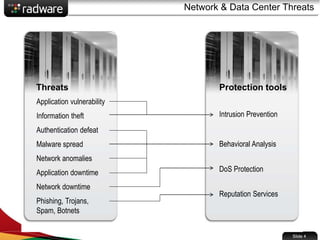
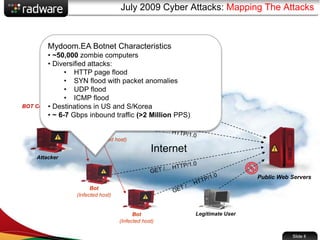
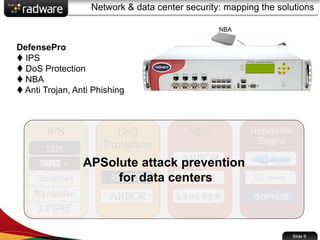
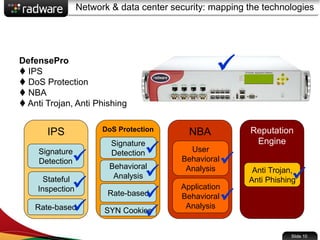
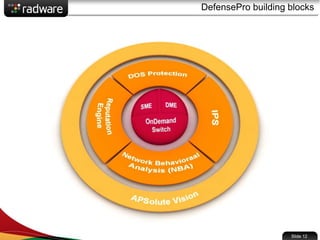
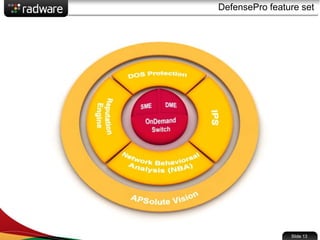
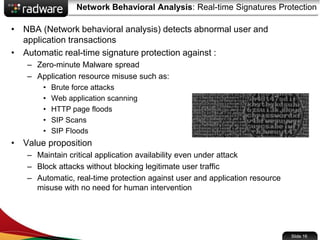
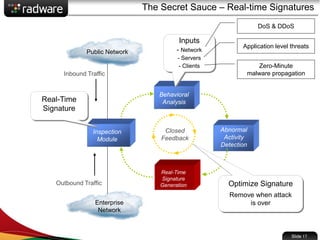
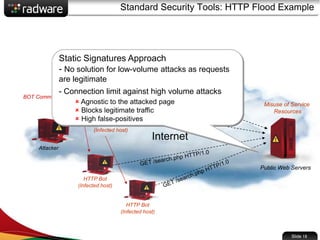
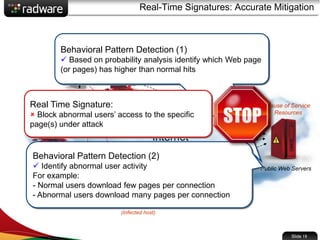
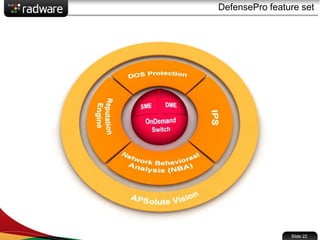
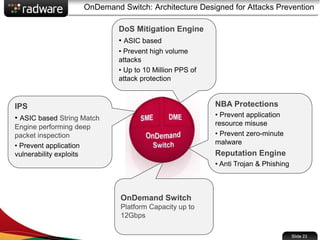
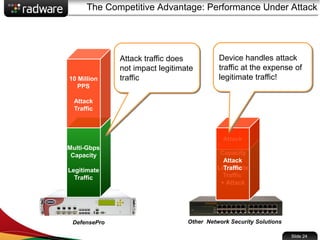
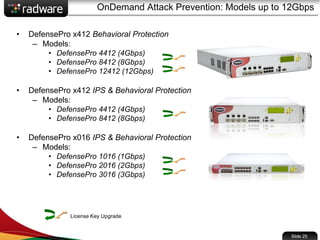
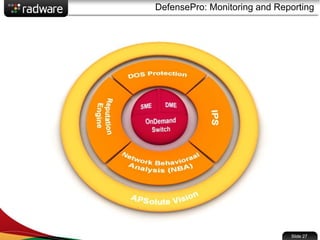
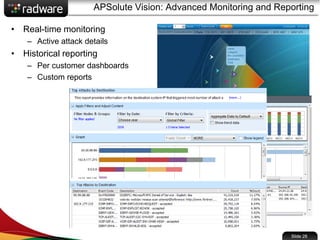
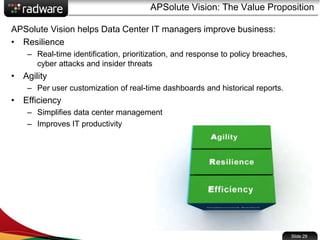
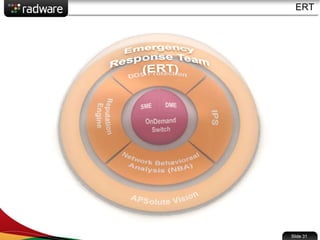
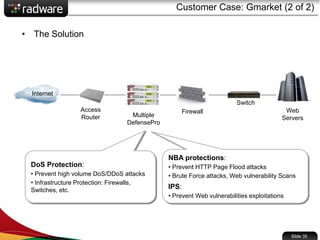
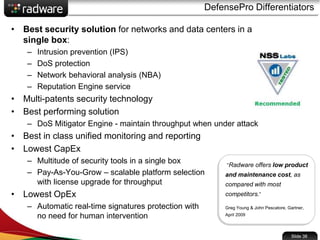
The document presents the capabilities of DefensePro, a real-time attack prevention device designed to protect data centers against various security threats, including DDoS attacks and application vulnerabilities. It outlines key features such as intrusion prevention, behavioral analysis, and a reputation engine, emphasizing its ability to maintain application availability under attack while reducing operational costs. Additionally, it highlights successful case studies and the system's competitive advantages in performance and scalability.