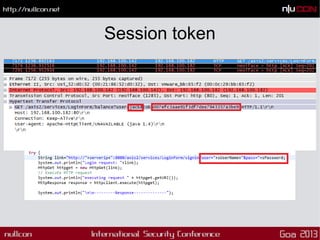
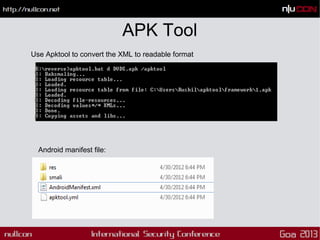
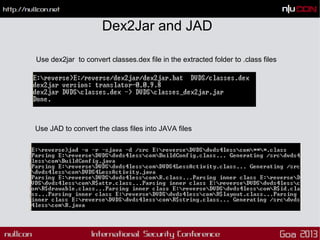
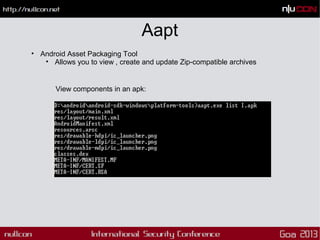
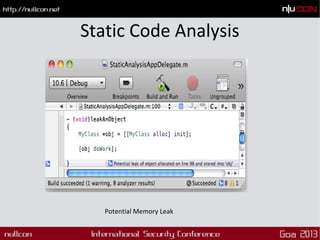
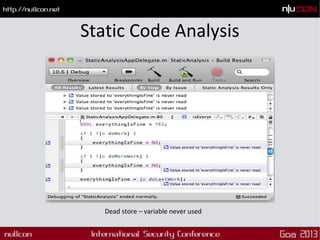
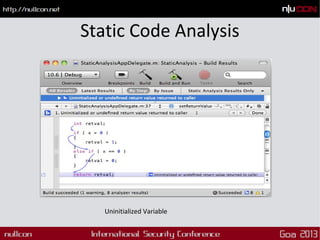
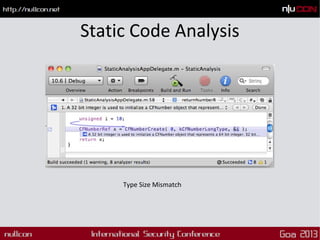
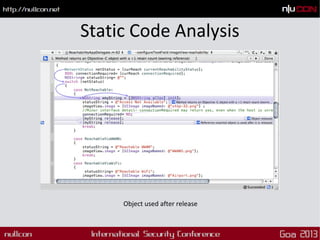
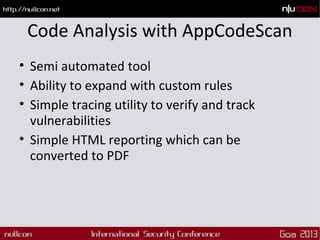
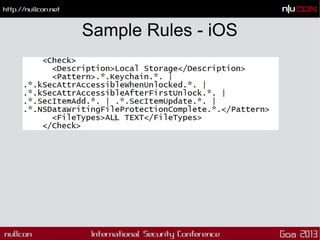
This document discusses mobile code mining for discovery and exploits. It introduces the speaker, Hemil Shah, and provides an overview of mobile infrastructure, apps, and changes in the mobile environment compared to web. It then discusses several mobile attacks including insecure storage, insecure network communication, UI impersonation, activity monitoring, and system modification. It also covers decompiling Android apps and analyzing app code for security issues.


![Enterprise Technology Trend
2007. Web services would rocket from $1.6
billion in 2004 to $34 billion. [IDC]
2008. Web Services or Service-Oriented
Architecture (SOA) would surge ahead.
[Gartner]
2009. Enterprise 2.0 in action and penetrating
deeper into the corporate environment
2010. Flex/HTML5/Cloud/API
2012. HTML5/Mobile era.](https://image.slidesharecdn.com/mobilecodeminingfordiscoveryandexploitsnullcongoa2013-160202074021/85/Mobile-code-mining-for-discovery-and-exploits-nullcongoa2013-3-320.jpg)
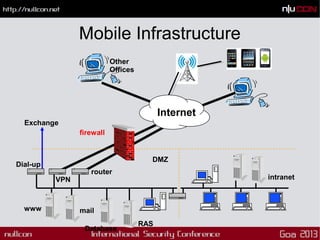
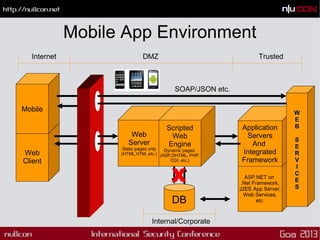

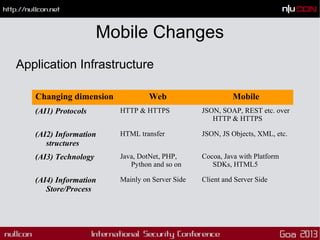
![Mobile Changes
Security Threats
Changing dimension Web Mobile
(T1) Entry points Structured Scattered and multiple
(T2) Dependencies Limited • Multiple technologies
• Information sources
• Protocols
(T3) Vulnerabilities Server side [Typical
injections]
• Web services [Payloads]
• Client side [Local Storage]
(T4) Exploitation Server side exploitation Both server and client side
exploitation](https://image.slidesharecdn.com/mobilecodeminingfordiscoveryandexploitsnullcongoa2013-160202074021/85/Mobile-code-mining-for-discovery-and-exploits-nullcongoa2013-9-320.jpg)