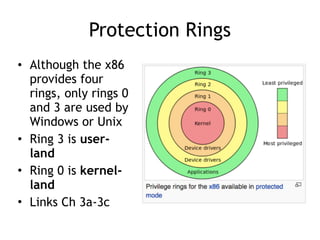
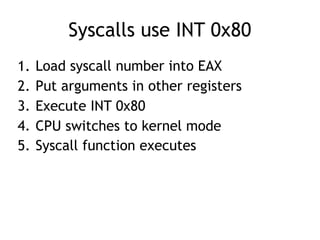
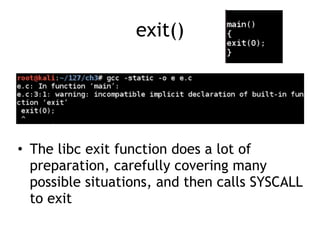
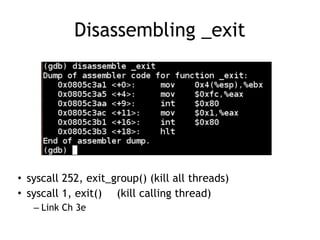
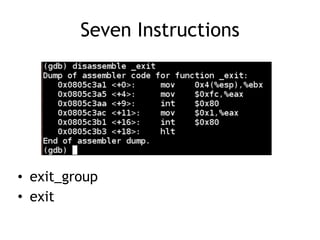
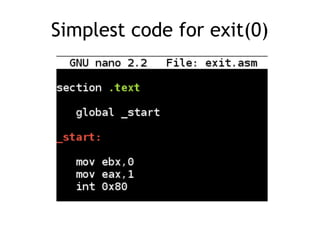
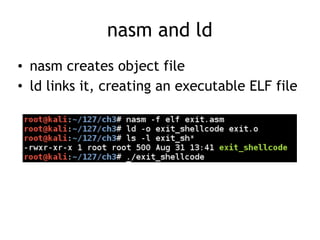
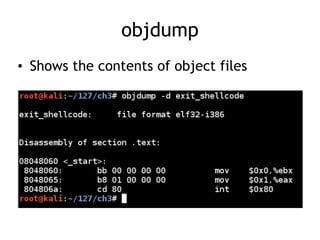
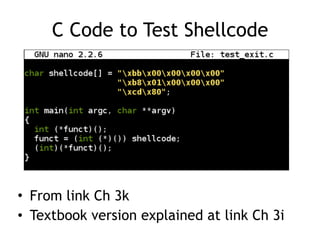
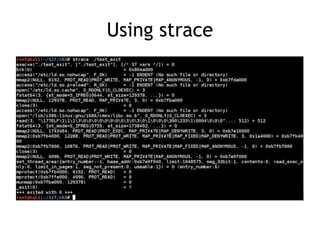
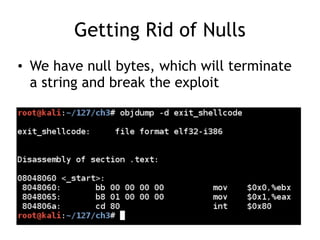
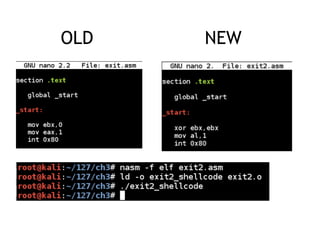
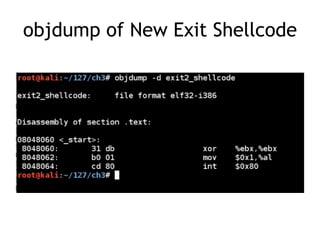
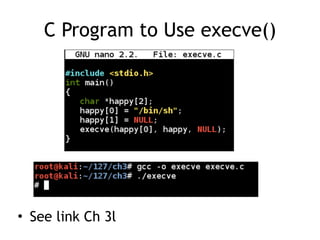
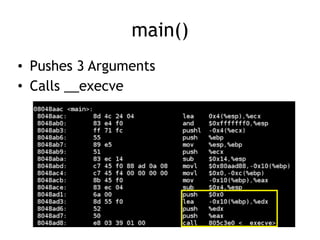
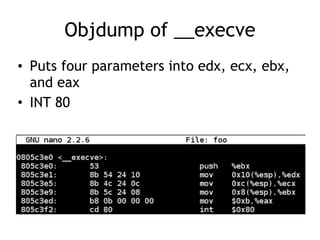
The document discusses shellcode development, focusing on its creation using assembly language, system calls, and processes in Linux. It explains how shellcode is injected into a system to exploit vulnerabilities, highlighting crucial components like protection rings, syscall interactions, and the importance of compact code to avoid null bytes. Additionally, it provides an overview of the functions exit() and execve(), along with the steps to write effective shellcode.