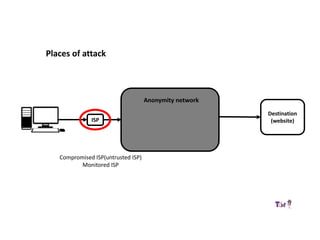
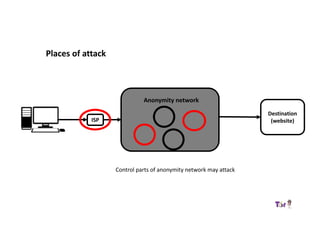
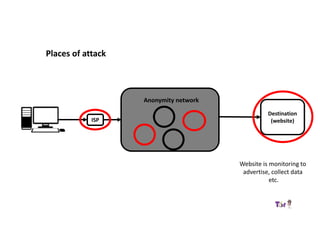
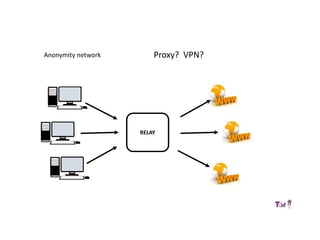
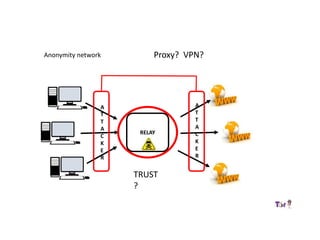
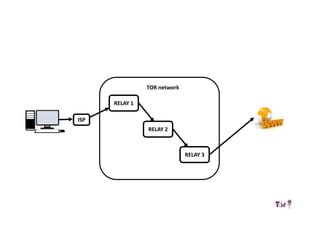
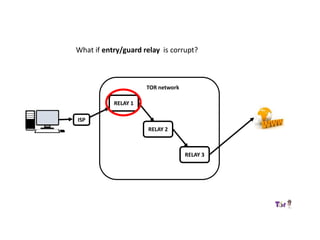
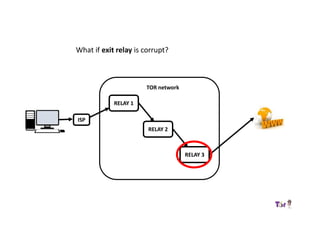
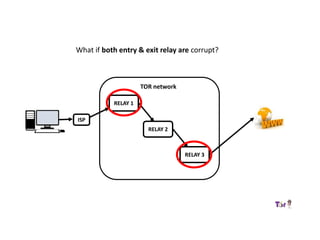
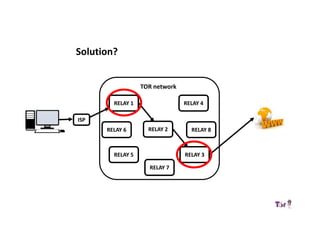
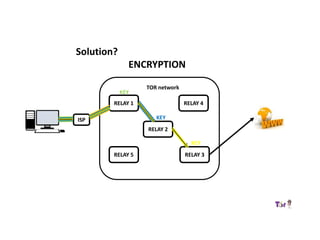
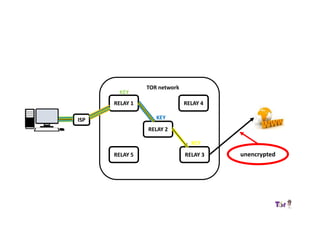
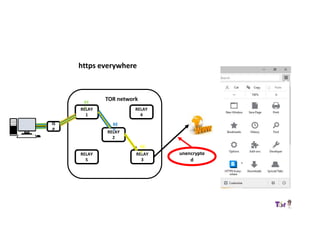
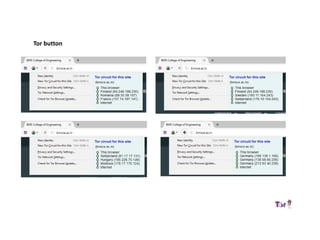
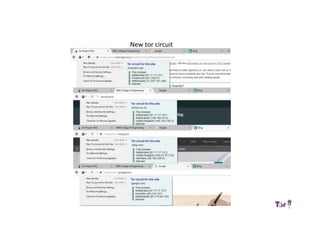
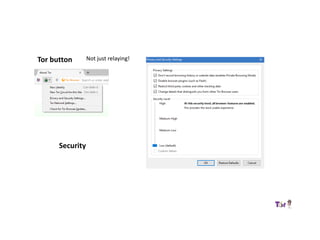
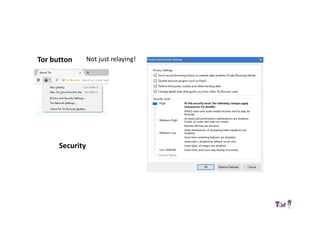
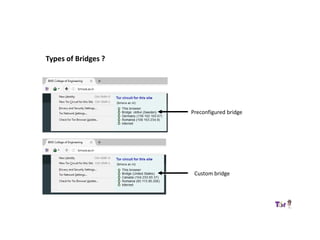
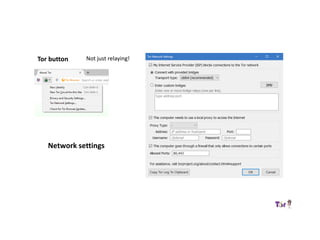
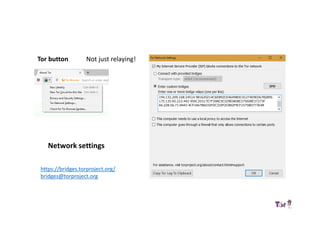
The document provides an overview of how the Tor network functions, including its design and components like relays, encryption, and bridges. It discusses the importance of using Tor for maintaining anonymity online and the potential vulnerabilities to the network from compromised ISPs or relays. Additional resources and tools for using Tor and enhancing security are also mentioned.