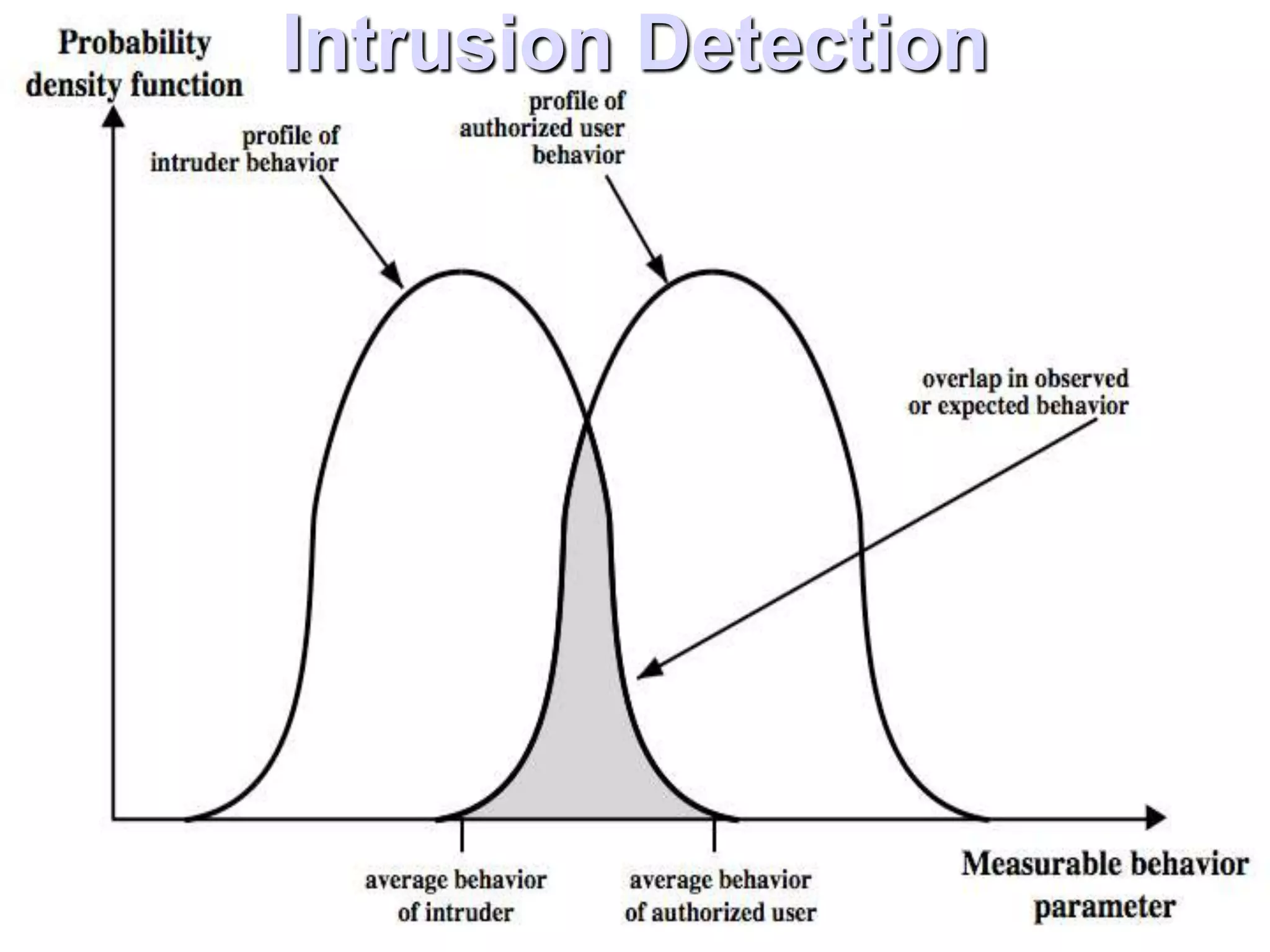
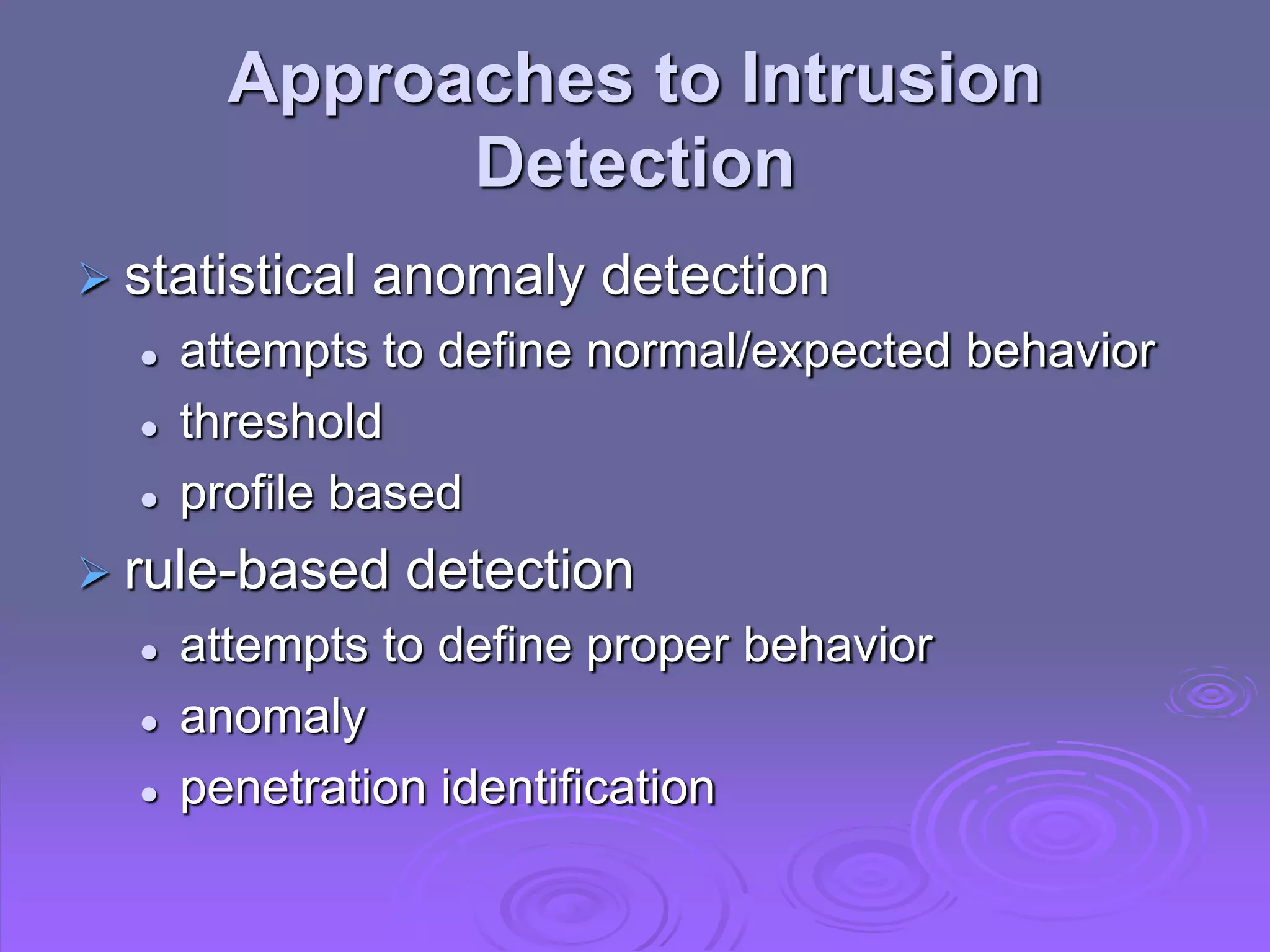
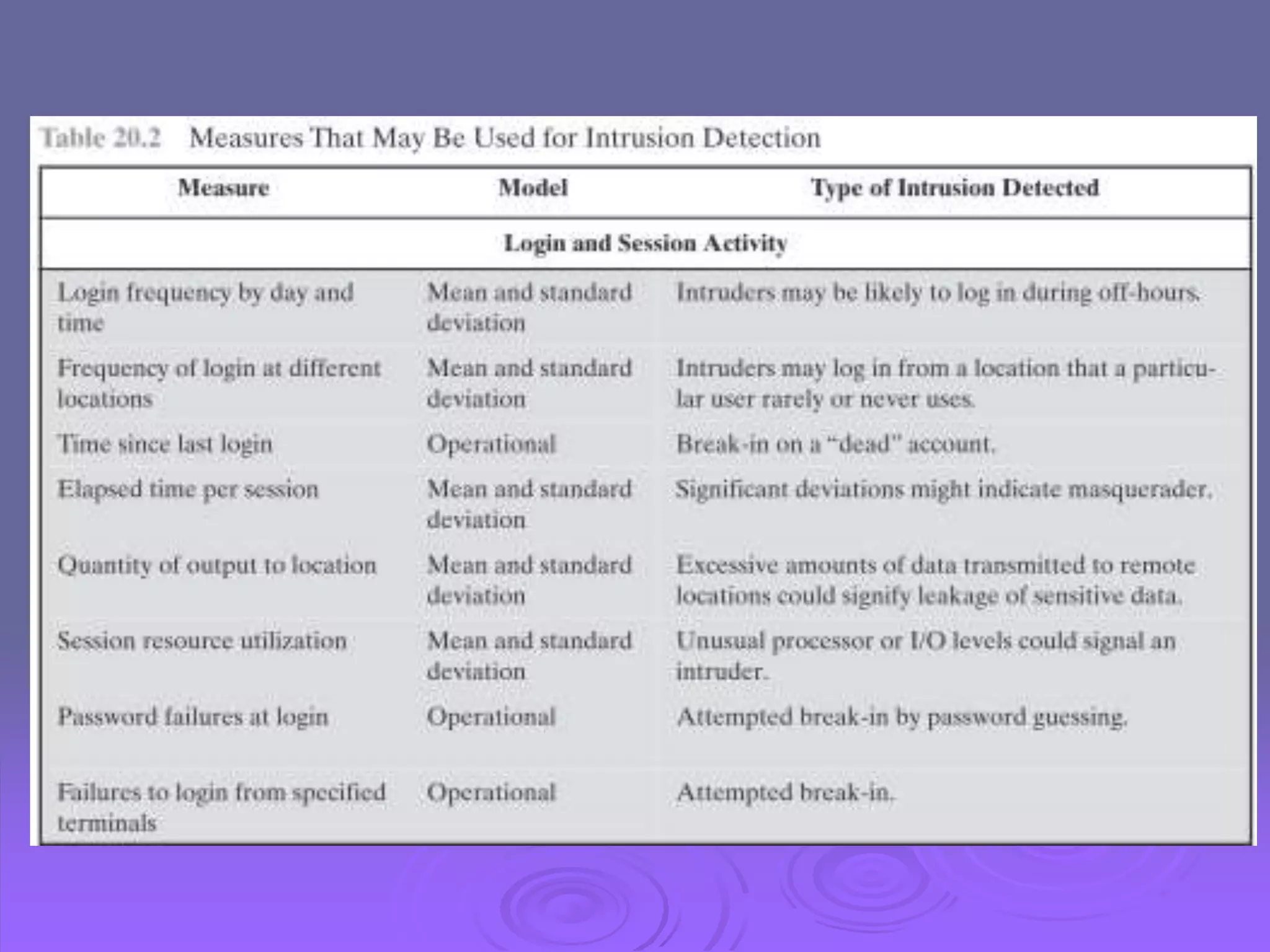
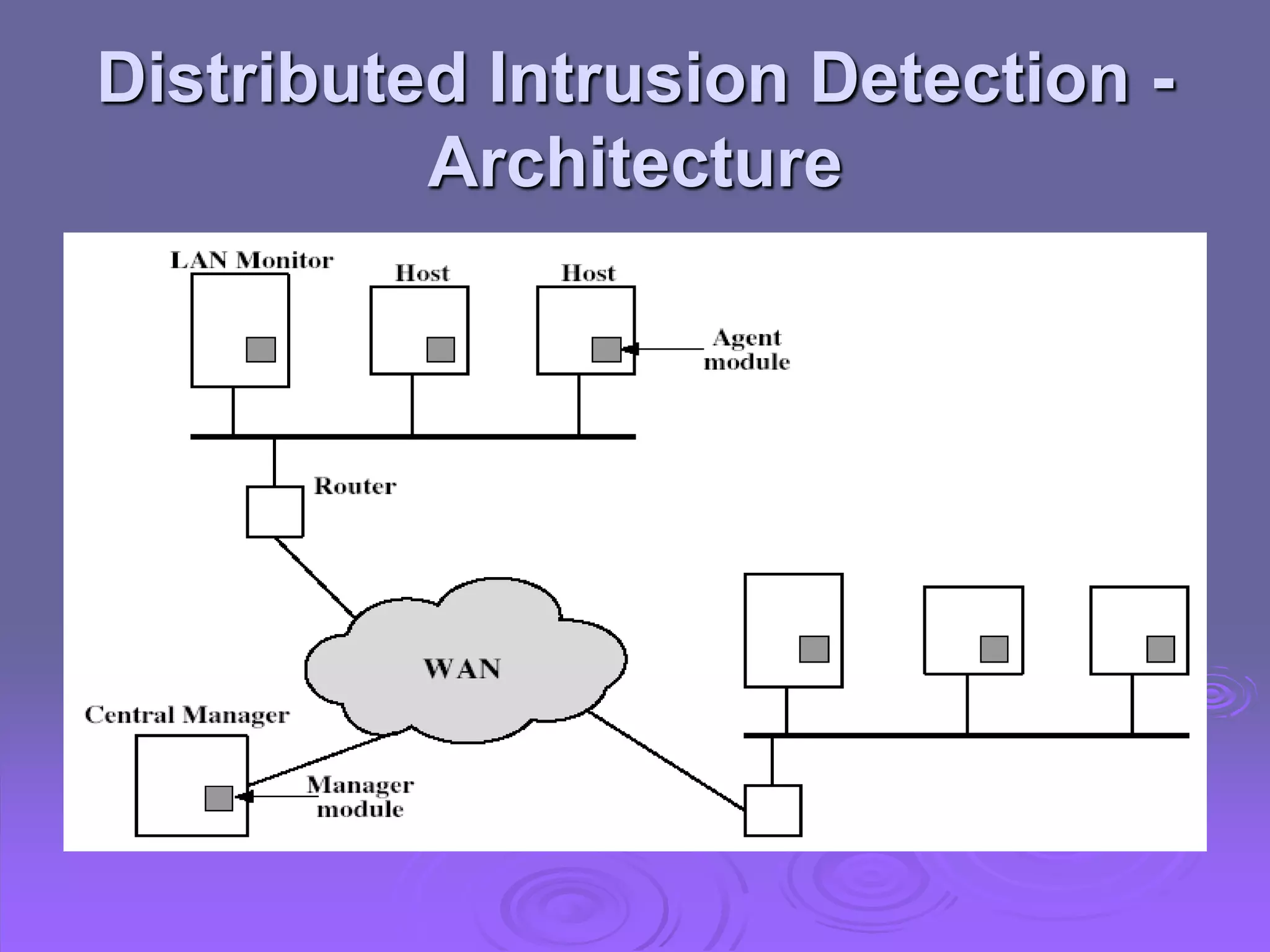
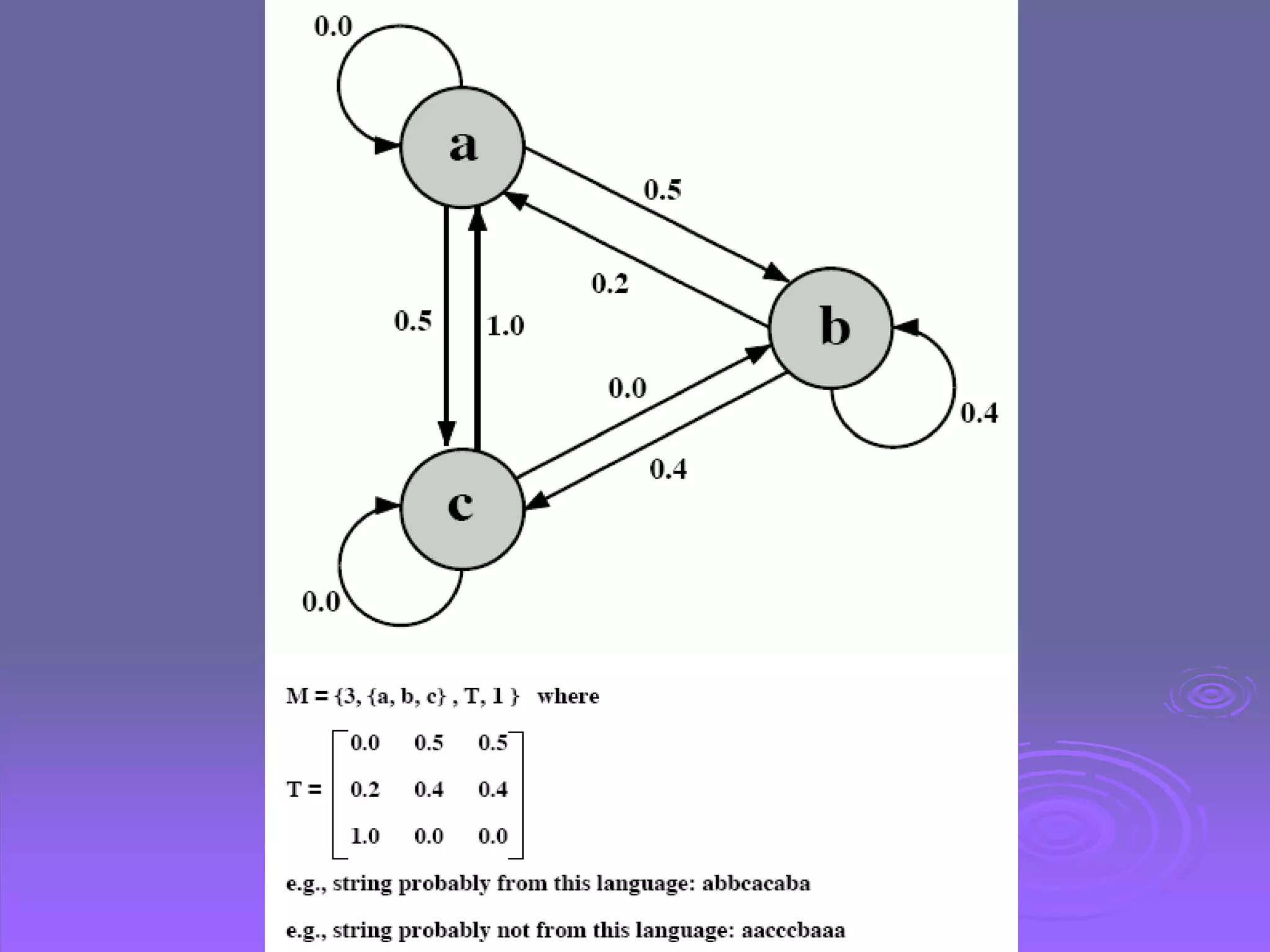
The document discusses intruders, intrusion detection techniques, and password management. It describes classes of intruders including masqueraders, misfeasors, and clandestine users. It covers statistical and rule-based intrusion detection approaches, including analyzing audit records and applying rules to detect anomalies. It also addresses managing passwords through education, computer-generated passwords, reactive password checking, and proactive verification that passwords meet strength requirements.