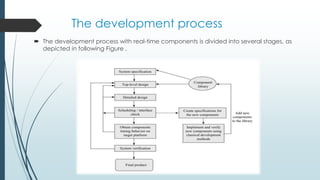
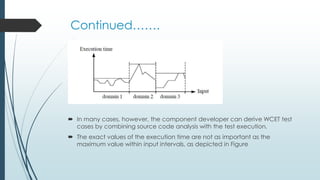
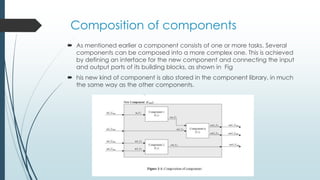
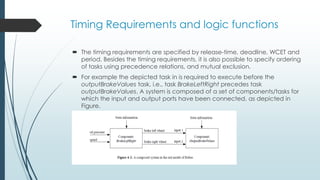
This document discusses components in real-time systems. It defines real-time systems as those with tight timing constraints where responses must occur within strict deadlines. It describes the components of real-time systems as modular and cohesive software packages that communicate via interfaces. The document outlines a process for developing component-based real-time systems, including top-level design, detailed design, scheduling, worst-case execution time verification, and system implementation and testing. It provides examples of real-time components from the Rubus operating system.