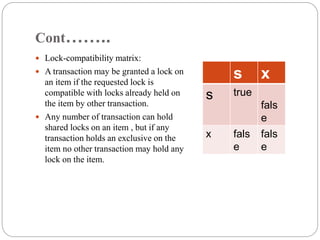
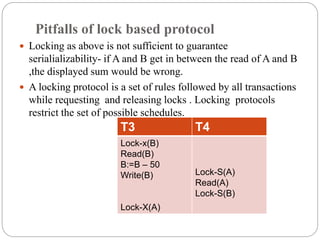
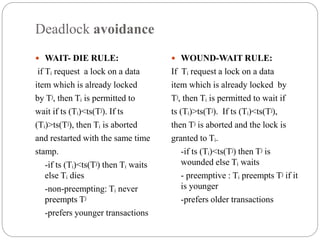
This document provides an overview of concurrency control and two-phase locking protocol. It discusses lock-based concurrency control, two-phase locking protocol, deadlocks, and strategies for handling deadlocks such as deadlock prevention, avoidance, and detection and recovery. The key aspects covered are the lock compatibility matrix, differences between shared and exclusive locks, requirements for serializability under two-phase locking, and the four conditions required for a deadlock.