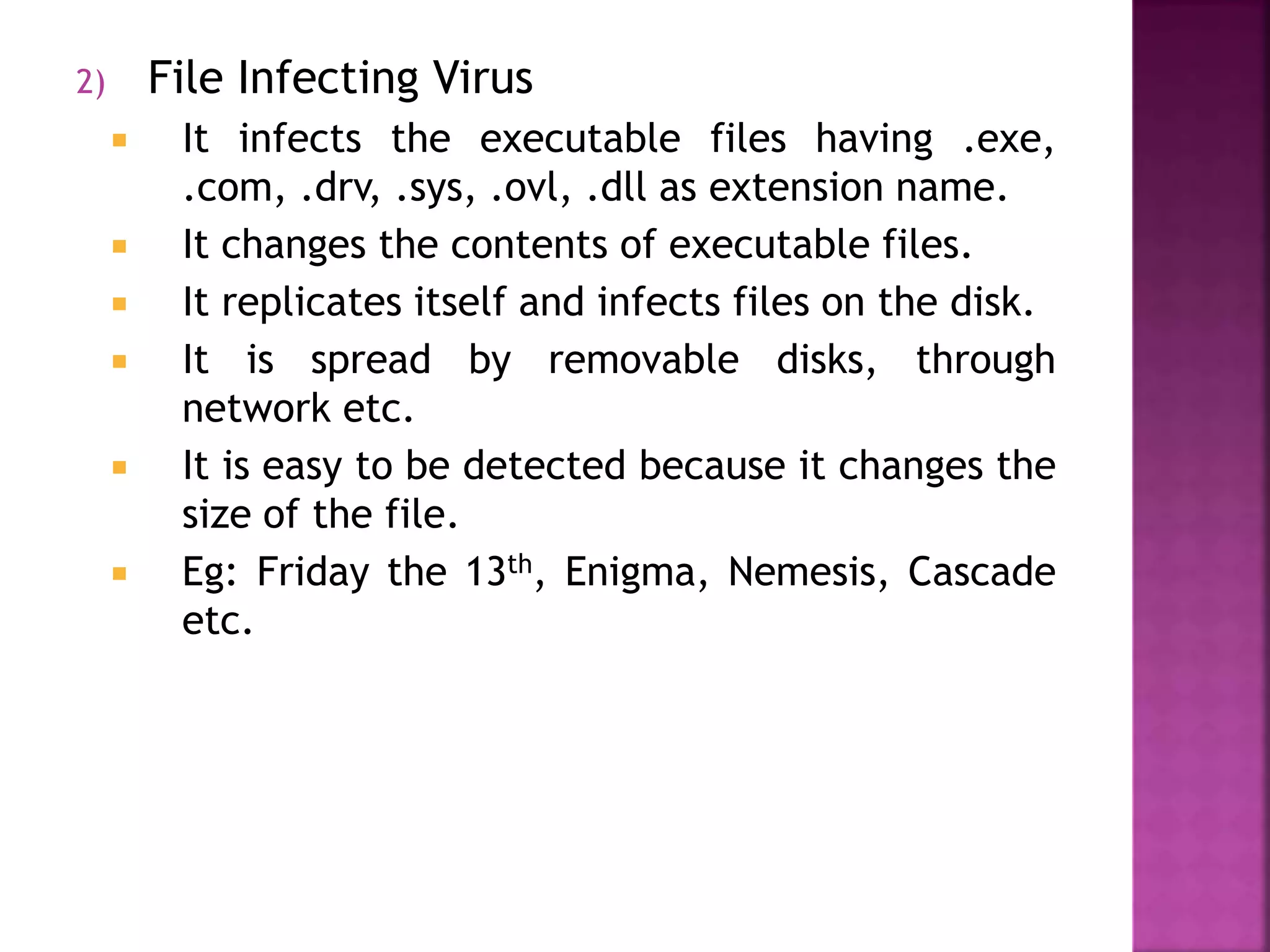
This document discusses computer viruses. It defines a virus as a program that infects and damages files. Viruses replicate by attaching themselves to other programs. They can be transmitted via email attachments, downloaded files, removable drives, or networks. Common symptoms of virus infection include computers running slowly, files changing or deleting unexpectedly, and error messages. The document recommends using antivirus software, scanning downloads, and avoiding suspicious websites or attachments to prevent virus infections. It describes two main types of viruses: boot sector viruses, which infect the boot sector and prevent computers from starting up, and file infecting viruses, which change the contents of files and replicate within files.