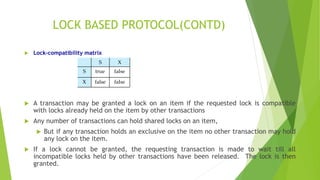
This document discusses lock-based protocols for concurrency control. It describes that locks can be requested in exclusive or shared mode to control concurrent access to data items. A lock compatibility matrix is used to determine if a requested lock is compatible with existing locks held by other transactions. The Two Phase Locking protocol is introduced to ensure conflict serializable schedules by restricting transactions to an growing phase where they only acquire locks and a shrinking phase where they only release locks.