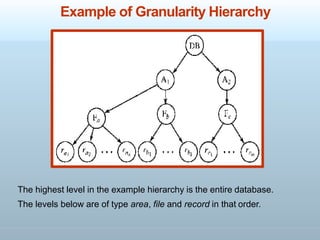
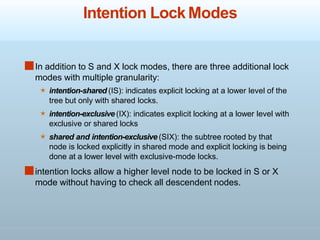
Concurrency control is essential for maintaining the consistency and reliability of transactions by synchronizing operations to avoid issues such as lost updates and dirty reads. It utilizes techniques like locking at multiple granularities to manage access to data, while also addressing deadlocks through prevention and detection methods. Deadlock handling can involve rolling back transactions to resolve conflicts, and care must be taken to avoid starvation where a transaction is repeatedly chosen as a victim.