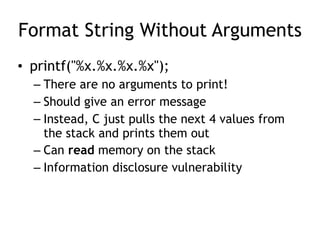
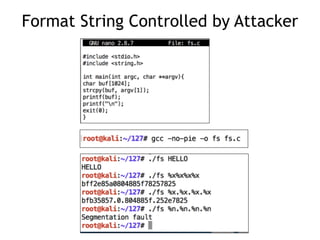
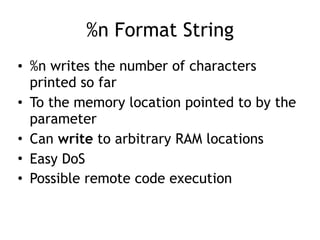
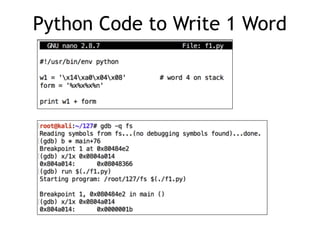
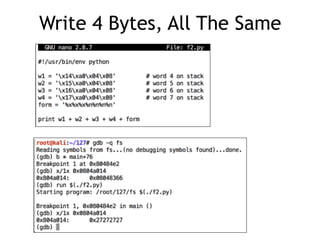
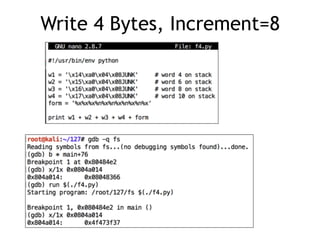
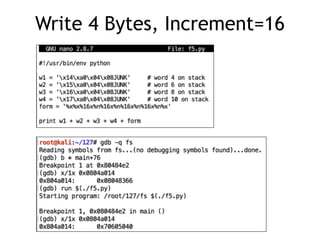
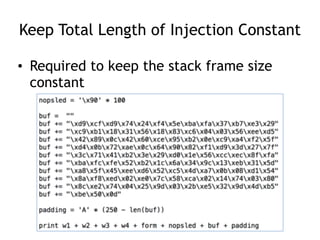
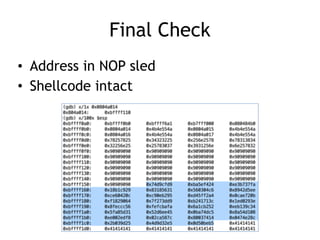
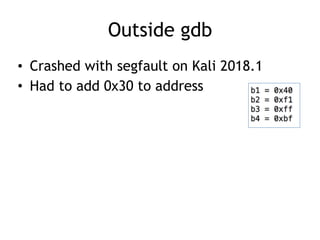
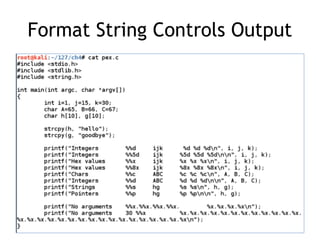
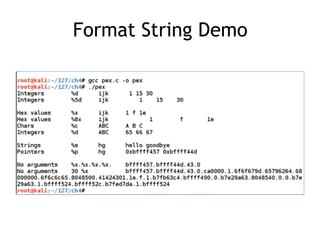
The document provides an overview of format string vulnerabilities, detailing how these bugs can lead to memory exploitation and arbitrary code execution. It explains several exploitation techniques, including manipulation of the stack and the Global Offset Table (GOT) to gain control of program execution. Additionally, the document discusses countermeasures and the usage of tools like GDB for debugging and testing vulnerabilities.




![Buffer Overflow
• This code is obviously stupid
char name[10];
strcpy(name, "Rumplestiltskin");
• C just does it, without complaining](https://image.slidesharecdn.com/127-ch4-180210161806/85/CNIT-127-Ch-4-Introduction-to-format-string-bugs-8-320.jpg)