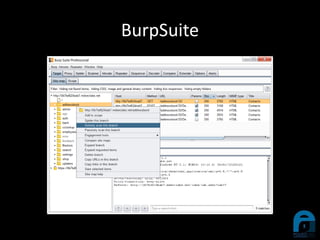
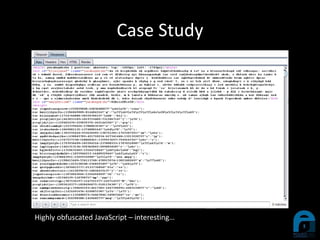
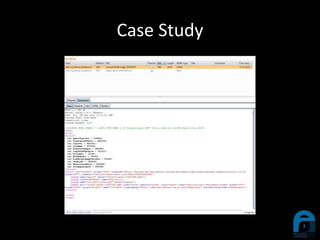
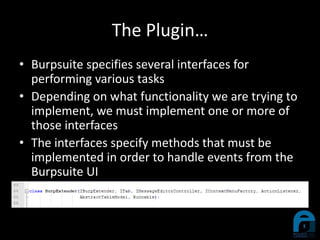
The document discusses the integration of YARA with Burp Suite, highlighting Ian Duffy's background and the use of these tools for cybersecurity. A case study illustrates how a compromised website was investigated using Burp Suite to identify malicious content through scanning. Future enhancements for the plugin are proposed, including live YARA scanning and persistence for configurations.