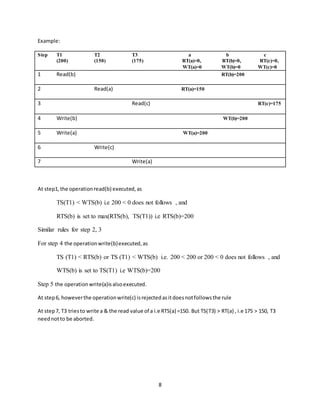
The document discusses various concurrency control techniques used in database management systems to ensure transaction isolation. It covers locking techniques like two-phase locking and timestamp ordering. Locking involves associating locks like read/write locks with data items. The two-phase locking protocol defines rules for acquiring and releasing locks in two distinct phases. Timestamp ordering assigns unique timestamps to transactions and ensures conflicting operations are executed based on timestamp order to guarantee serializability.