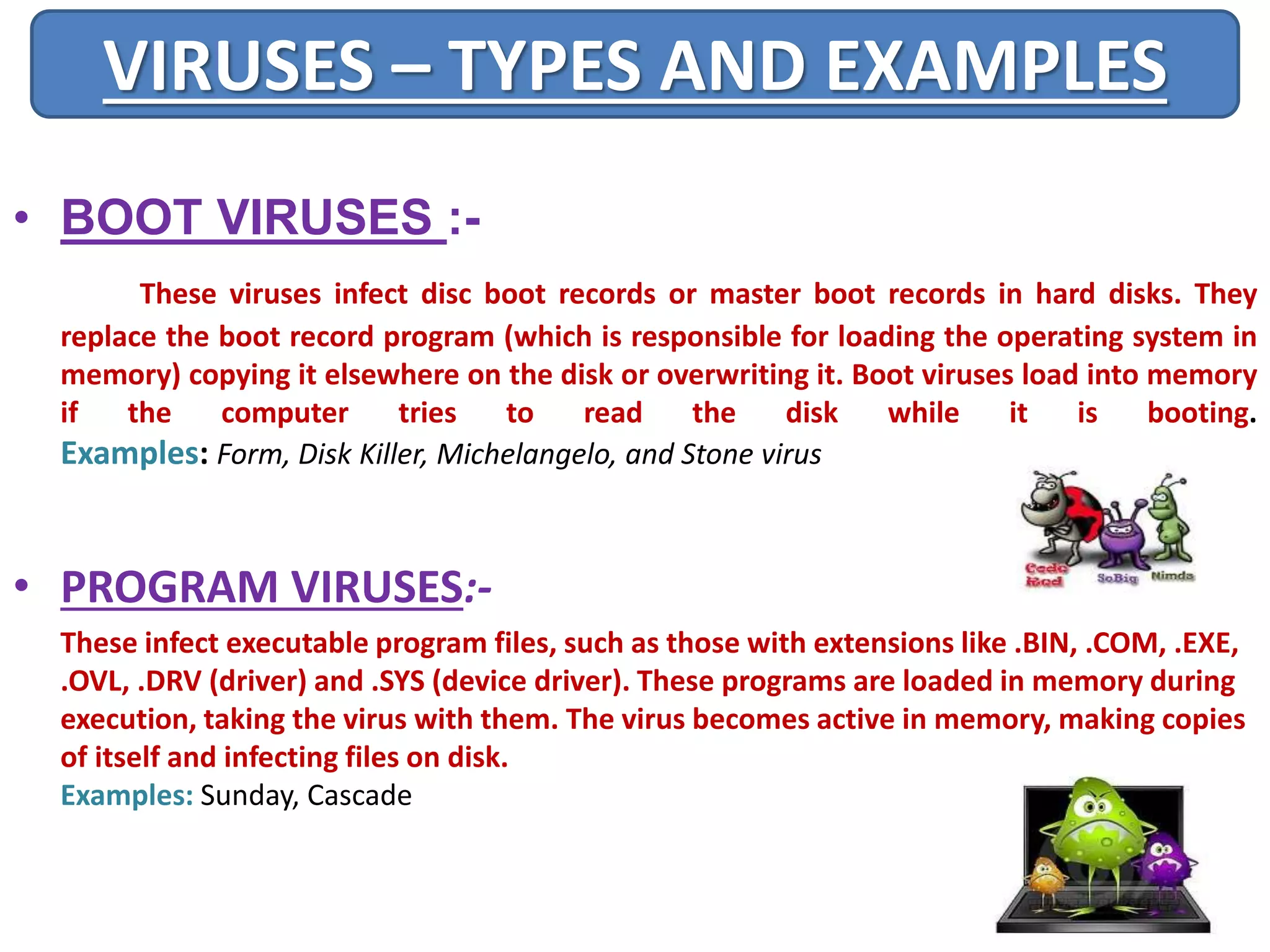
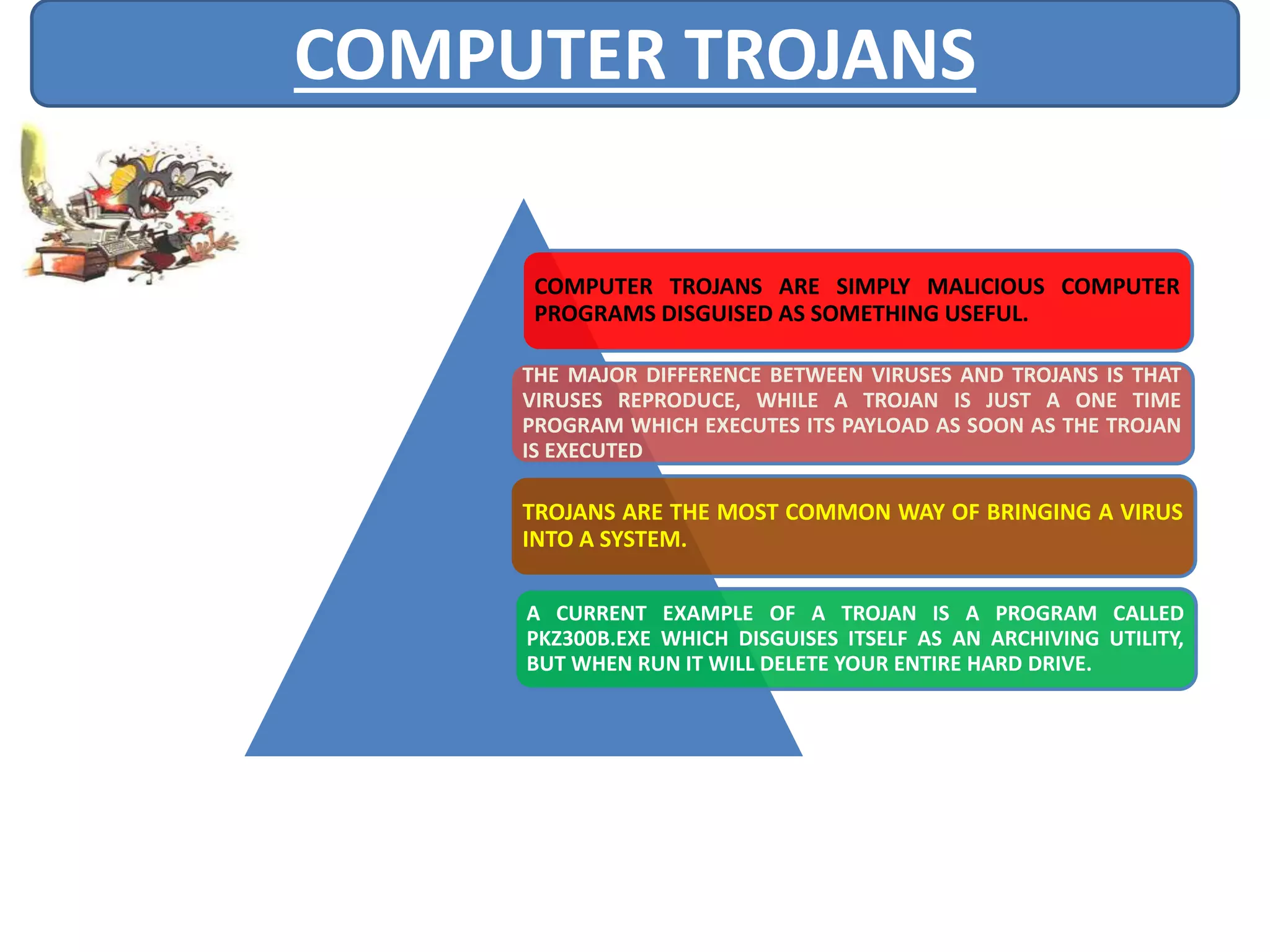
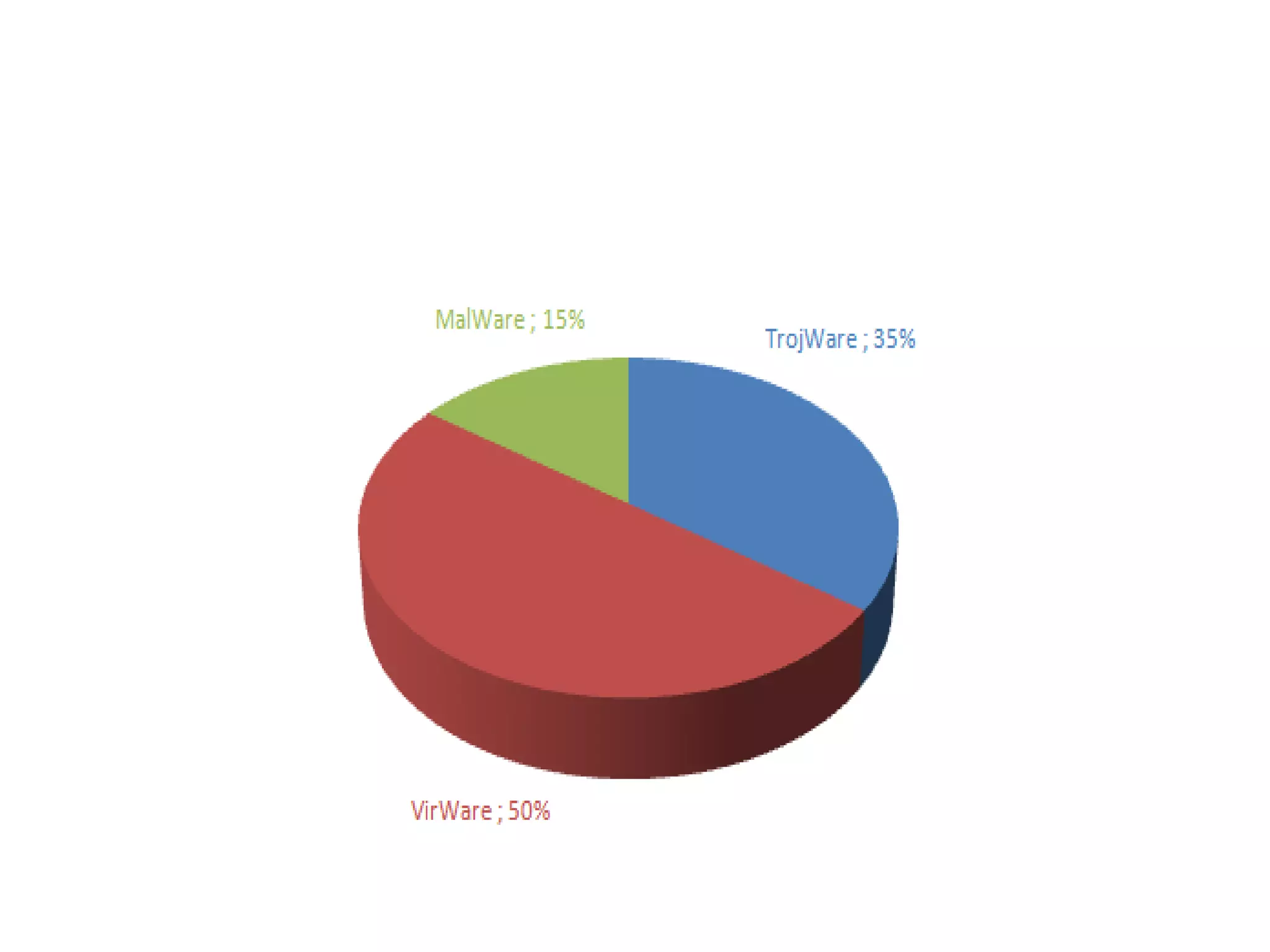
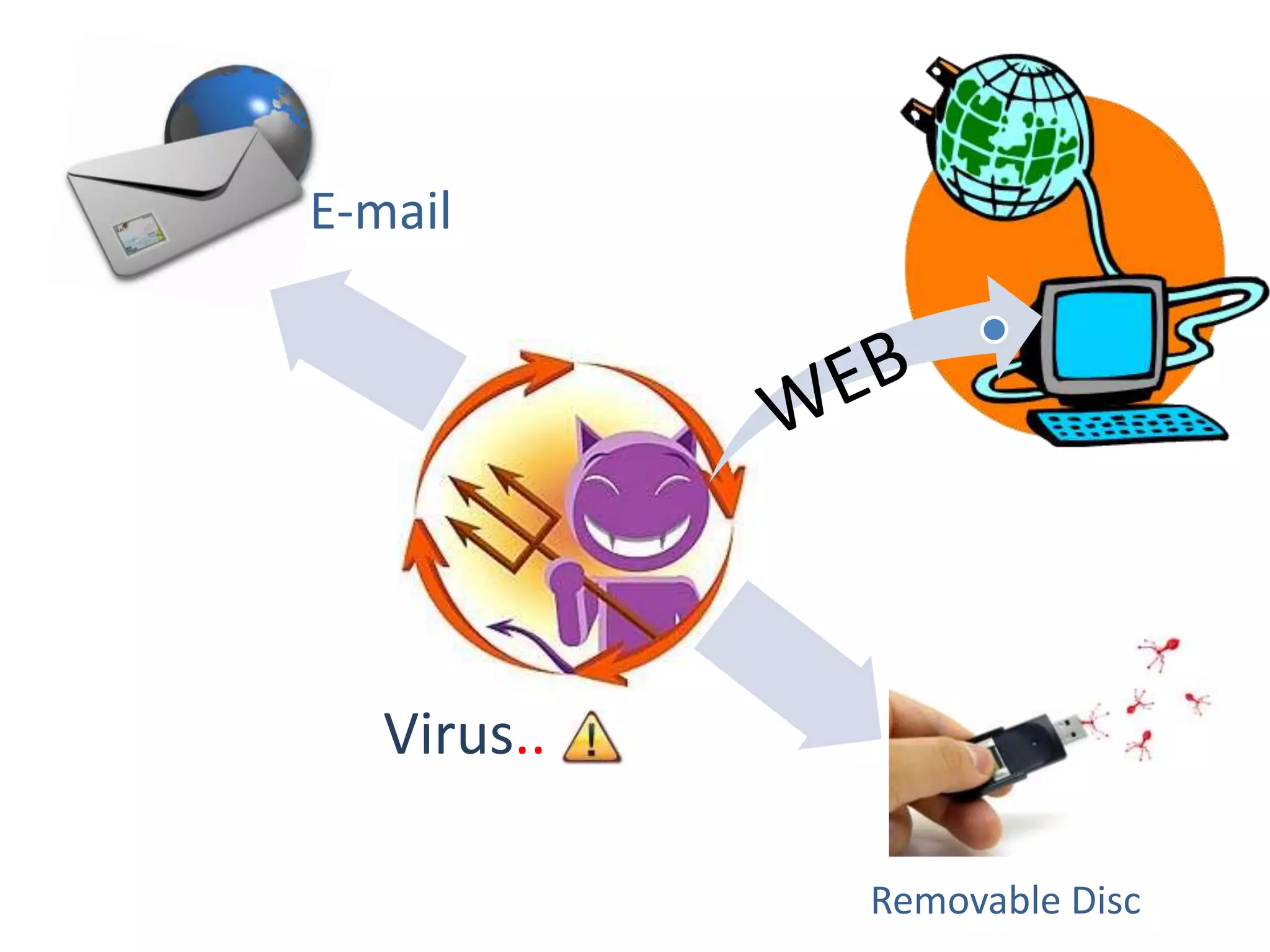
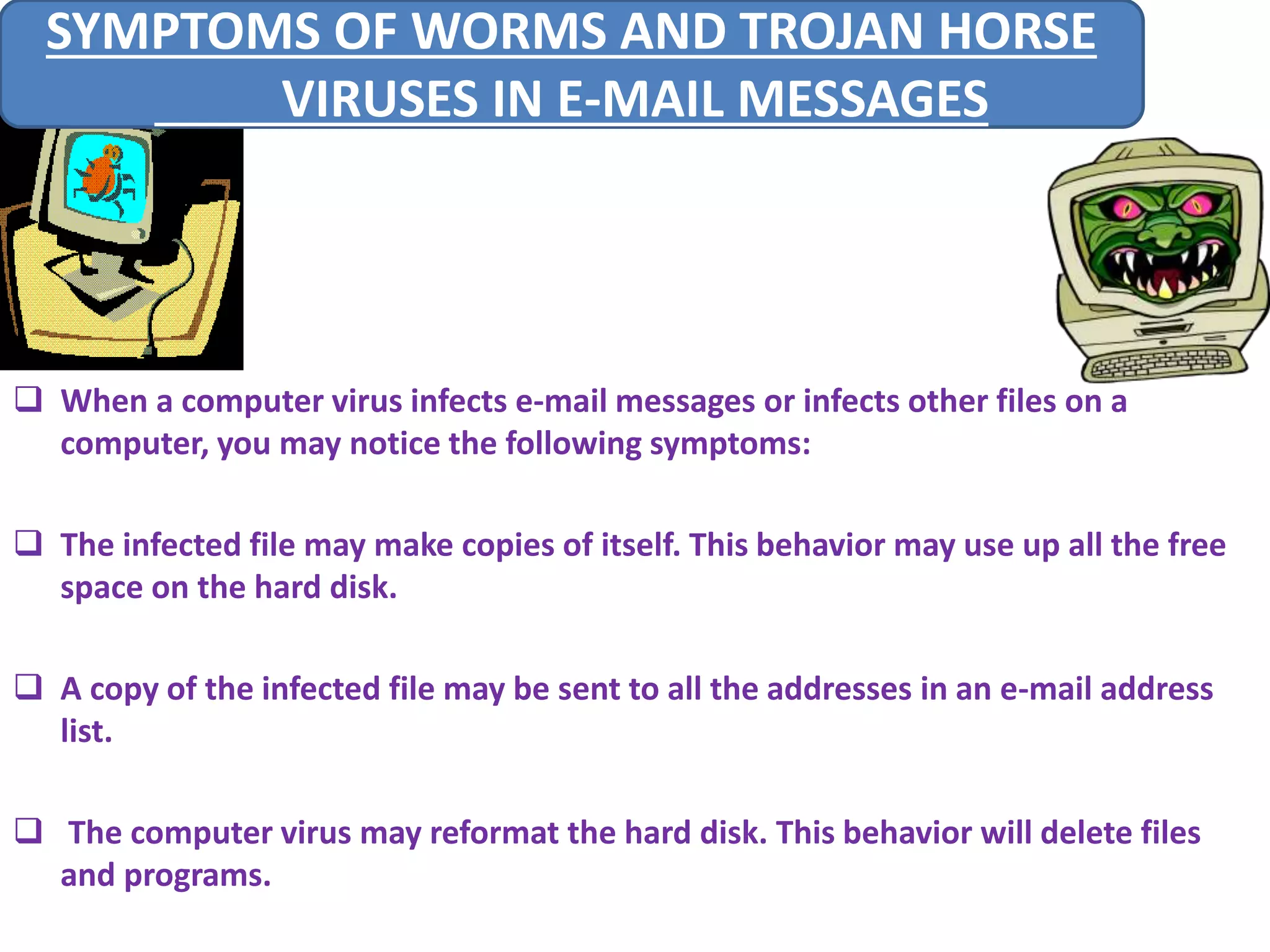
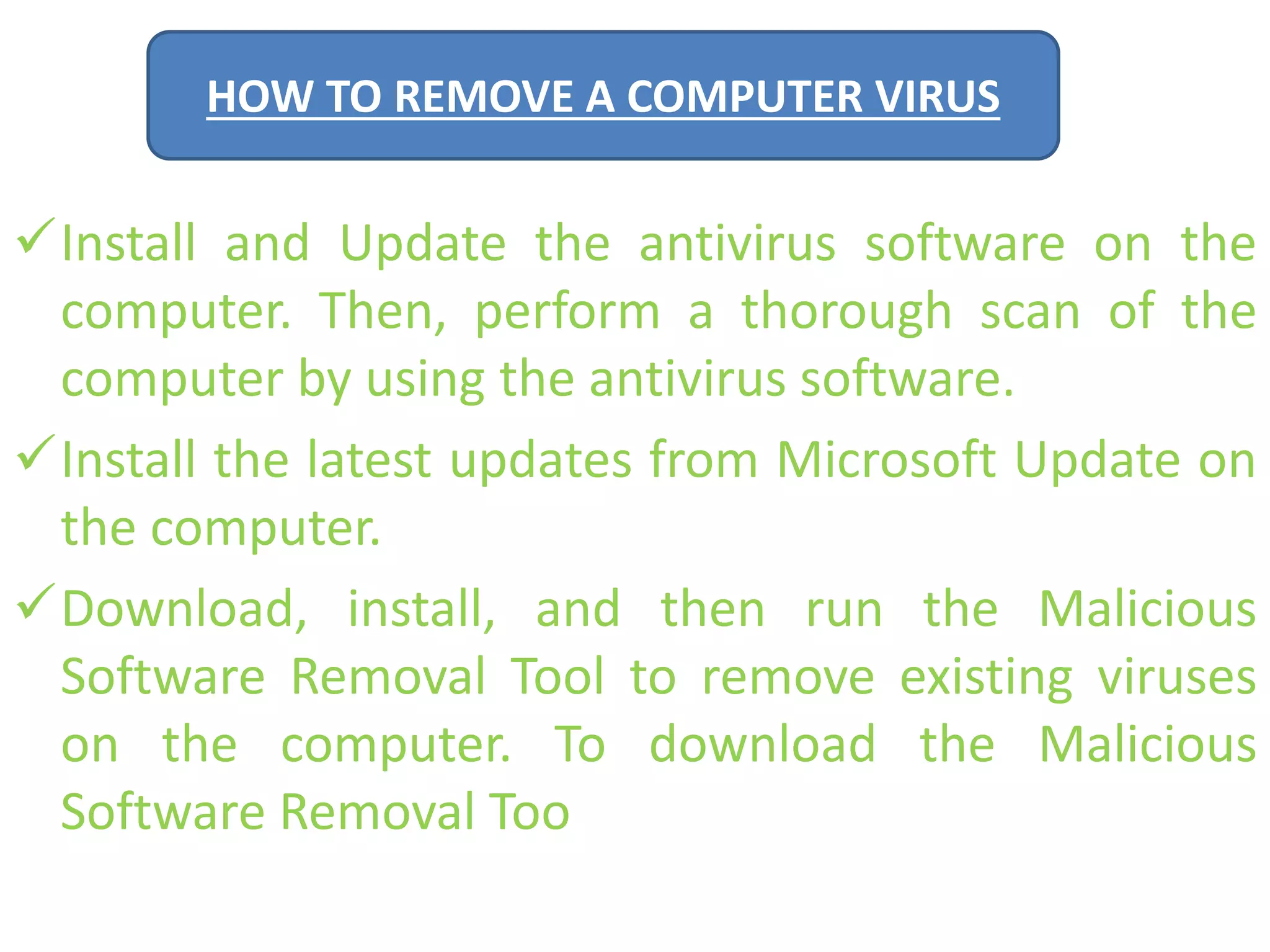
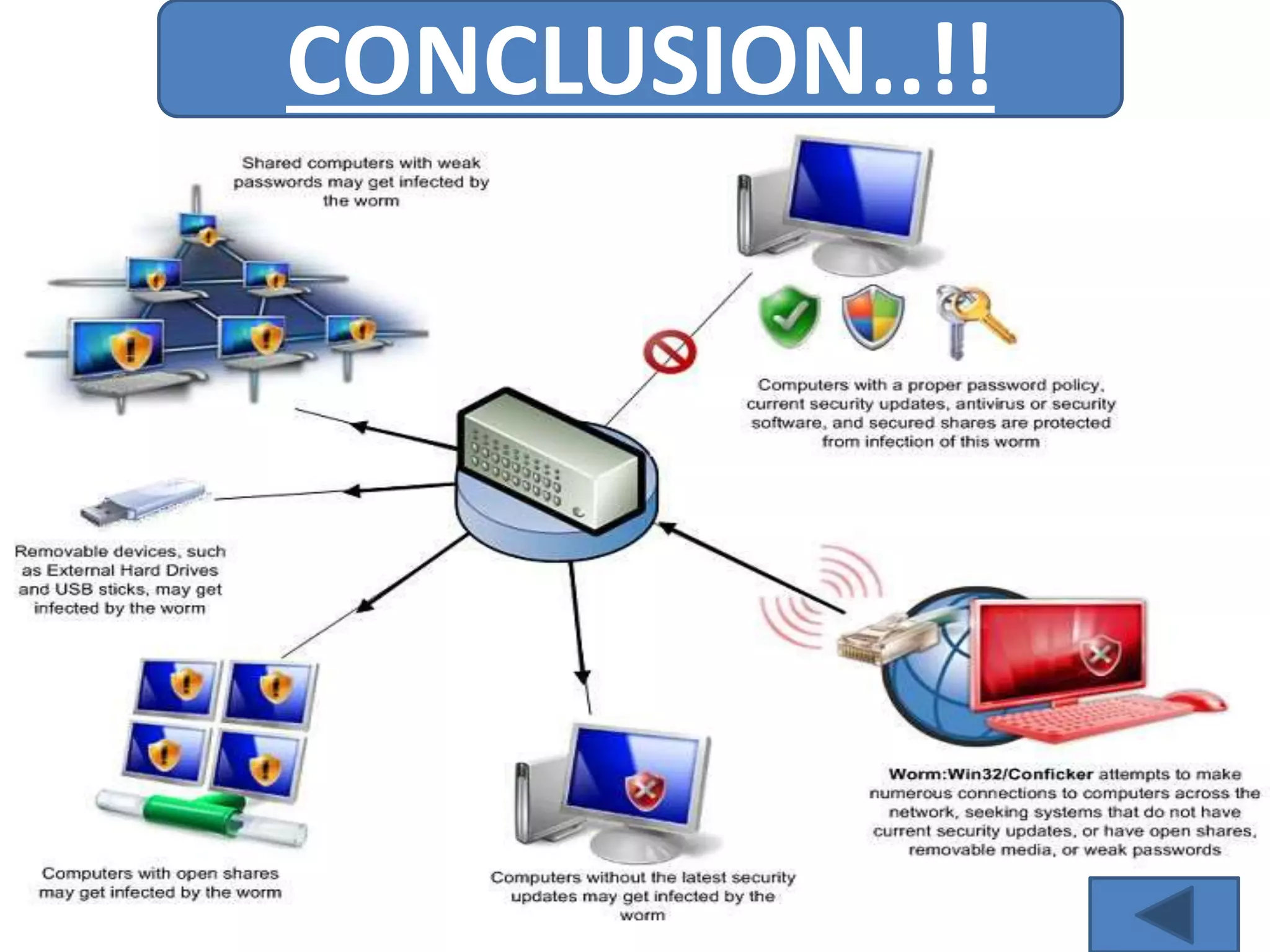
A computer virus is a malicious software program that spreads by copying itself to other computers. It can corrupt or delete data on a computer. Viruses are often spread through email attachments, downloads, and removable media. There are several types of viruses including boot viruses, program viruses, macro viruses, and polymorphic viruses. Symptoms of a virus infection include programs not working properly, critical files being deleted, and the computer running slower. It is important to have antivirus software installed and keep it updated to protect computers from virus infections.