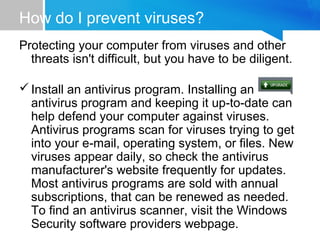
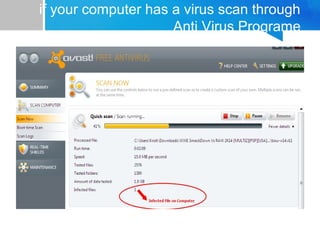
This document discusses different types of malware like viruses, worms, Trojan horses, and blended threats. It provides definitions and explanations of each type. It also gives advice on how to prevent malware infections through practices like keeping antivirus software updated, not opening email attachments from unknown senders, keeping Windows updated, and using a firewall. The document outlines some signs that a computer may have a virus and provides steps people can take to check for and remove viruses, such as using an online scanner, the Malicious Software Removal Tool, or manually removing viruses by identifying them. It also explains what Data Execution Prevention is and how it helps protect against malware attacks.