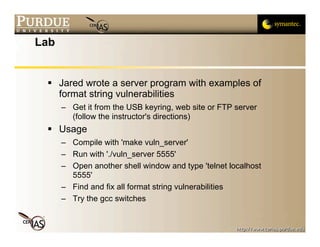
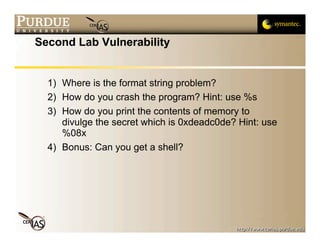
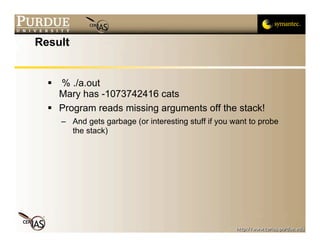
This document discusses format string vulnerabilities in programming. It begins by explaining what a format string is in C and how it can be exploited if the format string is controlled by an attacker. It then provides examples of format string vulnerabilities, how to define them, and their importance. The document analyzes a specific vulnerability in the cfingerd 1.4.3 program and discusses how to prevent format string vulnerabilities through safe programming practices.







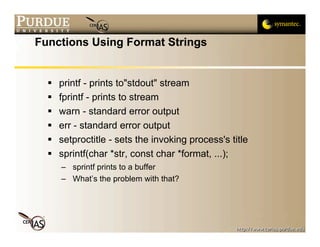
![User-specified Format String
What happens if the following code is run,
assuming there always is an argument input by a
user?
int main(int argc, char *argv[])
{
printf(argv[1]);
exit(0);
}
Try it and input "%s%s%s%s%s%s%s%s%s"
How many "%s" arguments do you need to crash
it?](https://image.slidesharecdn.com/2-formatstrings-091013224252-phpapp02/85/2-Format-Strings-9-320.jpg)

![Corrected Program
int
main(int argc, char *argv[])
{
printf(“%s”, argv[1]);
exit(0);
}
% ./a.out "%s%s%s%s%s%s%s"
%s%s%s%s%s%s%s](https://image.slidesharecdn.com/2-formatstrings-091013224252-phpapp02/85/2-Format-Strings-11-320.jpg)










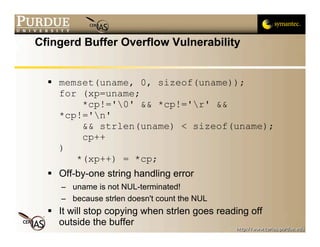
![Direct Effect of Off-by-one Error
char buf[BUFLEN], uname[64];
"uname" and "buf" are "joined" as one string!
So, even if only 64 characters from the input are
copied into "uname", string manipulation functions
will work with "uname+buf" as a single entity
"buf" was used to read the response from the
ident server so it is the raw input](https://image.slidesharecdn.com/2-formatstrings-091013224252-phpapp02/85/2-Format-Strings-24-320.jpg)