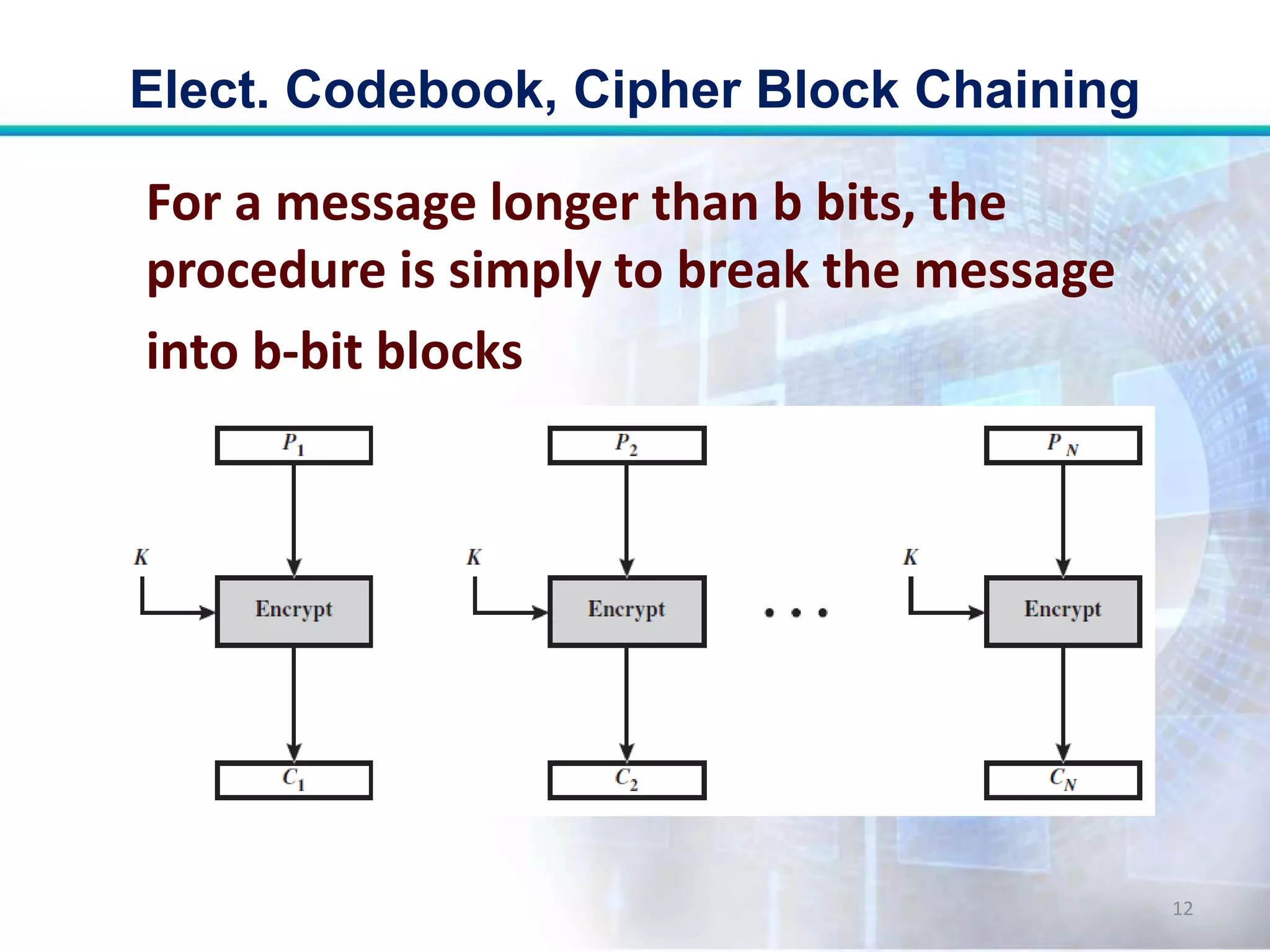
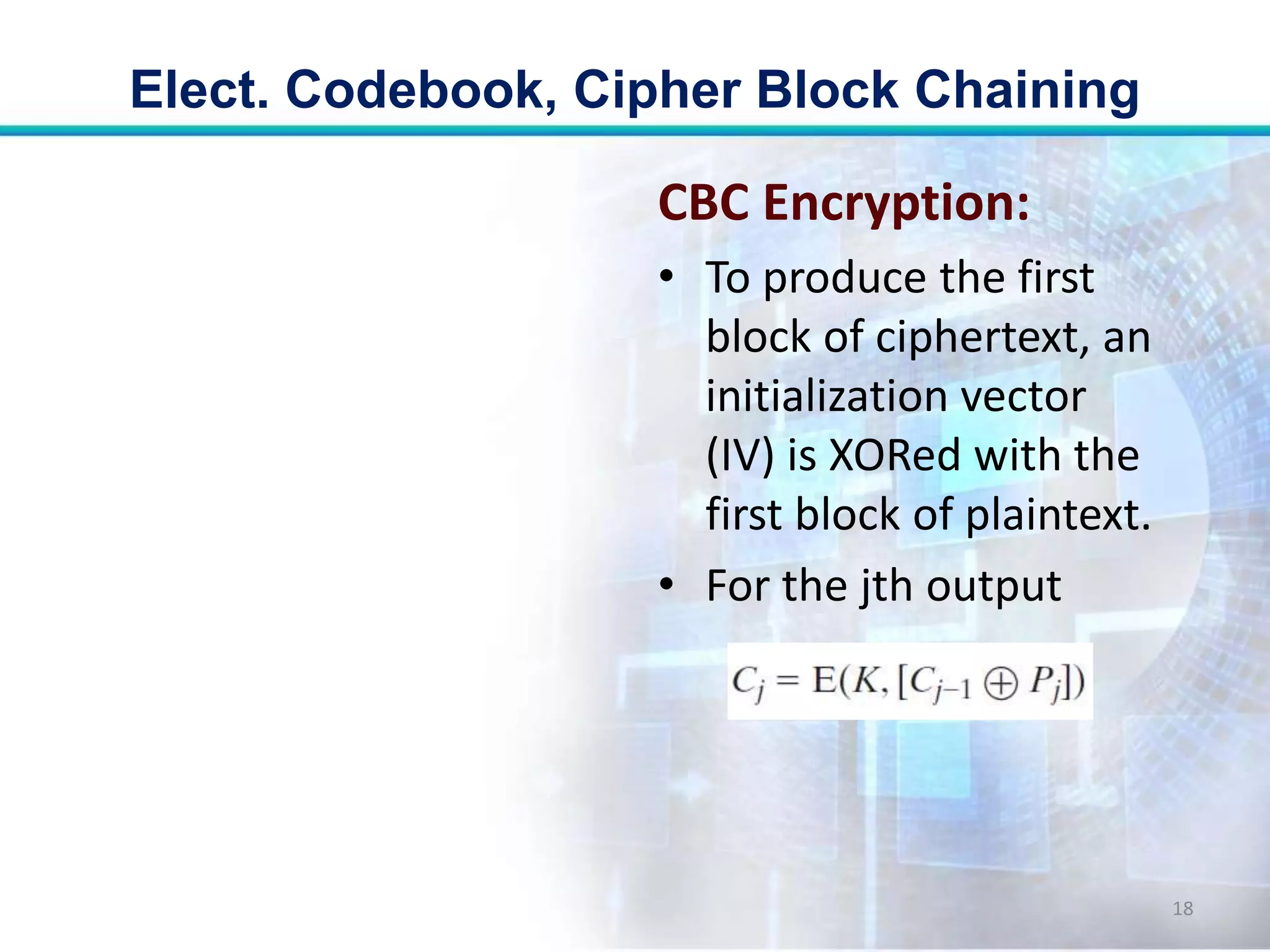
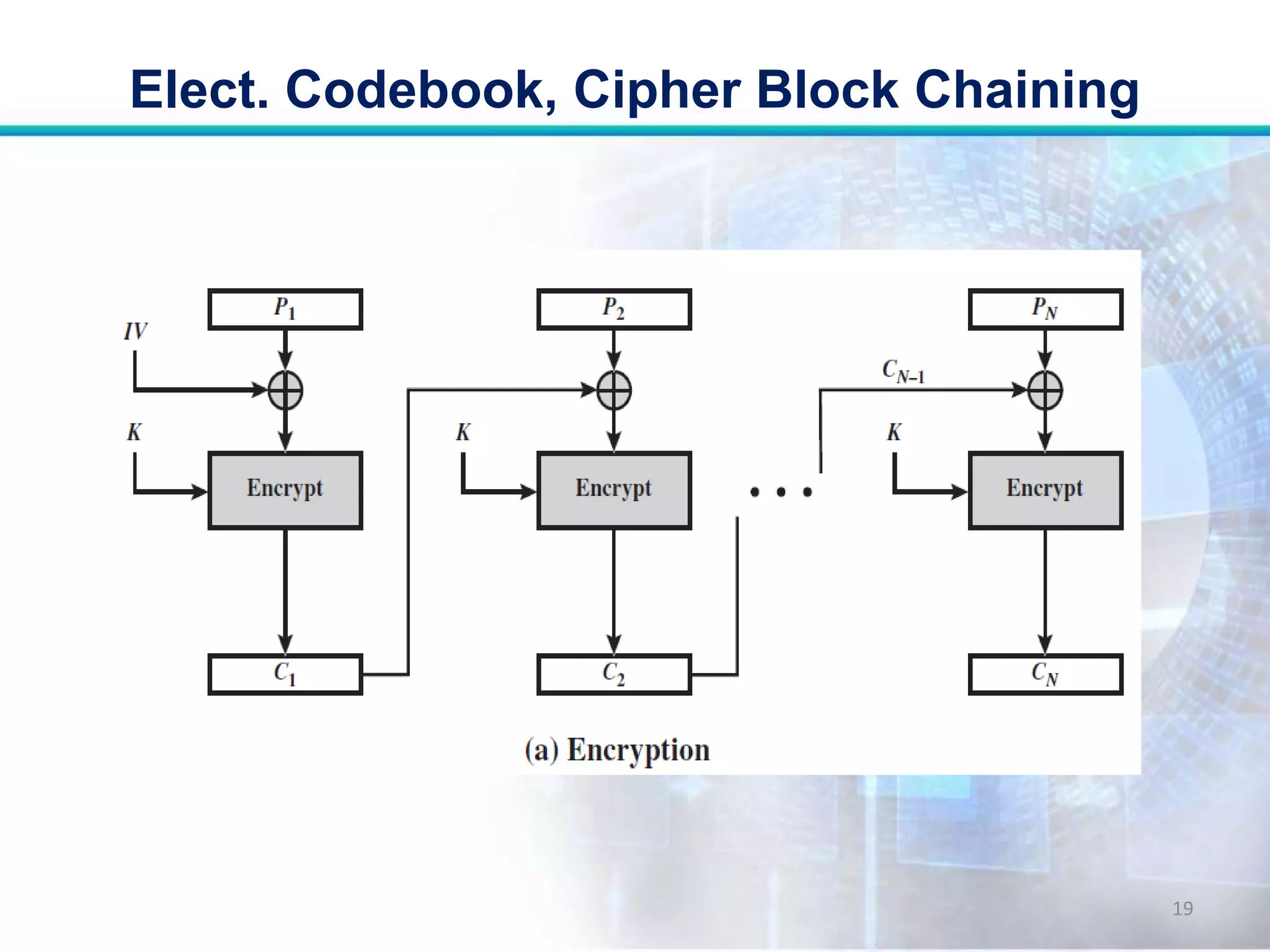
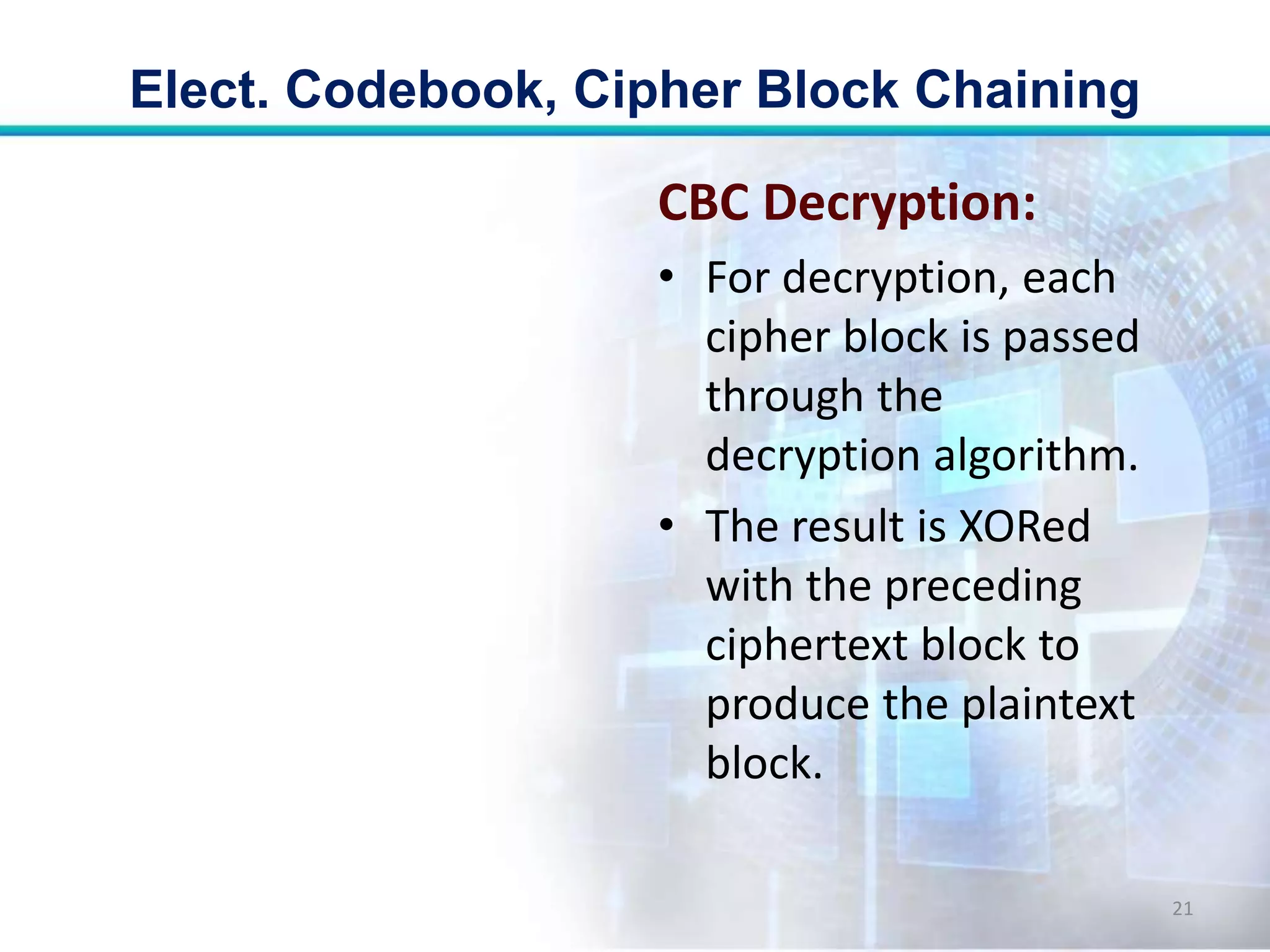
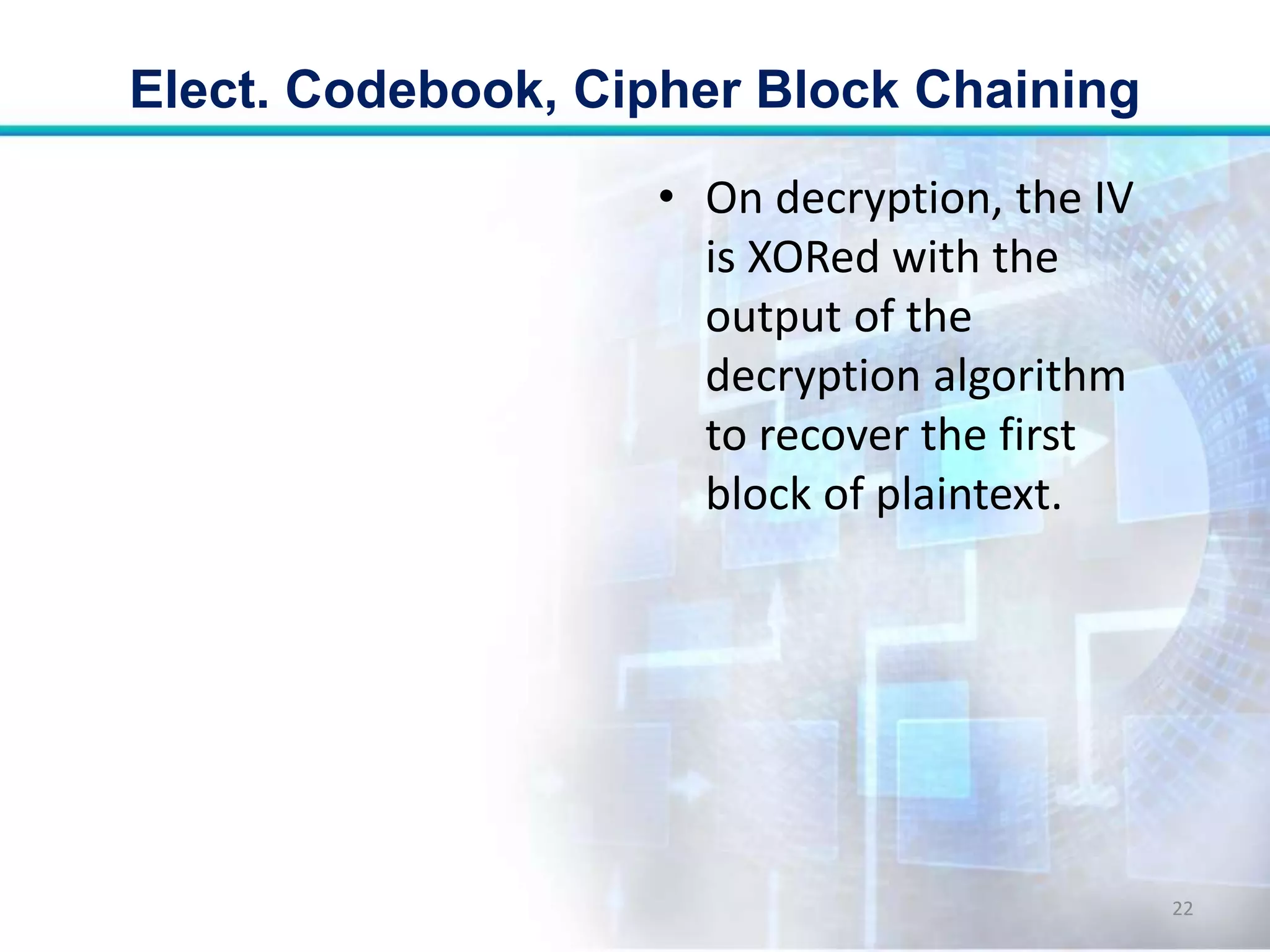
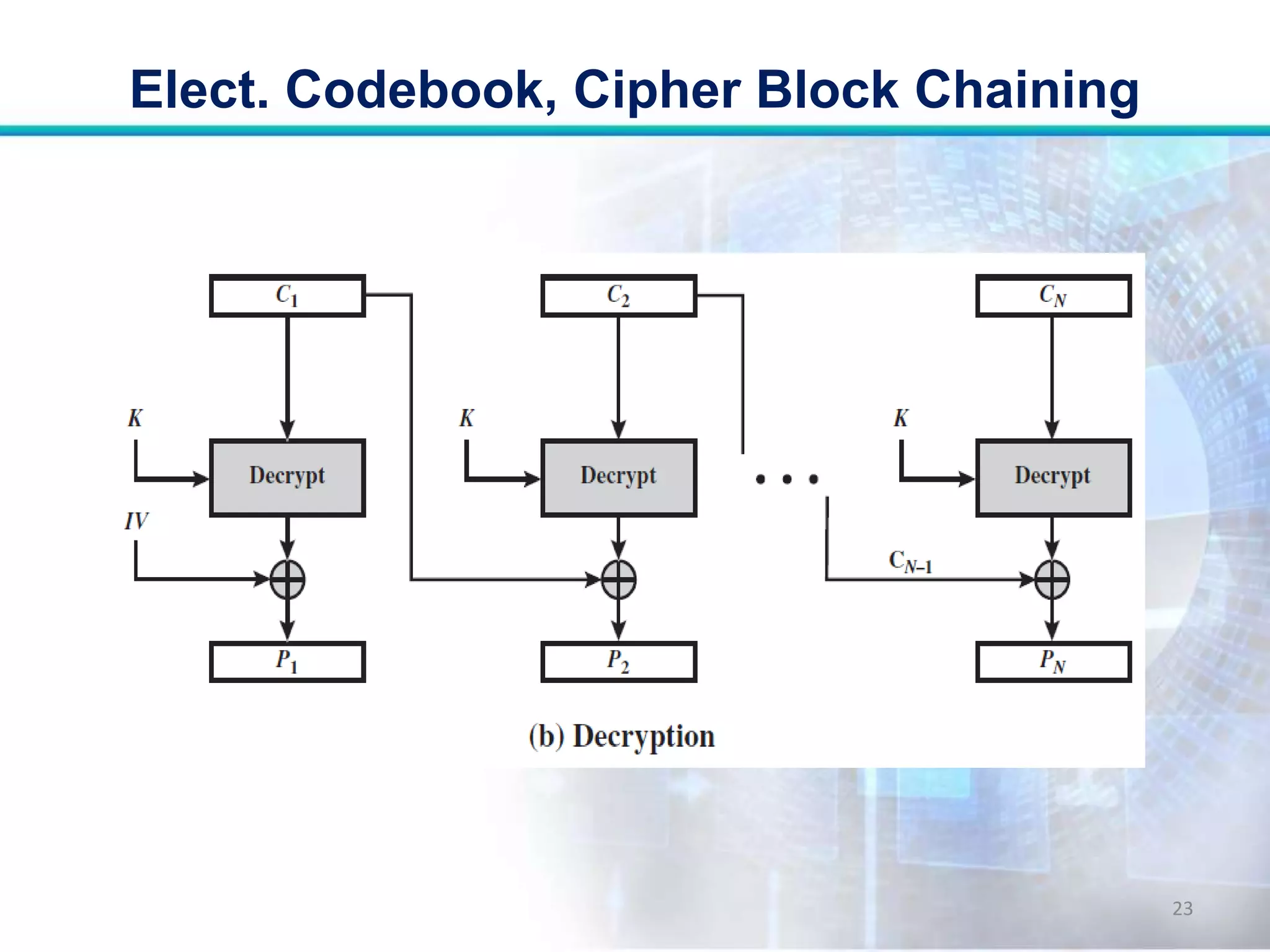
This document discusses two modes of operation for block ciphers: electronic codebook (ECB) mode and cipher block chaining (CBC) mode. ECB encrypts each plaintext block independently with the same key, resulting in the same ciphertext if the same plaintext is repeated. CBC improves on ECB by XORing each plaintext block with the previous ciphertext block before encryption to prevent repetitions in the ciphertext. The document outlines the encryption and decryption processes for ECB and CBC, noting that CBC is more secure for long messages.