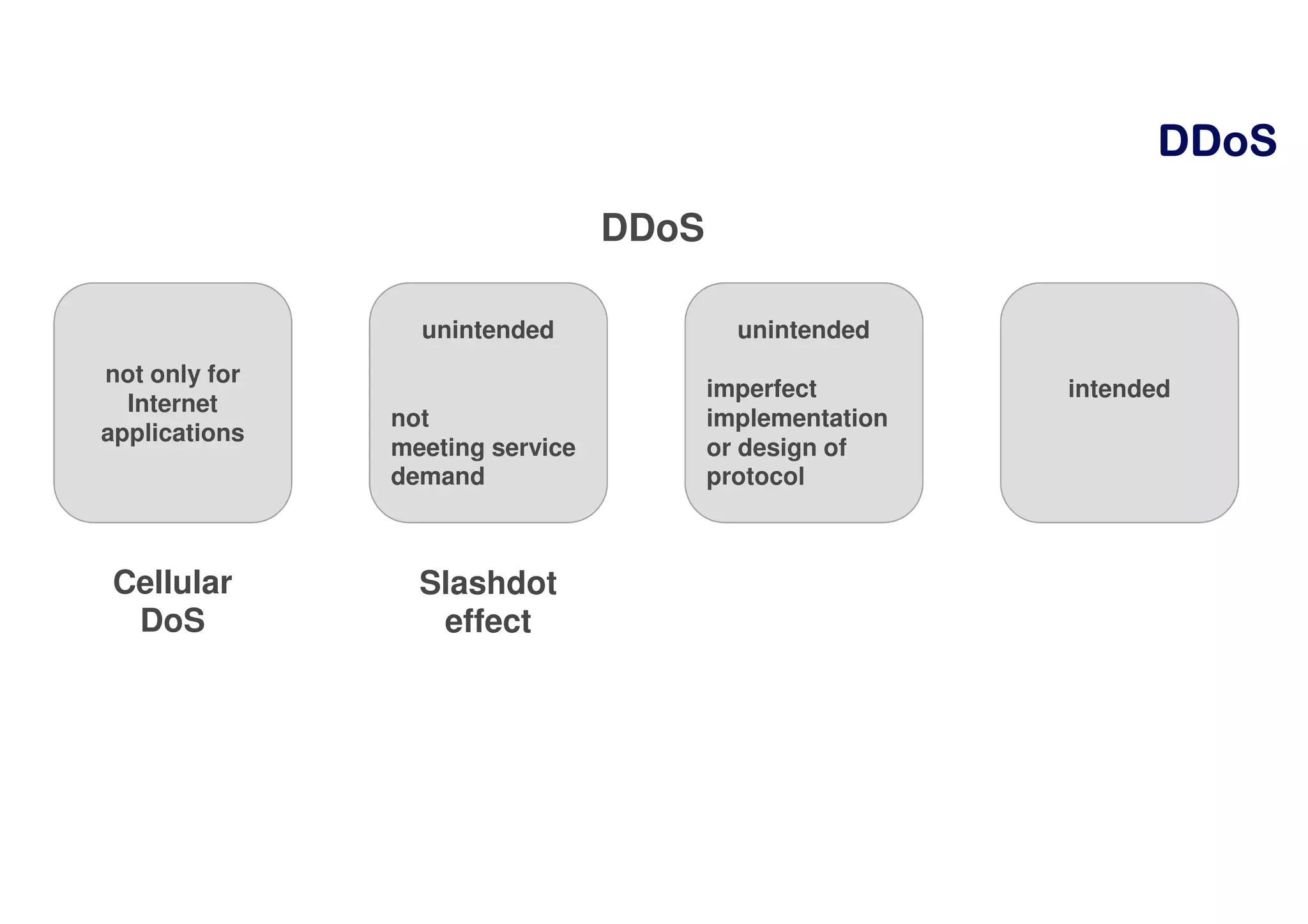
The document discusses distributed denial of service (DDoS) attacks. It begins by defining DDoS and DoS attacks, noting that a DDoS attack involves coordinating multiple parties to overwhelm a server or application with traffic. The document then discusses the scale of DDoS attacks over time, how attacks on the scale of terabits per second can be achieved, and how DDoS attacks have become a business. It also summarizes the impact of the Mirai botnet and techniques for mitigating DDoS attacks through detection methods, split intelligence versus resource constraints, and the lack of built-in accountability on the internet.

![DoSDoSDoSDoS
• a Denial-of-Service attack is one that prevents a [networked] function to
work normally.
• Overwhelming a server with traffic is DoS.
• Remotely exhausting the available memory of an application is DoS.
• It is distributed if there’s coordination of multiple parties to develop the
attack.](https://image.slidesharecdn.com/bcuddosslideshare-170911091145/75/DDoS-Attacks-3-2048.jpg)