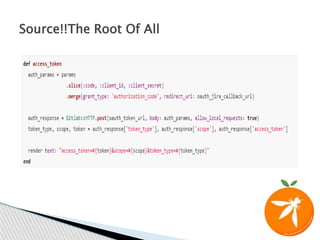
The document discusses Server Side Request Forgery (SSRF), including what it is, different types (blind and basic), ways to exploit it like bypassing filters and chaining vulnerabilities, tools that can be used for detection, and two case studies of SSRF vulnerabilities found in the wild. The first case involves using an SSRF to retrieve internal data and then storing malicious HTML in a generated PDF. The second case was an unauthenticated blind SSRF in a Jira OAuth authorization controller that was exploited through a malicious Host header.










![ Bypassing the blacklisting
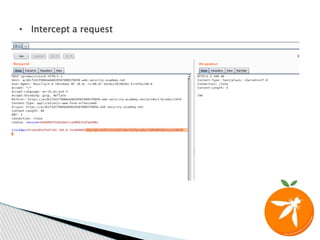
1)Redirection to blacklist address.
<?php header(“location: http://127.0.0.1”); ?>
2)Use of different encodings.
127.0.0.1—(HEX)--->7f.00.00.01
127.0.0.1—(Oct)--->0177.0000.0000.0001 (017700000001)
3)Use of escaping 0’s.
127.0.0.1 --->127.1
4)Using IPV6
http://127.0.0.1--> http://[::1]/
Breaking The Shield](https://image.slidesharecdn.com/ssrfforbugbounties-200518071759/85/SSRF-For-Bug-Bounties-17-320.jpg)


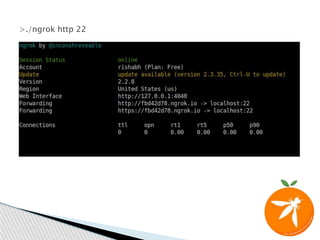



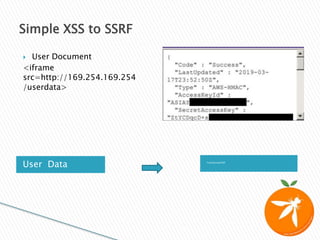
![ Most user input gets sanitized/filtered
We haven’t found an XSS in our target app
But… we are allowed to customize the fonts and styling of the
generated PDF
XSS via escaping <style> tag
</style><iframe src=”http://169.254.169.254/user-
data/[...]”>
Tackling The HTML Renders](https://image.slidesharecdn.com/ssrfforbugbounties-200518071759/85/SSRF-For-Bug-Bounties-26-320.jpg)