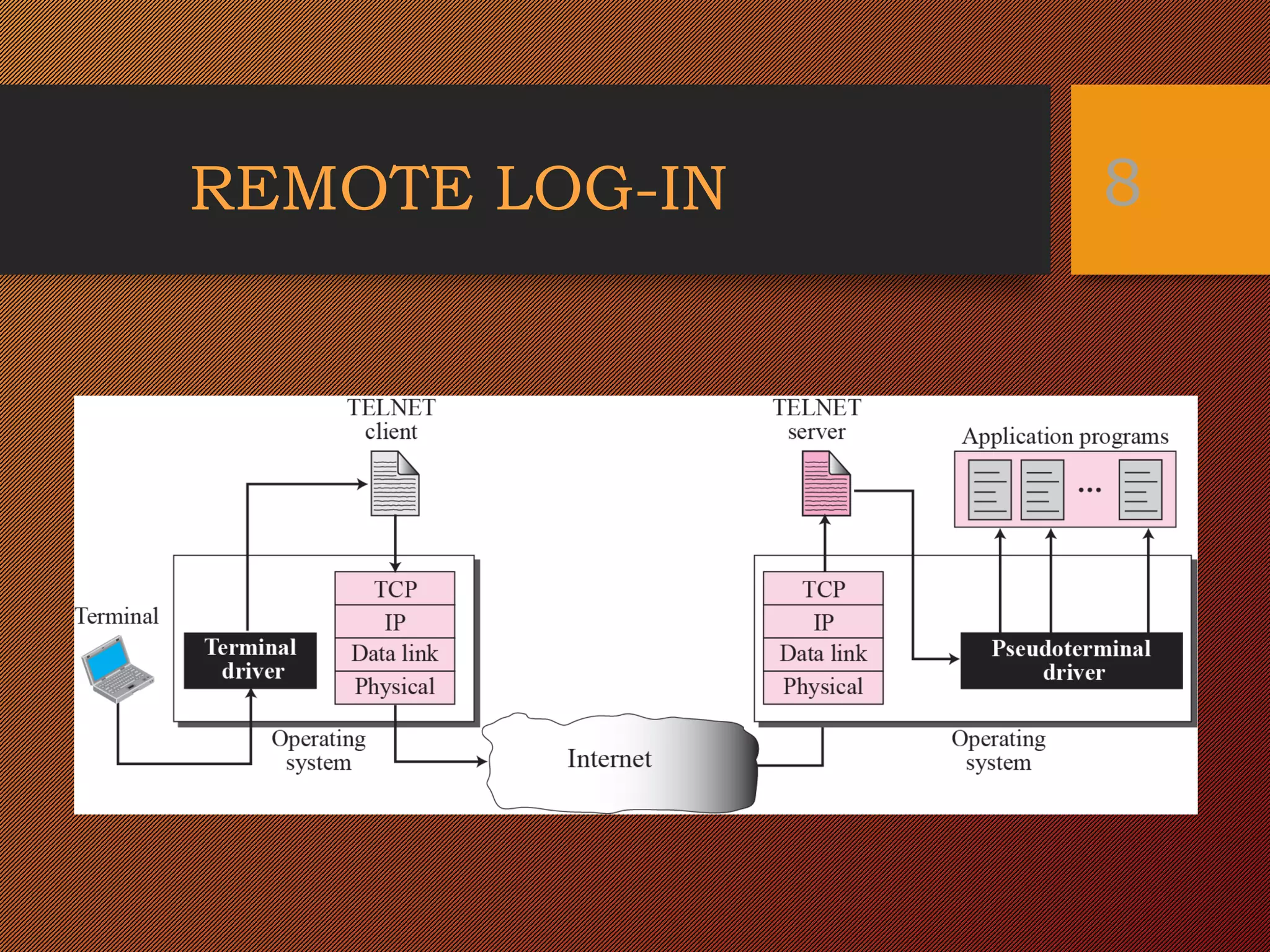
TELNET is a TCP/IP protocol that allows users to connect to remote systems and access services as if their local terminal was connected directly to the remote system. It enables users to log in remotely using their username and password. TELNET uses control characters and option negotiation to translate between the local character set and the character set of the remote system, allowing the connection to function transparently. Common options negotiated are terminal type, echo, and line mode. This document provides details on how TELNET establishes and manages remote connections.