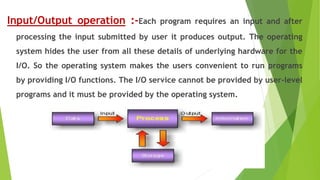
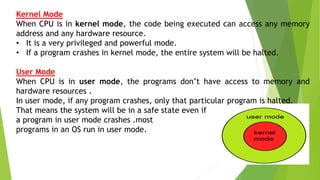
The document discusses the key system services provided by operating systems. It describes seven common services: program execution, input/output operations, file system manipulation, communications, error detection, resource allocation, and protection. For each service, it provides details on how the operating system handles and abstracts the low-level hardware operations to provide a more convenient interface for users and programs. It also discusses system calls which allow programs to interface with the operating system to utilize these services.