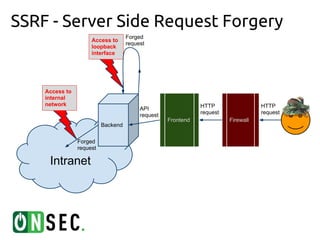
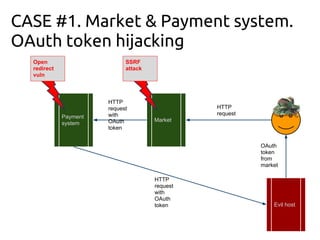
This document discusses server-side request forgery (SSRF) exploitation. It provides examples of how SSRF can be used to access internal networks and bypass authentication by forging requests from the vulnerable server. Specific cases described include exploiting OAuth token hijacking, memcached exploitation using protocol smuggling, and exploiting vulnerabilities in libraries like TCPDF, LWP, and Postgres that enable SSRF. The document encourages finding creative ways to leverage SSRF and related vulnerabilities like open redirects, XML external entities, and SQL injection to compromise hosts and internal services.











![Protocol smuggling
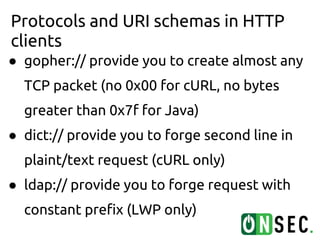
● When you say "GET / HTTP/1.1", what hears
a service?
● When you receive data by one of
prehistoric protocols what TCP packet you
send?
● When you say "bla[valid packet]bla", what
hears a service?](https://image.slidesharecdn.com/ssrfworkshop1-121208044517-phpapp02/85/SSRF-workshop-14-320.jpg)