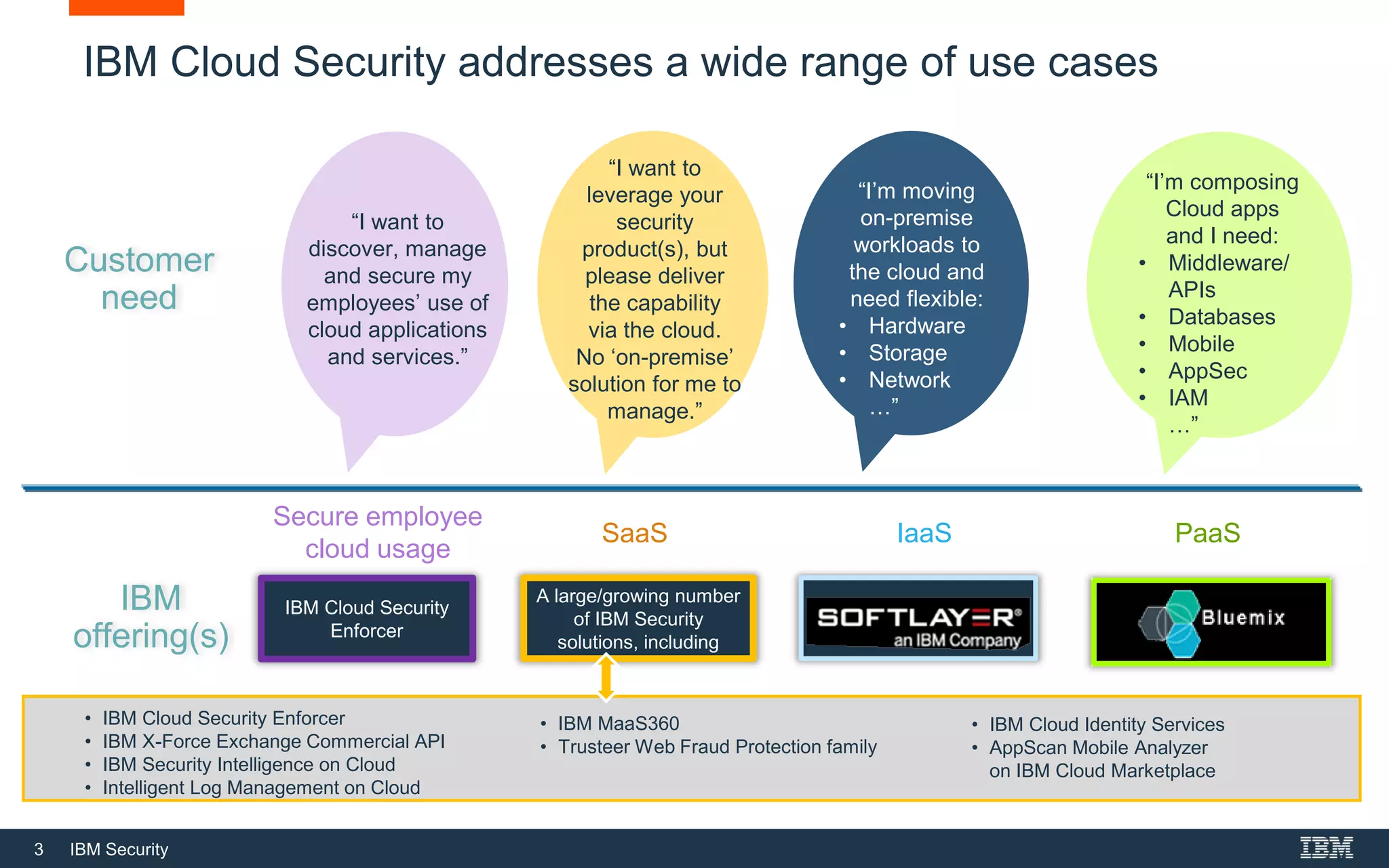
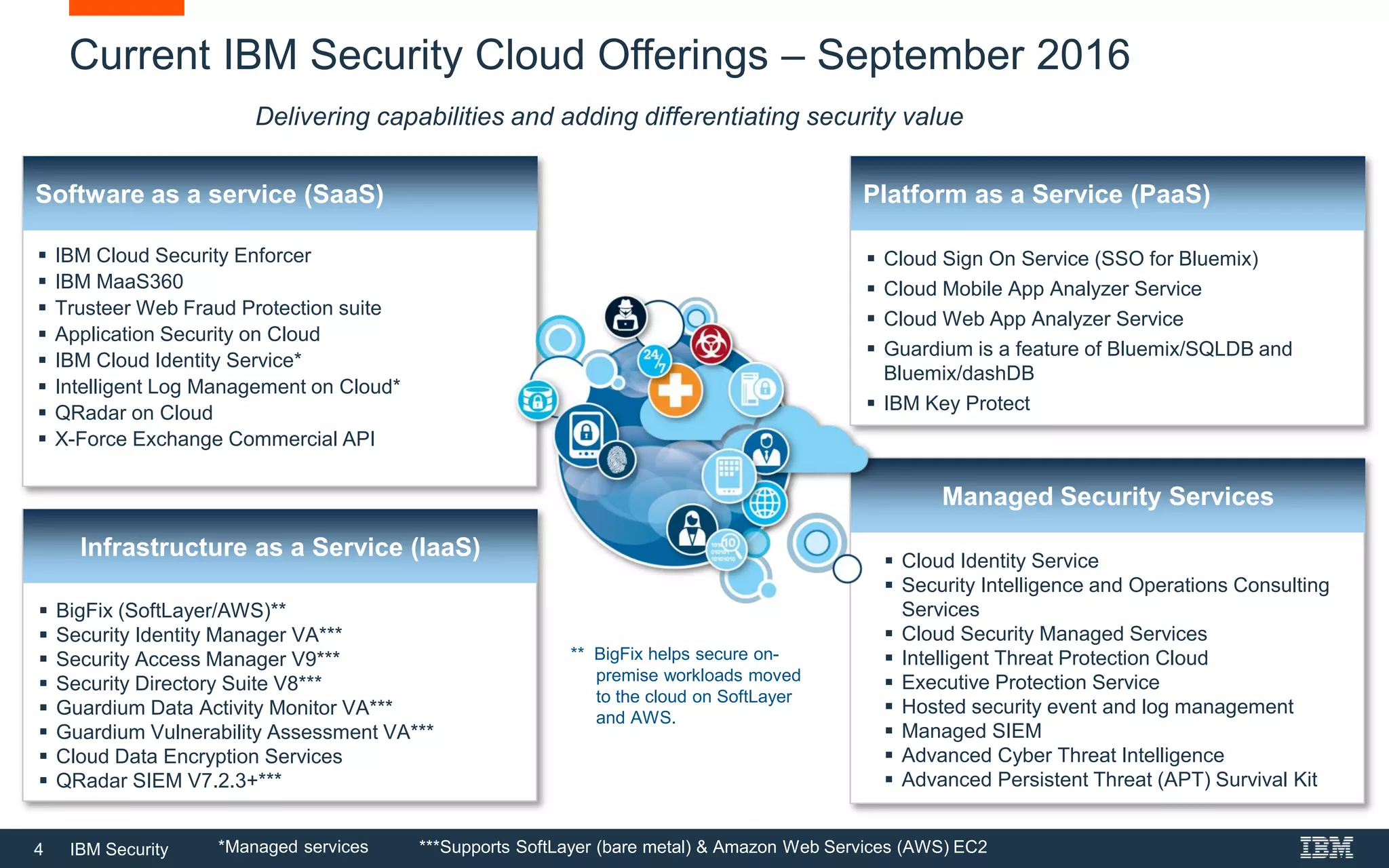
The document provides an overview of IBM's cloud security portfolio, detailing various services and solutions available for SaaS, IaaS, and PaaS environments. It highlights key offerings such as cloud identity services, managed security services, and application security tools designed to protect data and manage access in cloud applications. Additionally, it outlines customer needs related to cloud adoption and the associated security solutions provided by IBM to accommodate these needs.