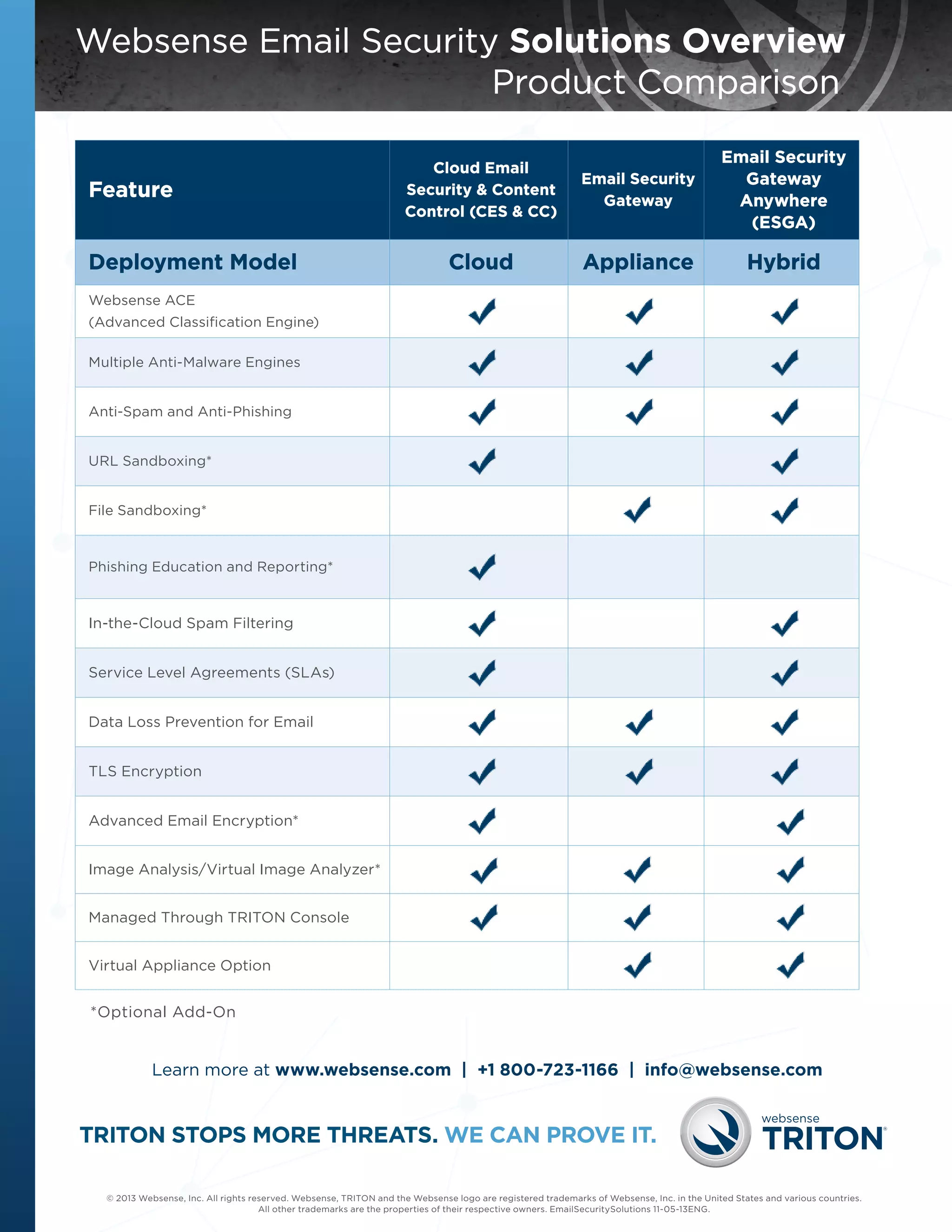
Websense offers several email security solutions to address modern threats. Their solutions leverage the Websense ThreatSeeker Intelligence Cloud and Advanced Classification Engine (ACE) to detect known and unknown malware, spam, and targeted attacks. Key capabilities include gateway threat analysis, point-of-click URL sandboxing, behavioral file sandboxing, and built-in data loss prevention. Websense solutions can be deployed in the cloud, on-premises with appliances, or in a hybrid model.