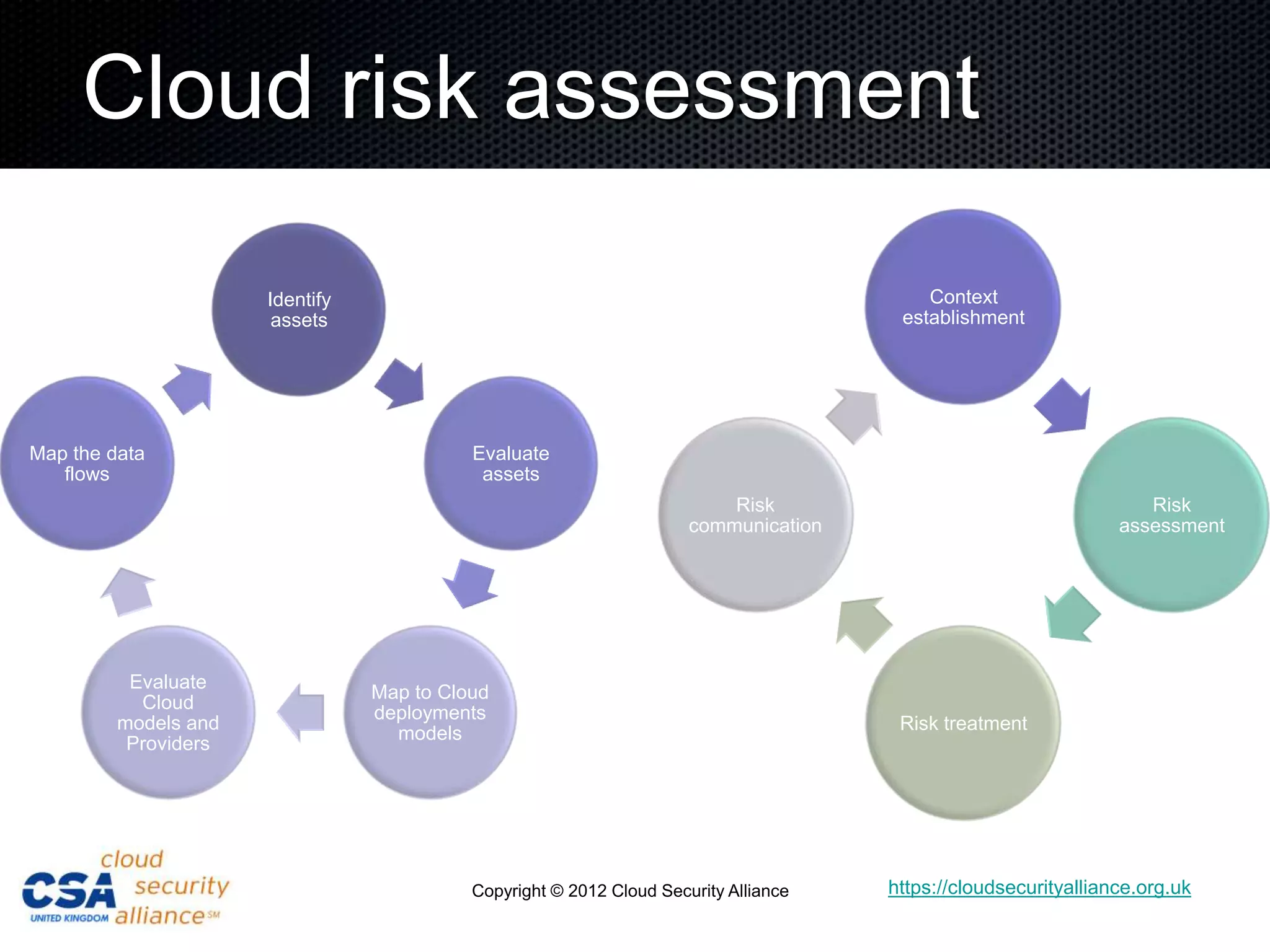
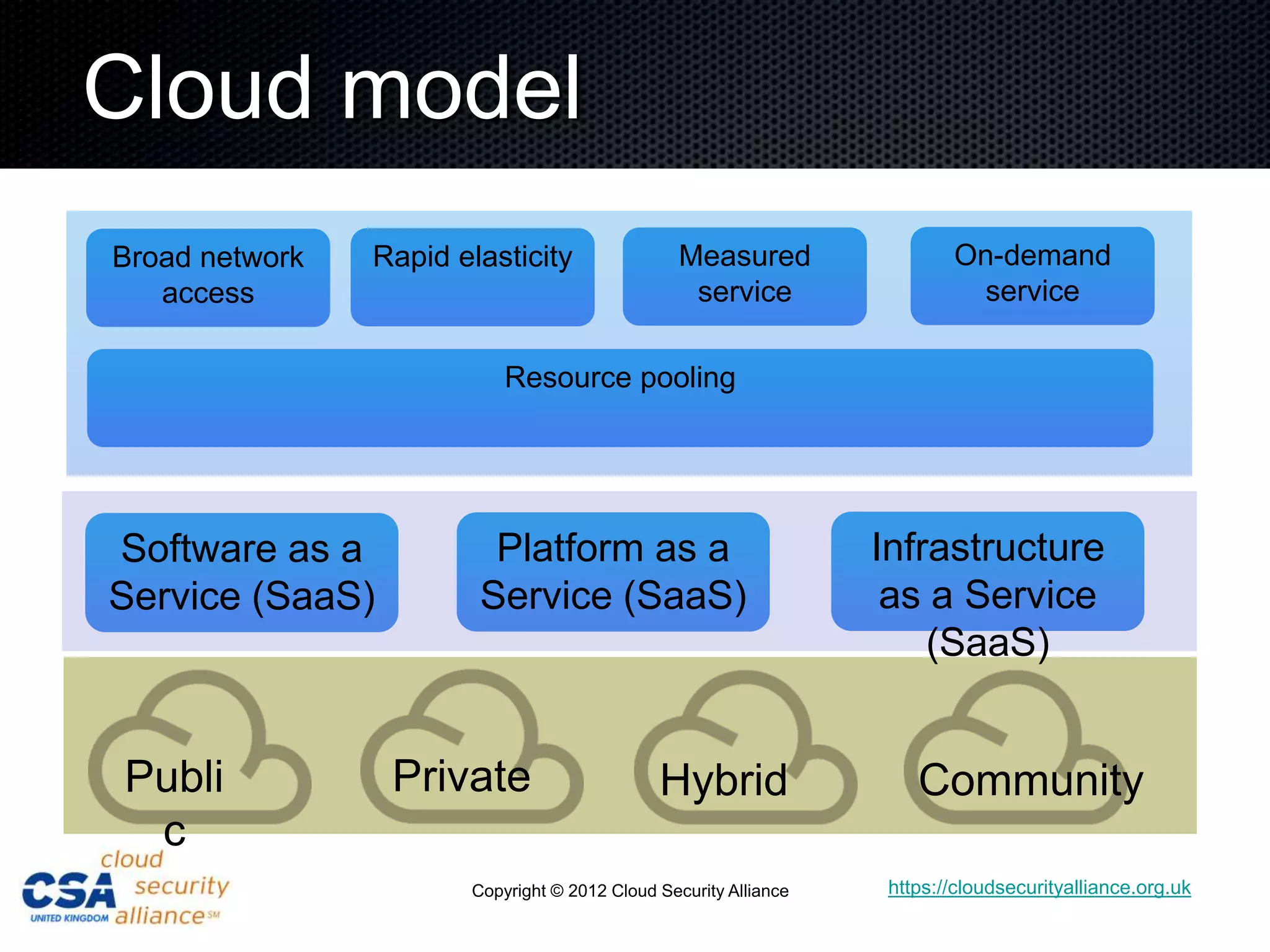
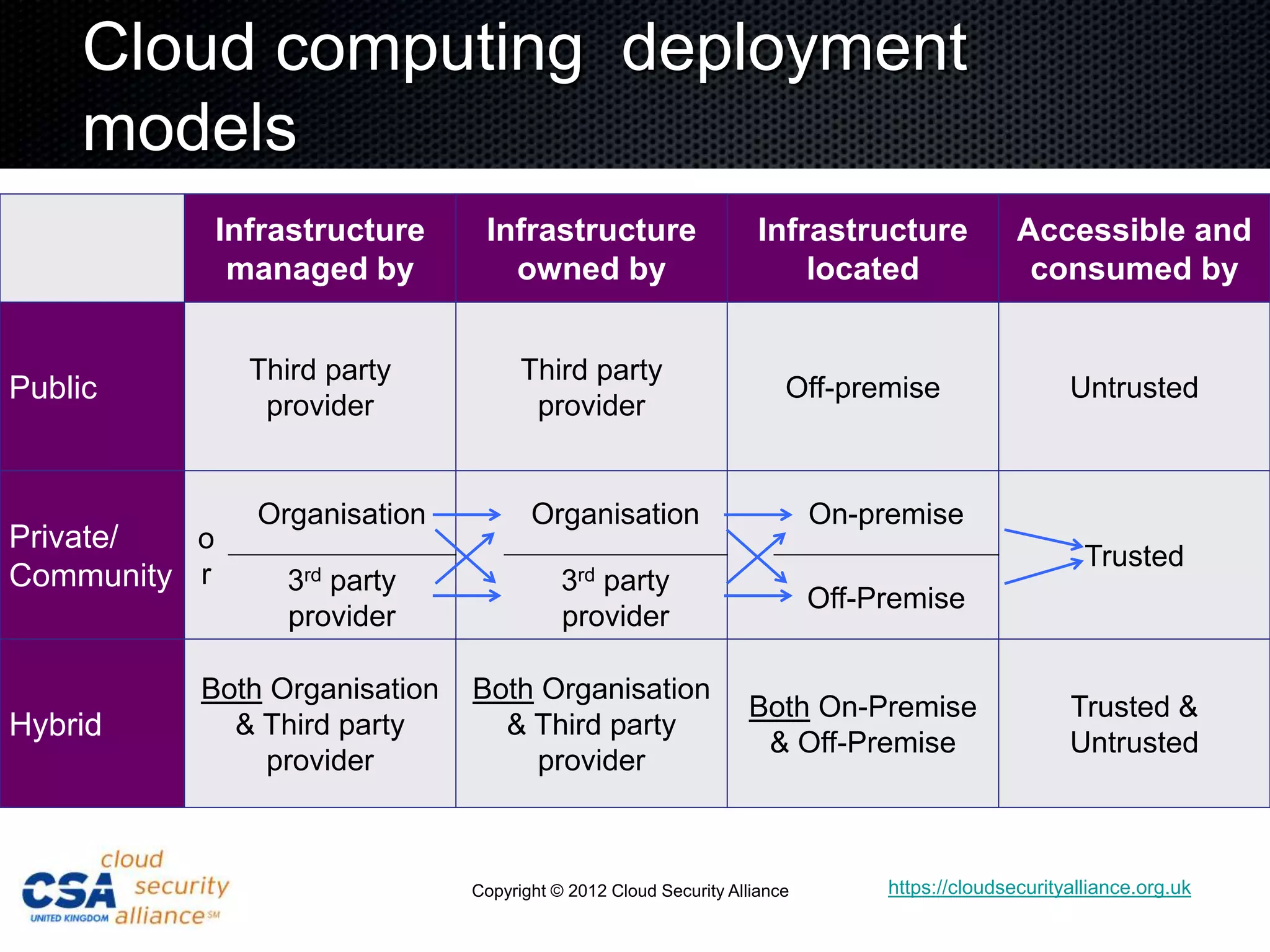
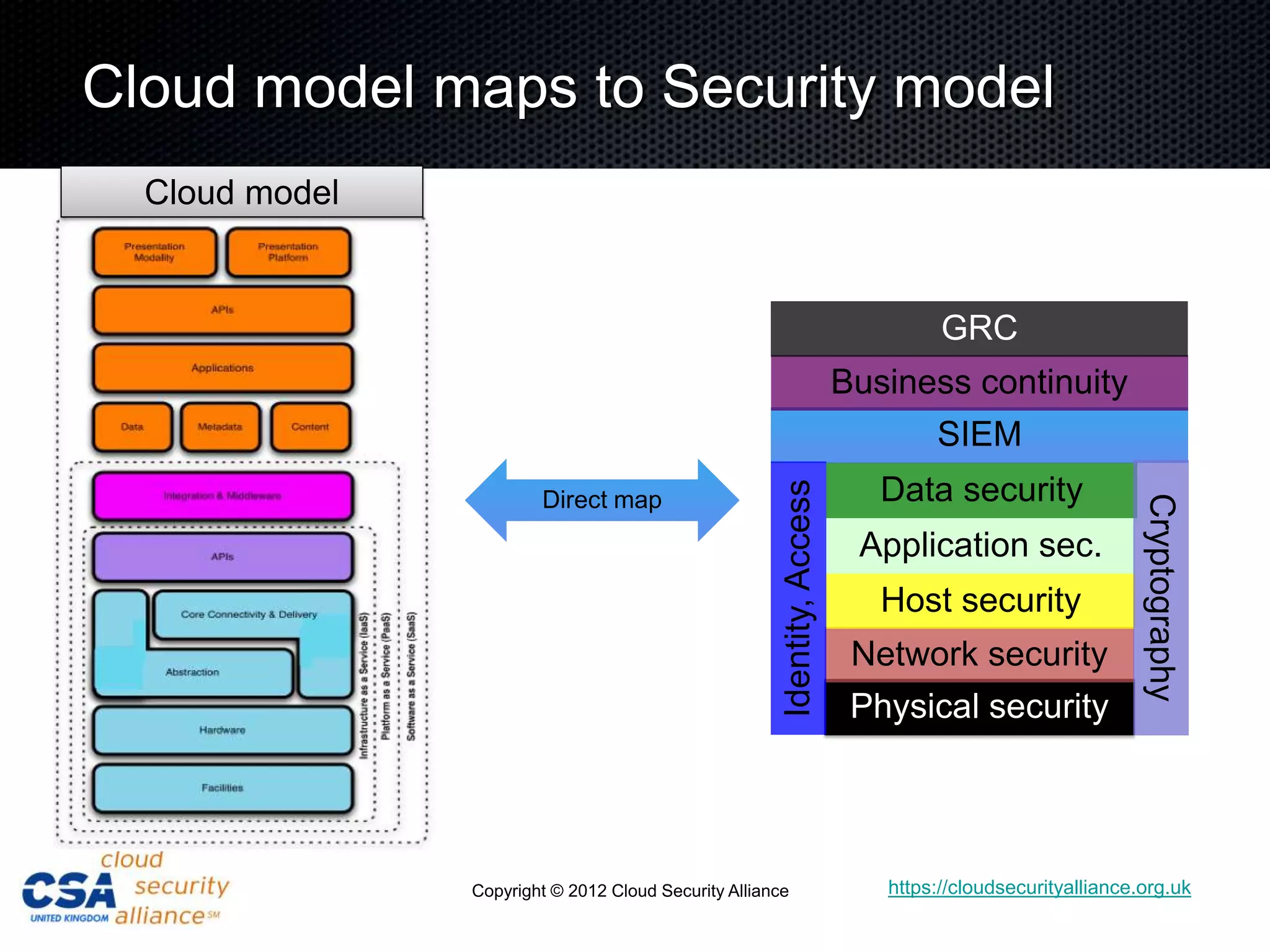
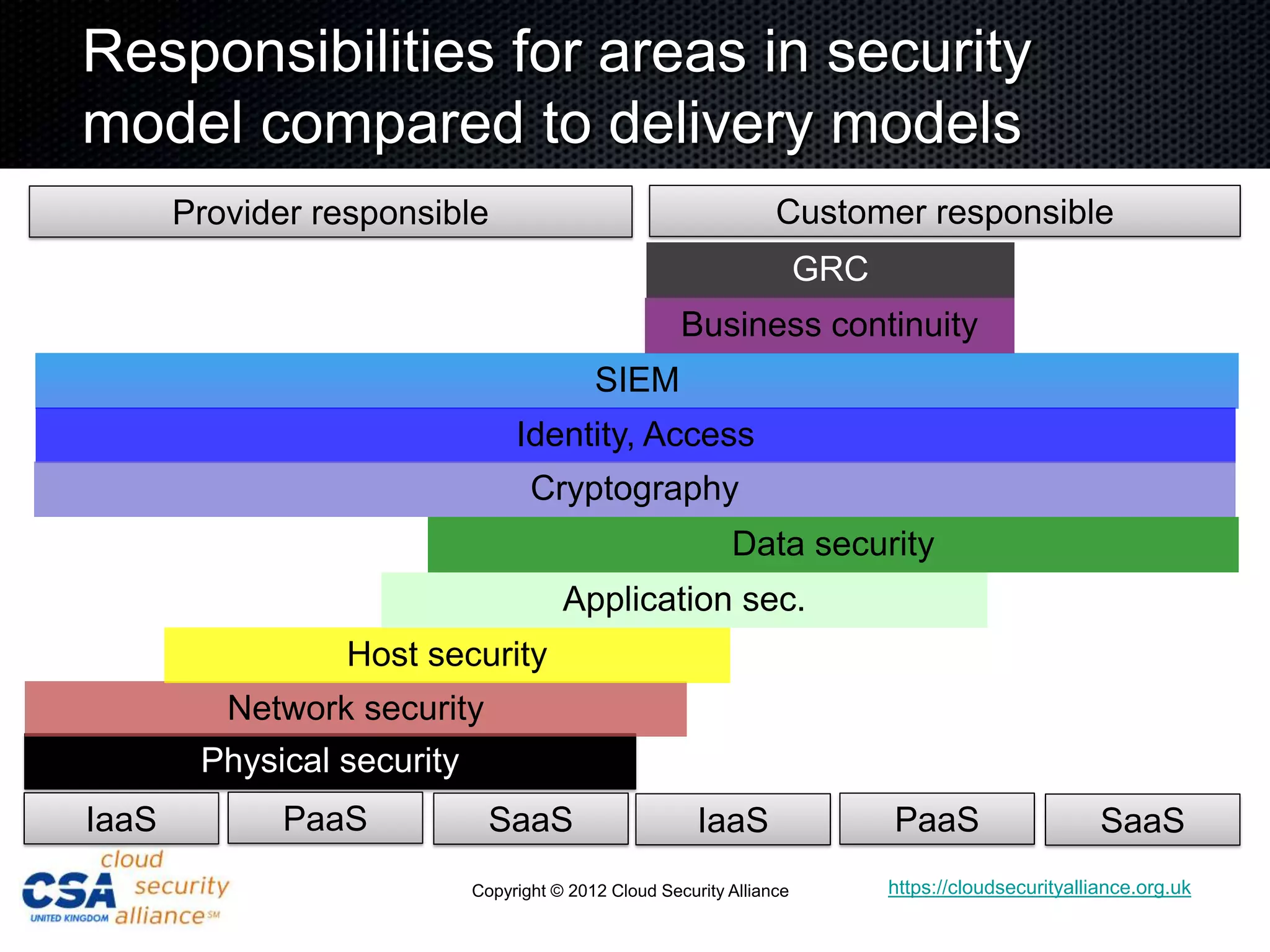
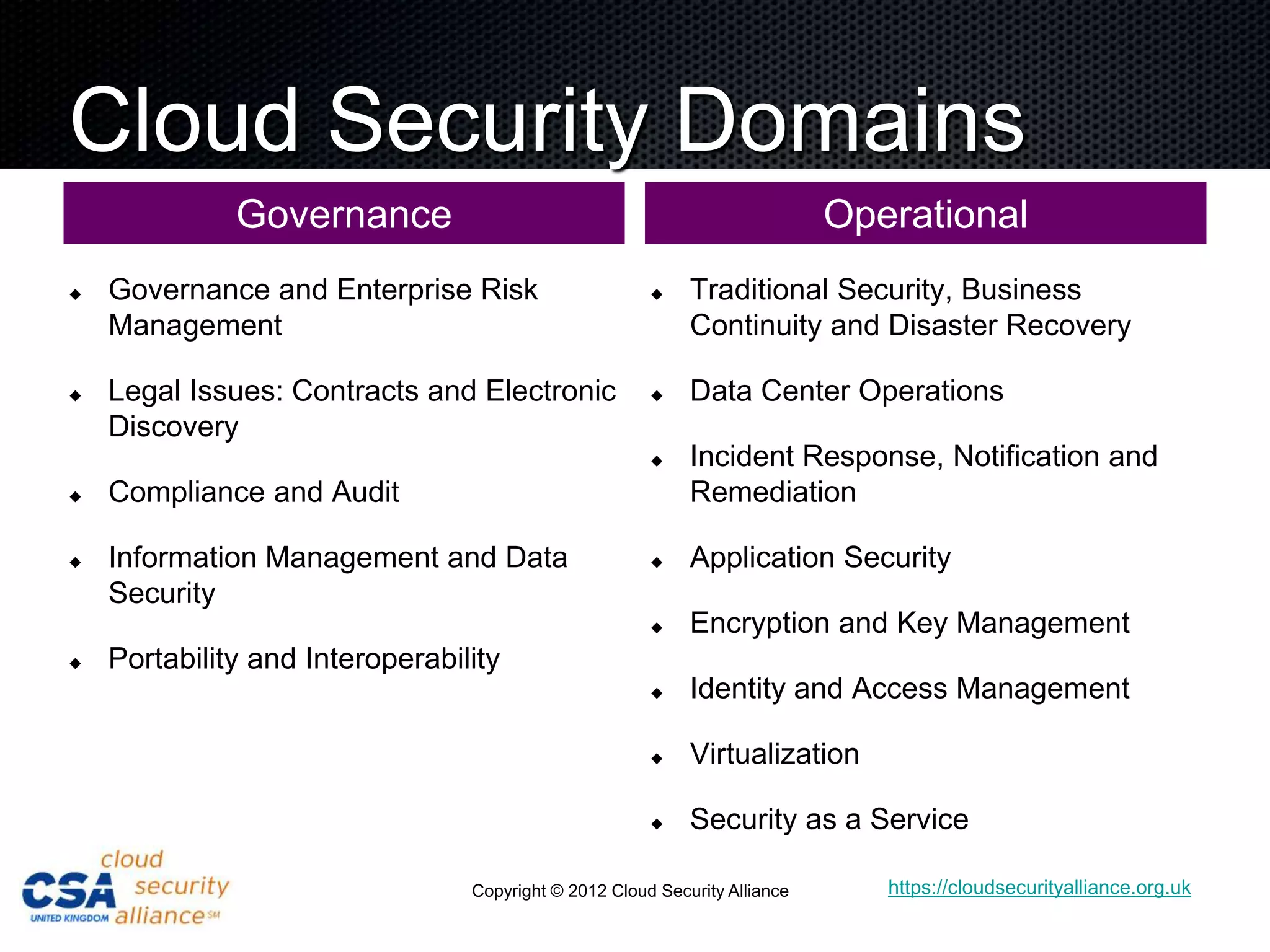
This document discusses security architecture in cloud computing. It provides an overview of cloud risk assessments and how they differ from traditional assessments. It also compares cloud security architectures to traditional security architectures. Finally, it outlines the key domains covered by the Cloud Security Alliance, including governance, operations, and others.