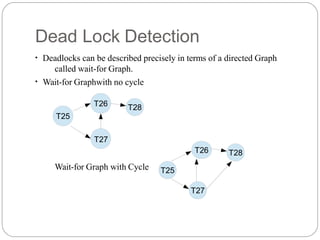
The document discusses deadlocks in database management systems, defining a deadlock state and presenting methods for prevention, detection, and recovery. It outlines key strategies for deadlock prevention, including transaction ordering and timestamp-based techniques such as wait-die and wound-wait schemes. For recovery, it emphasizes rolling back transactions and careful selection of victims to prevent starvation.