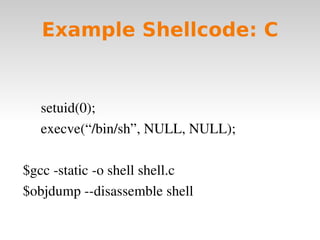
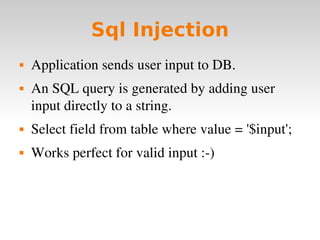
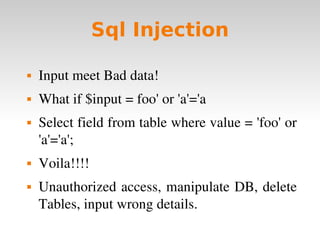
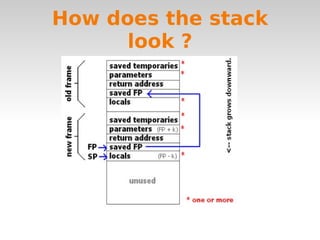
Code injection occurs when invalid data is injected as code instead of data and executed as part of a program. Common code injection techniques include buffer overflows, SQL injection, and cross-site scripting (XSS). Buffer overflows occur when input length exceeds the buffer size, overwriting the stack and potentially changing the return address. SQL injection happens when unsanitized user input is inserted into SQL queries, allowing manipulation of the database. XSS injects client-side script code by inputting it into a web application. To prevent code injection, developers must never trust unsanitized user input.






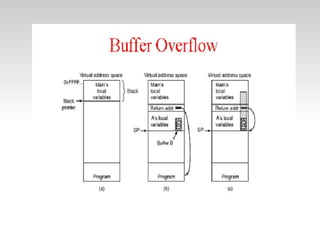
![Example Vulnerable Code int vul_func(char * src) { char vul_buf[40] = {0}; … strcpy(vul_buf, src); … return 0; }](https://image.slidesharecdn.com/aseemappsec-100402073631-phpapp02/85/null-Pune-meet-Application-Security-Code-injection-9-320.jpg)