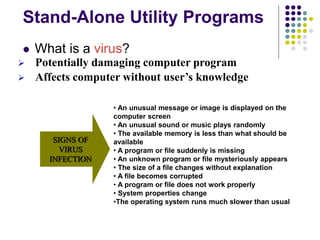
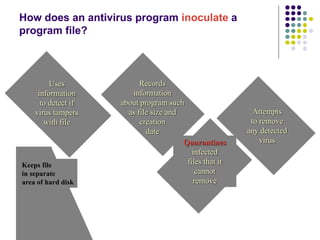
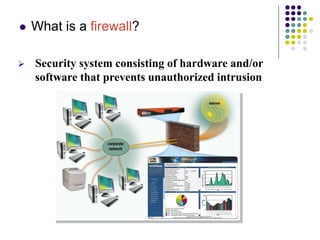
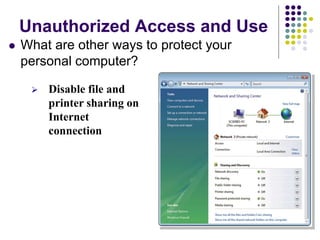
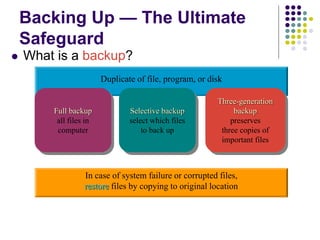
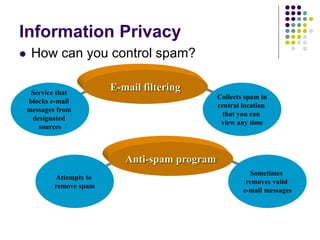
The document provides an overview of computer security risks, focusing on different types of computer viruses, worms, and trojan horses. It explains how these malicious programs can spread, their effects on computer systems, and signs of infection. Additionally, it discusses the importance of antivirus programs, firewalls, and preventative measures to protect personal computers from these threats.