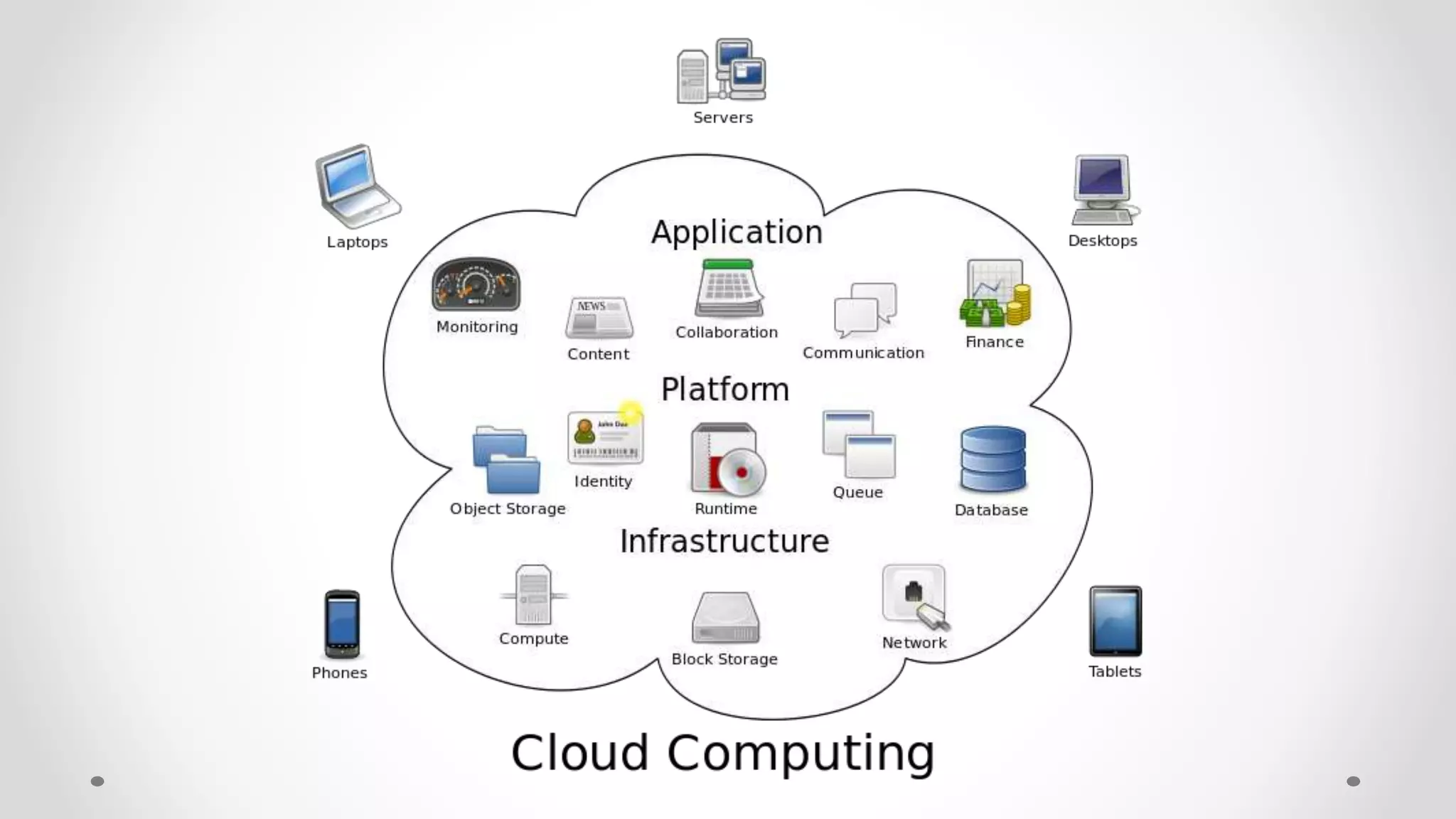
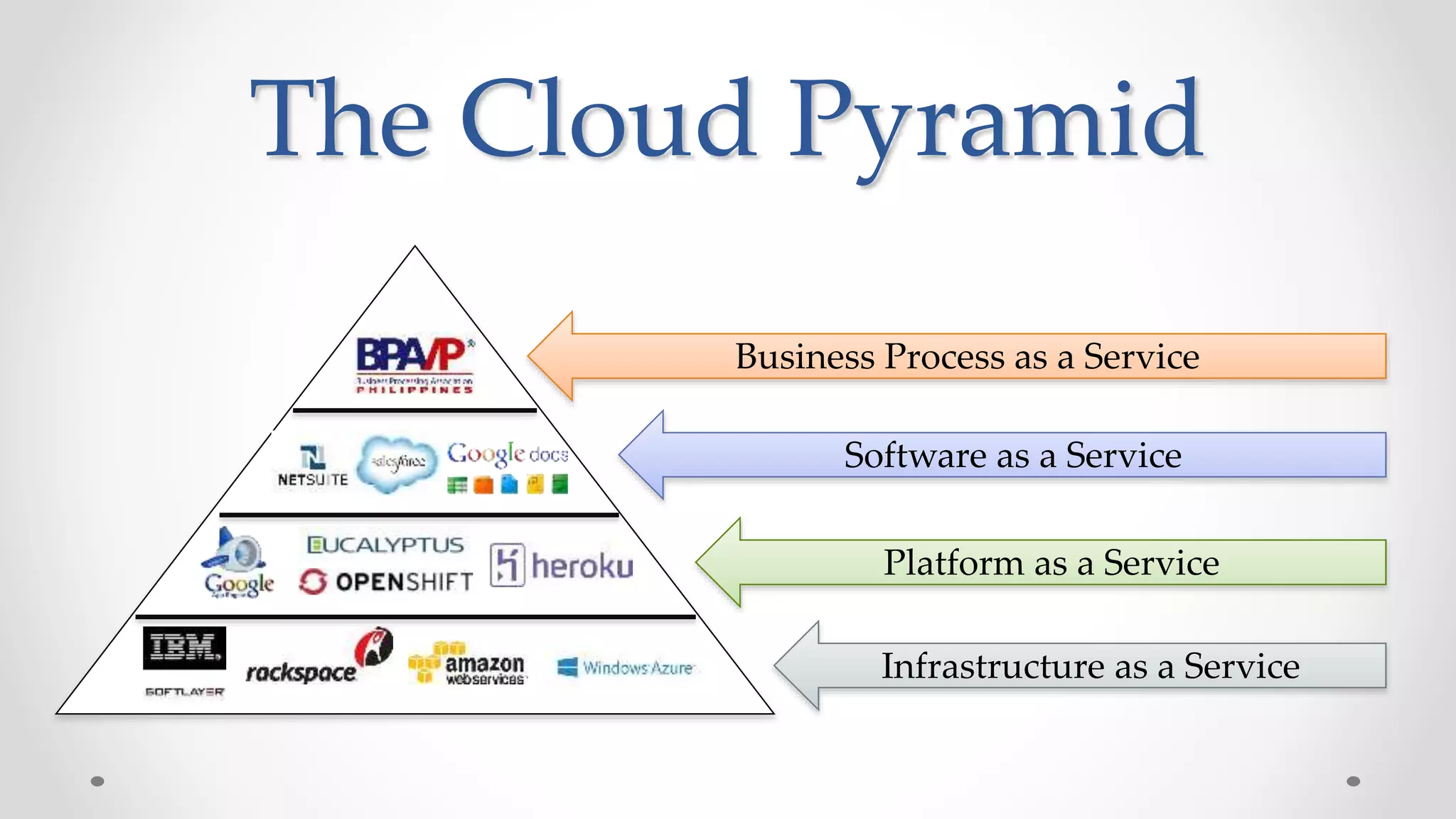
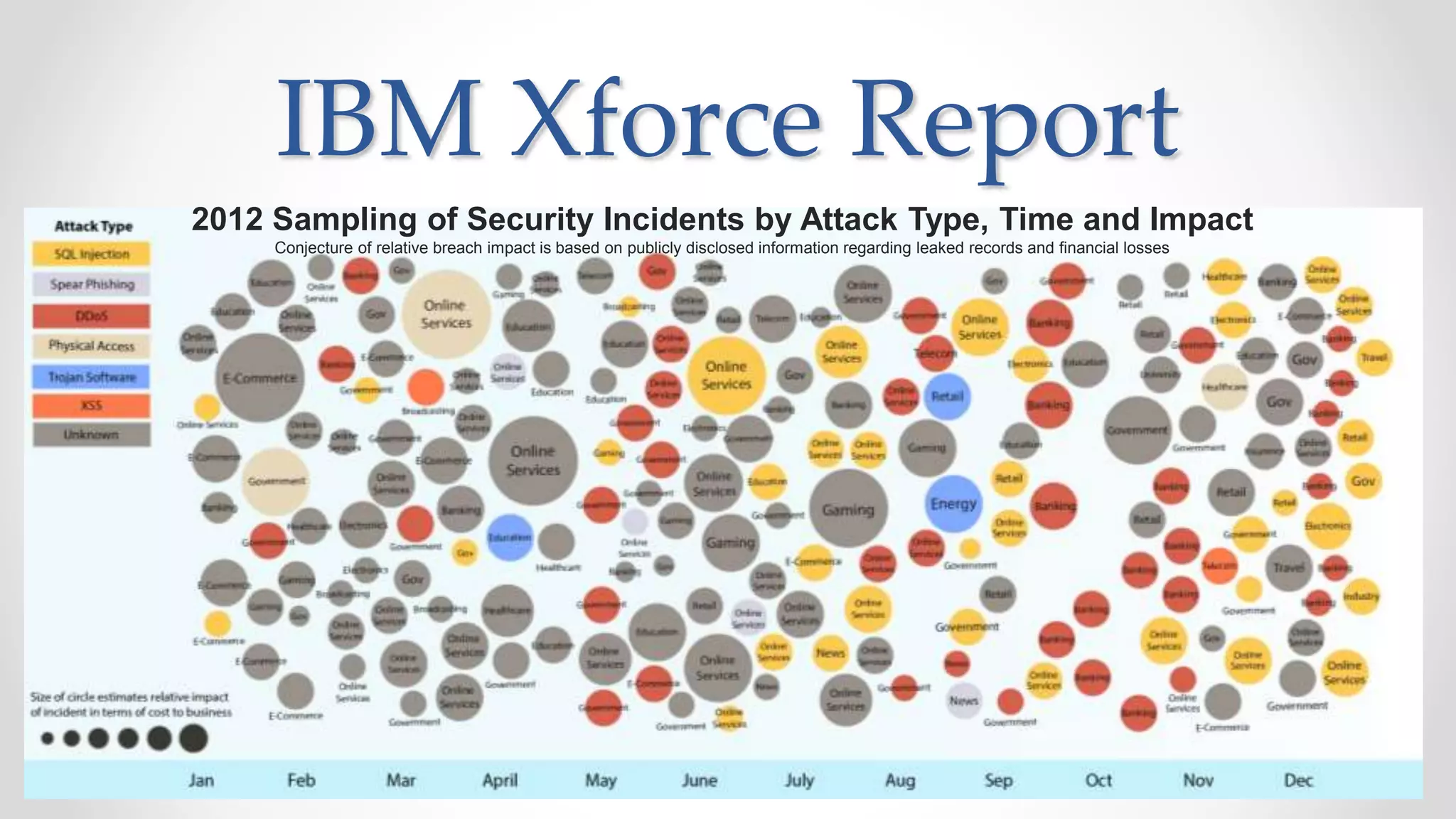
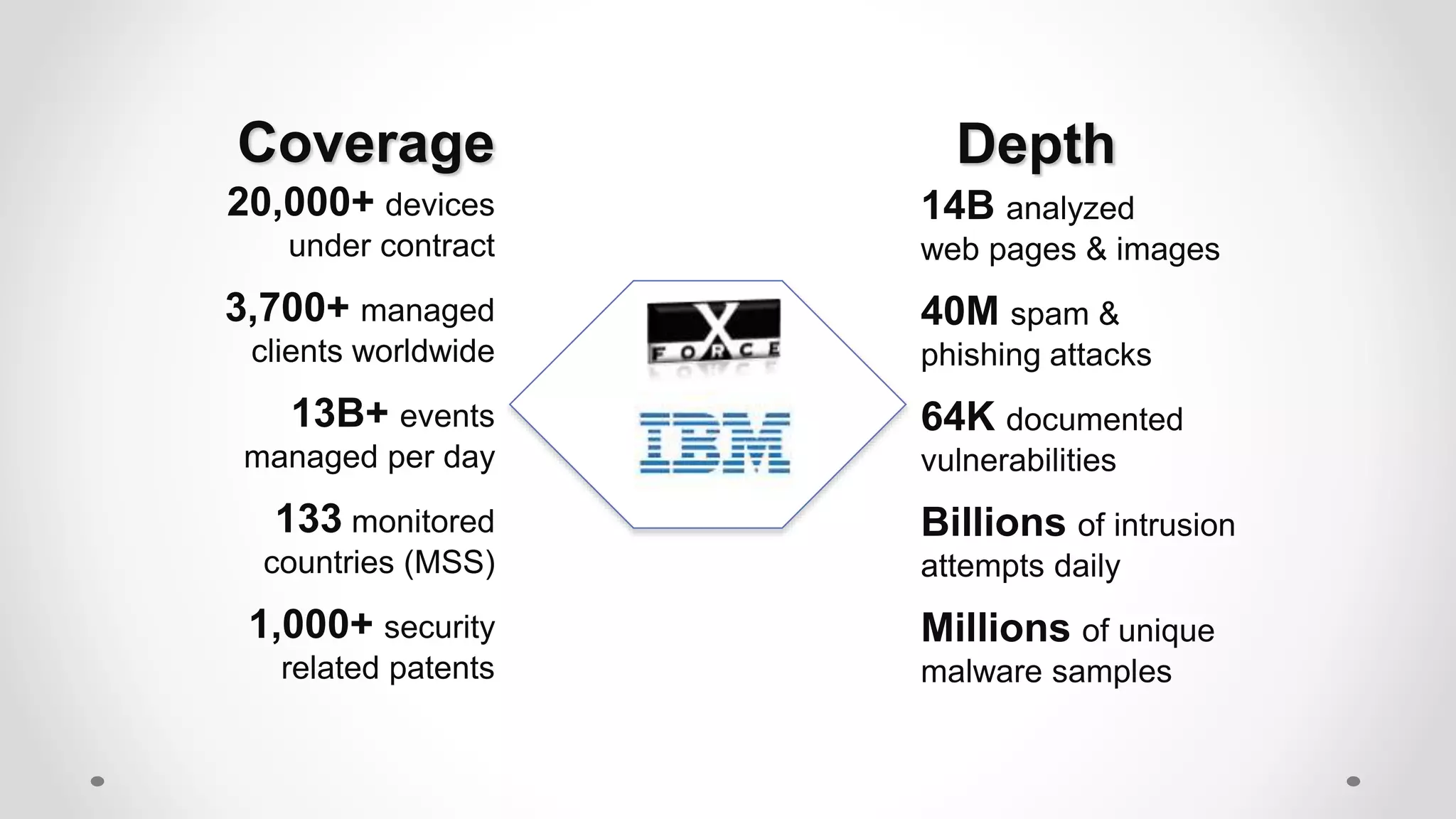
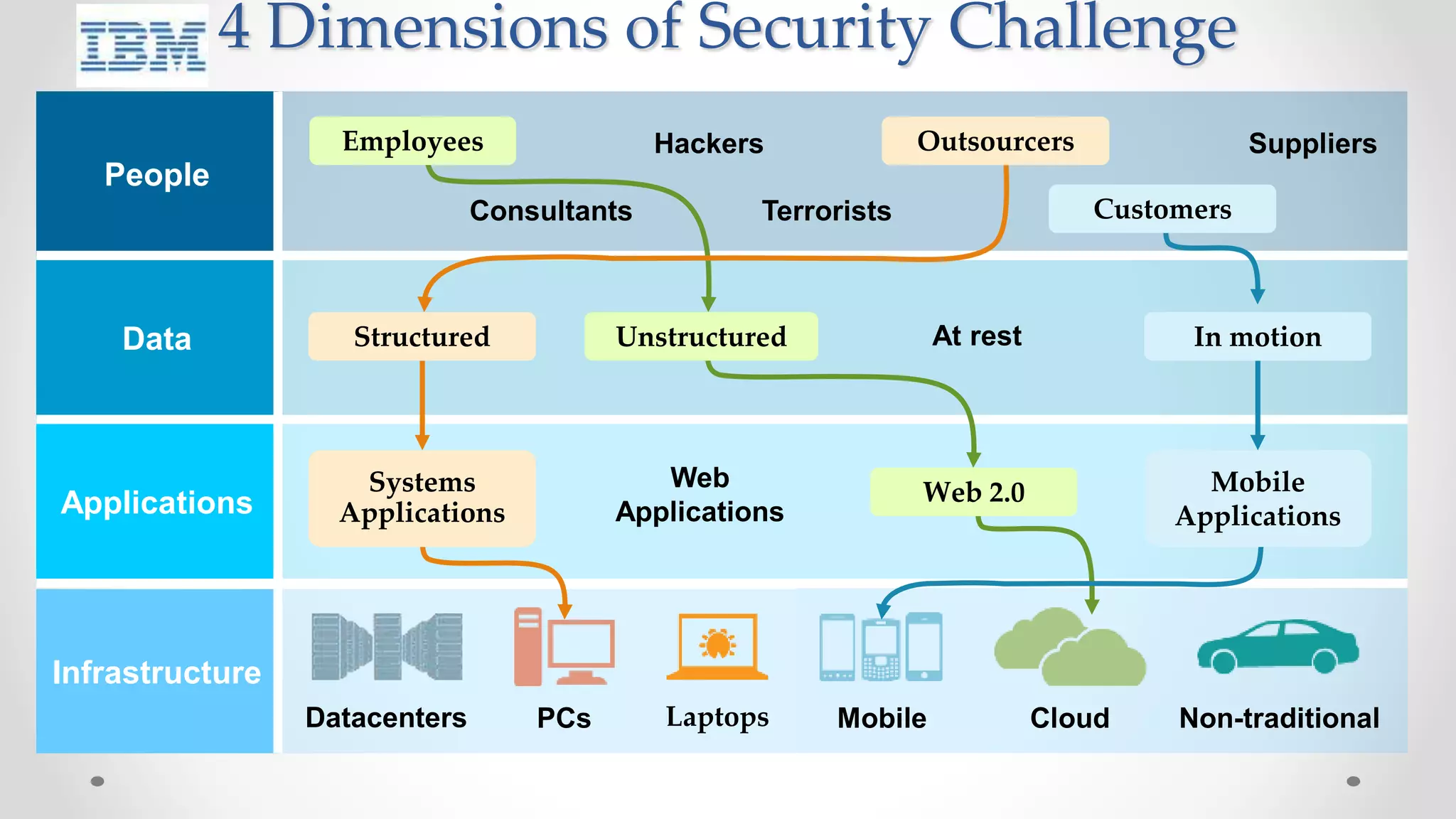
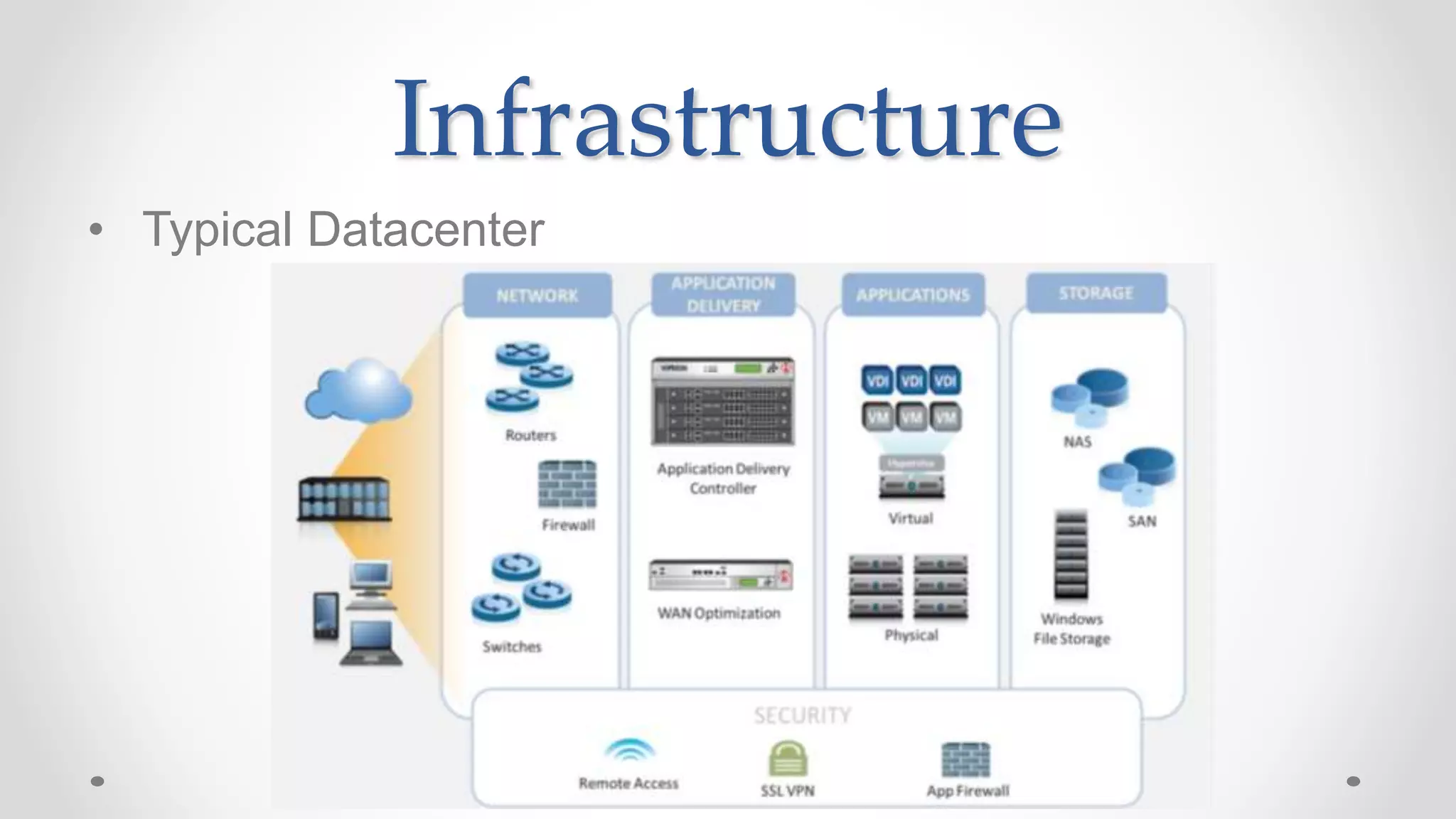
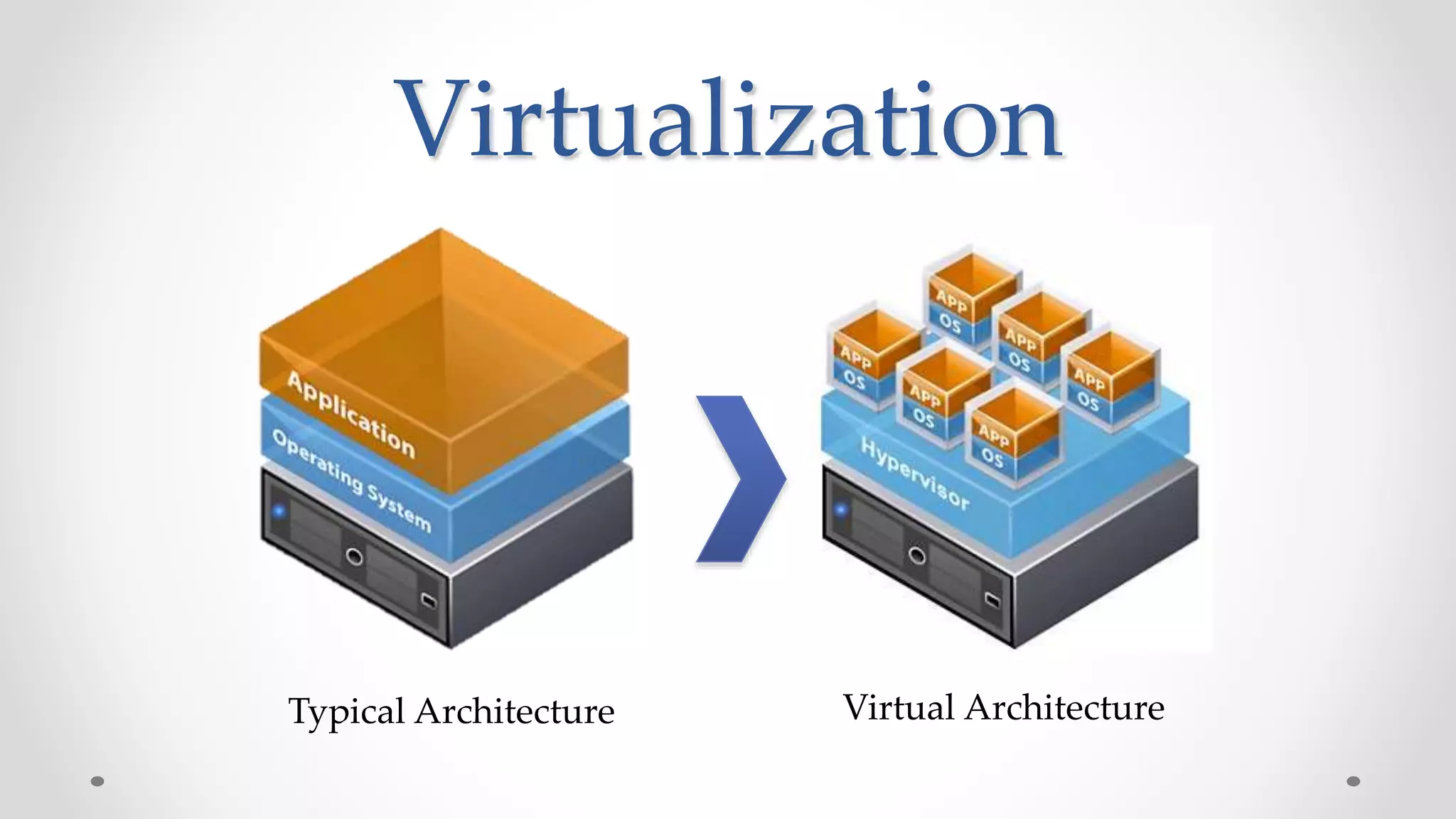
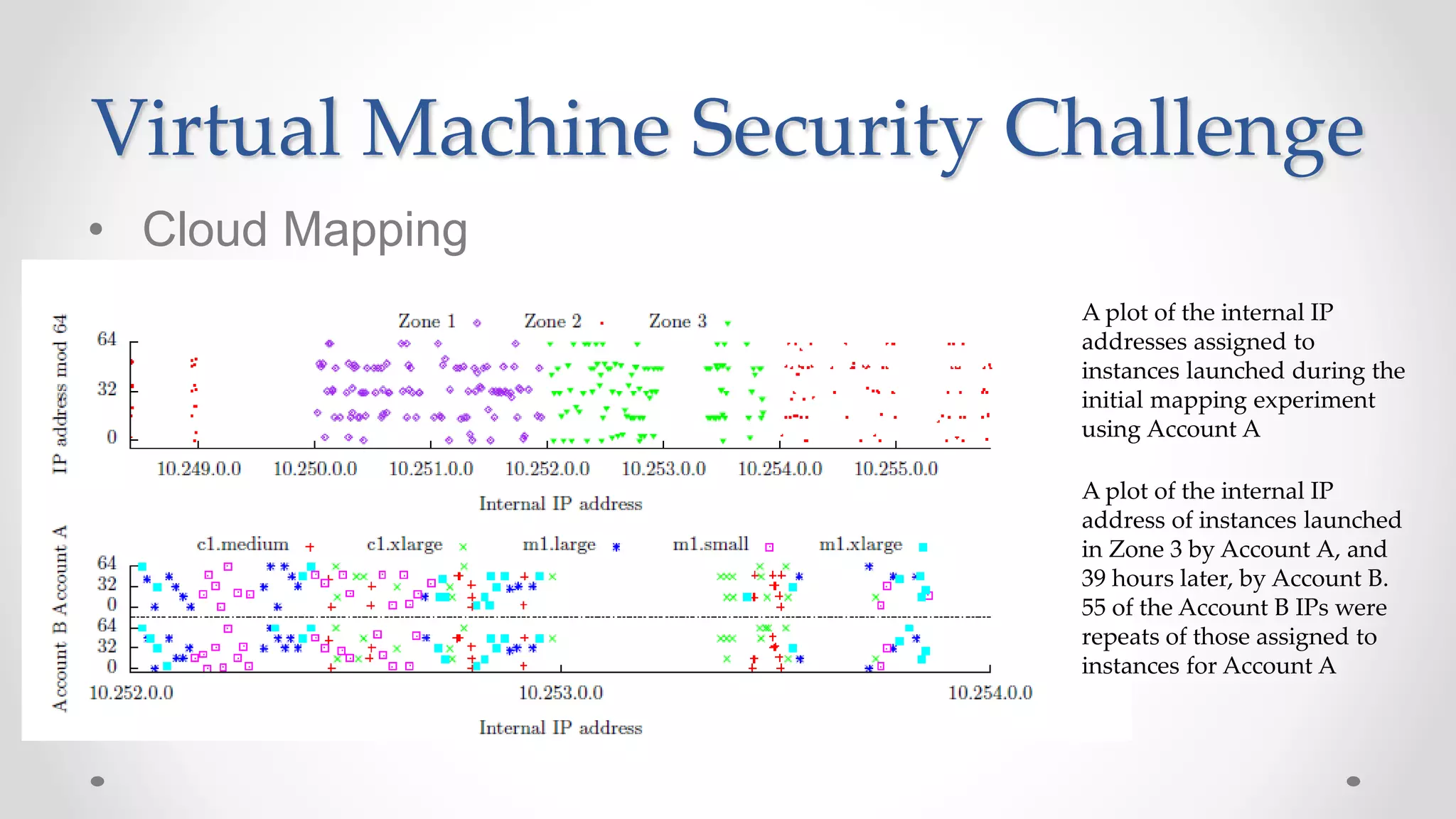
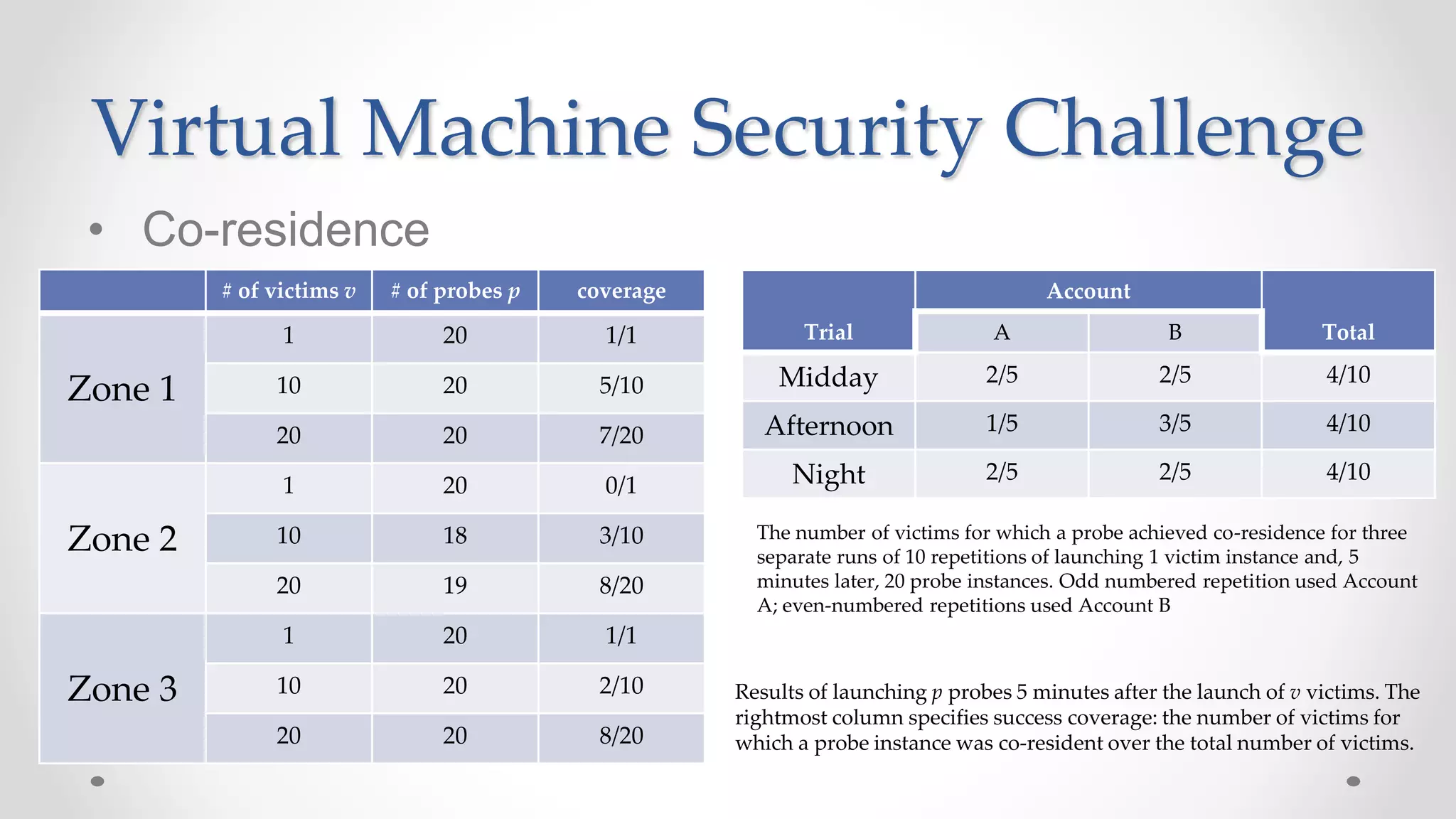
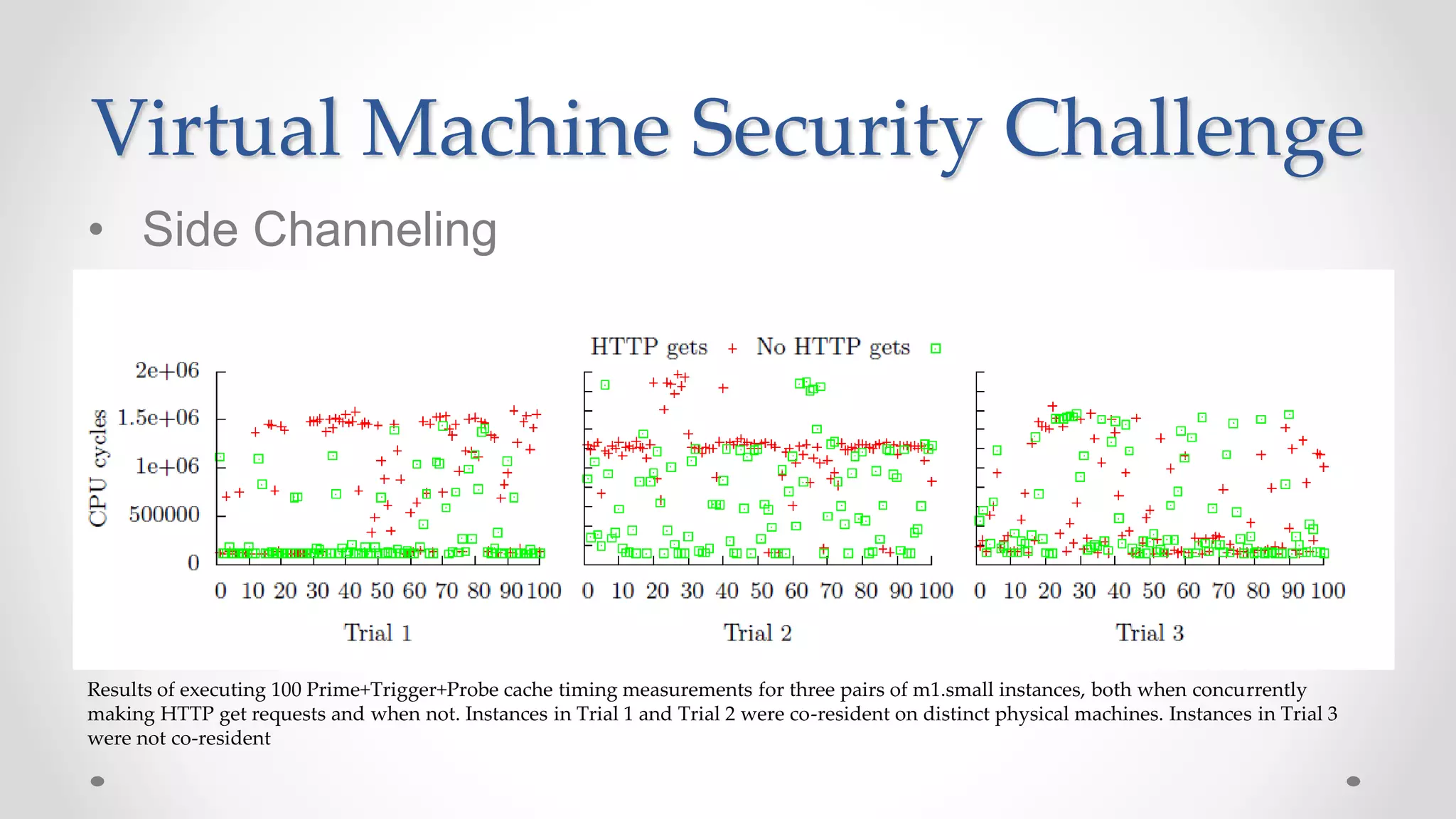
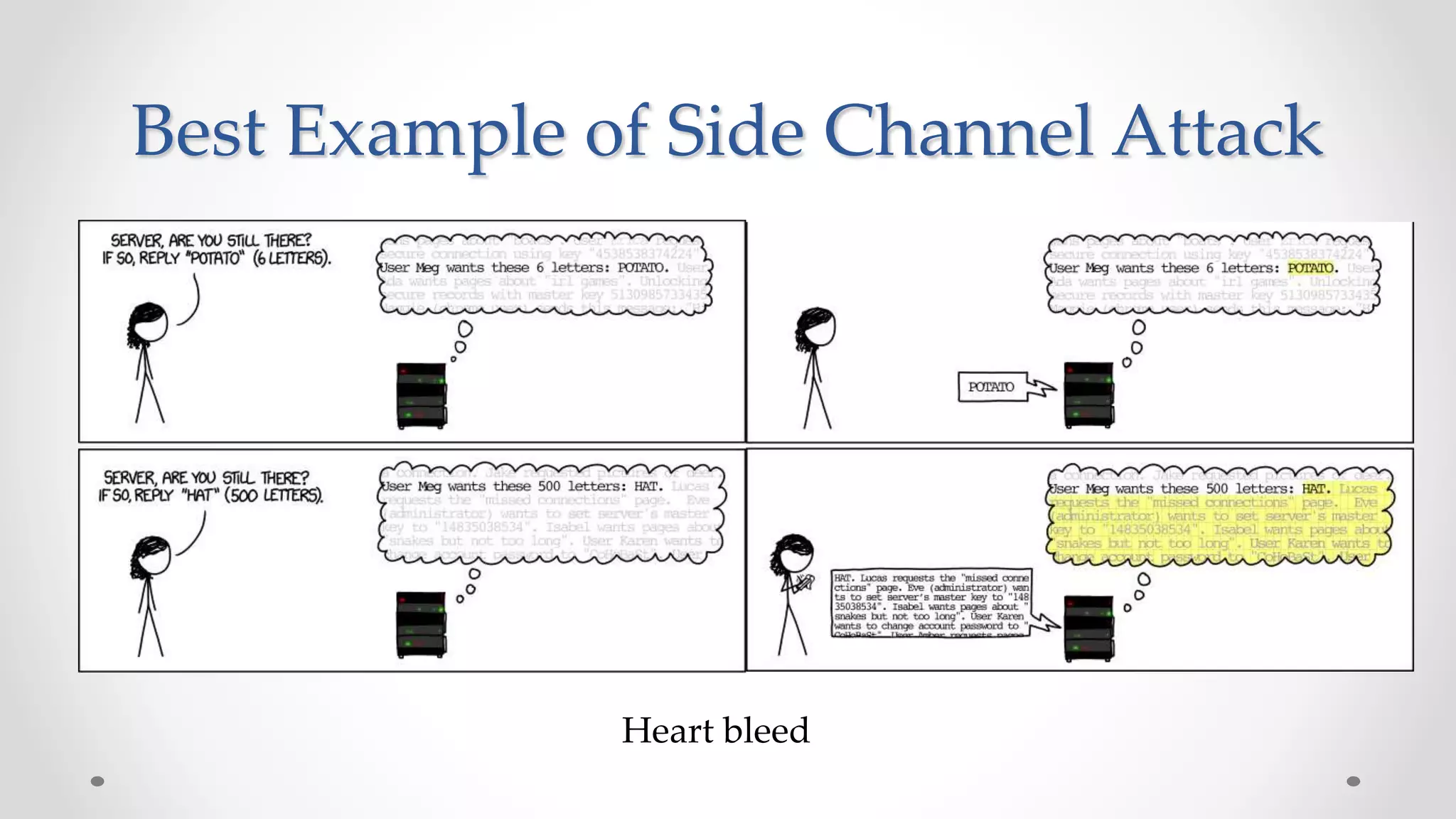
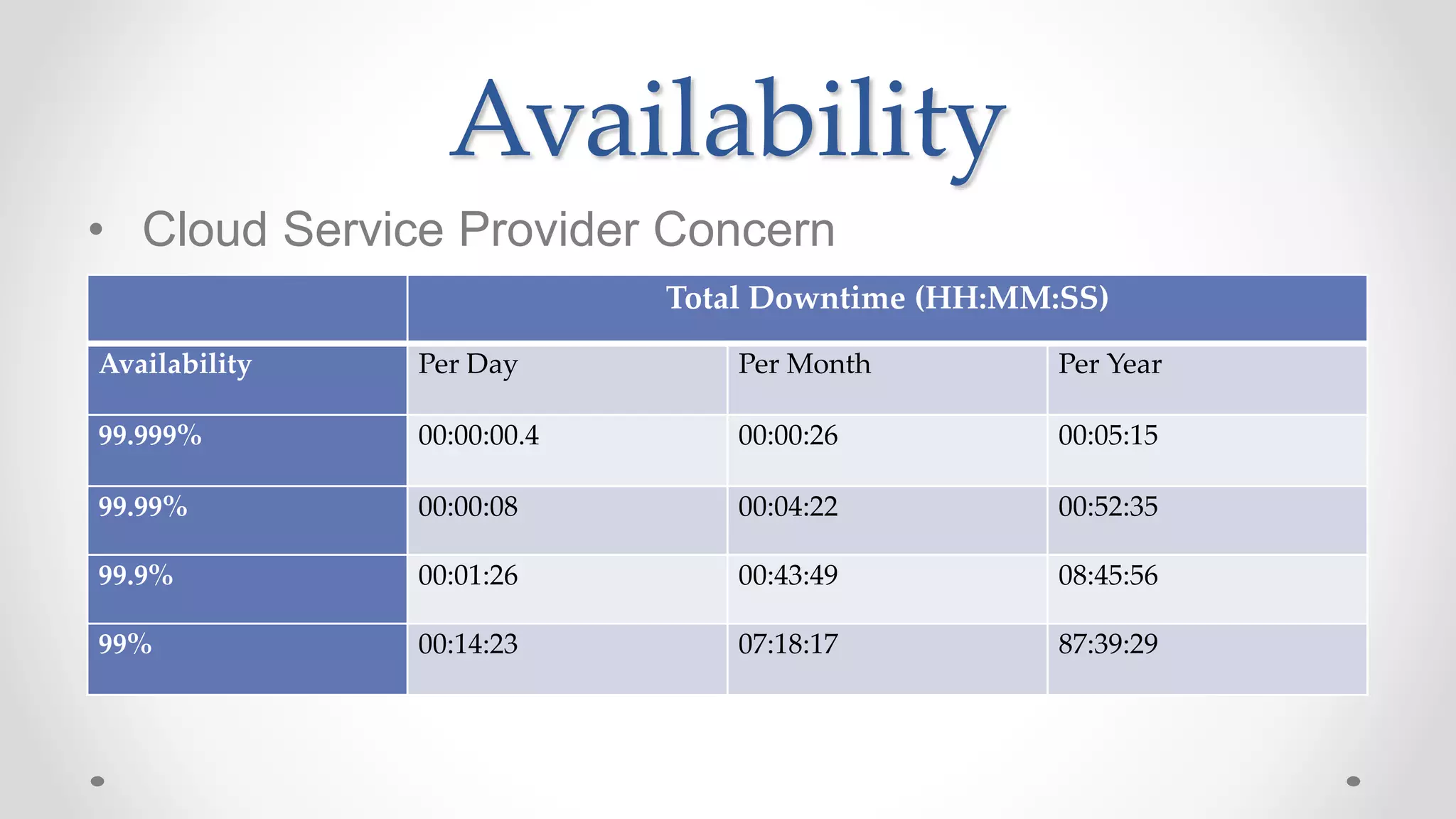
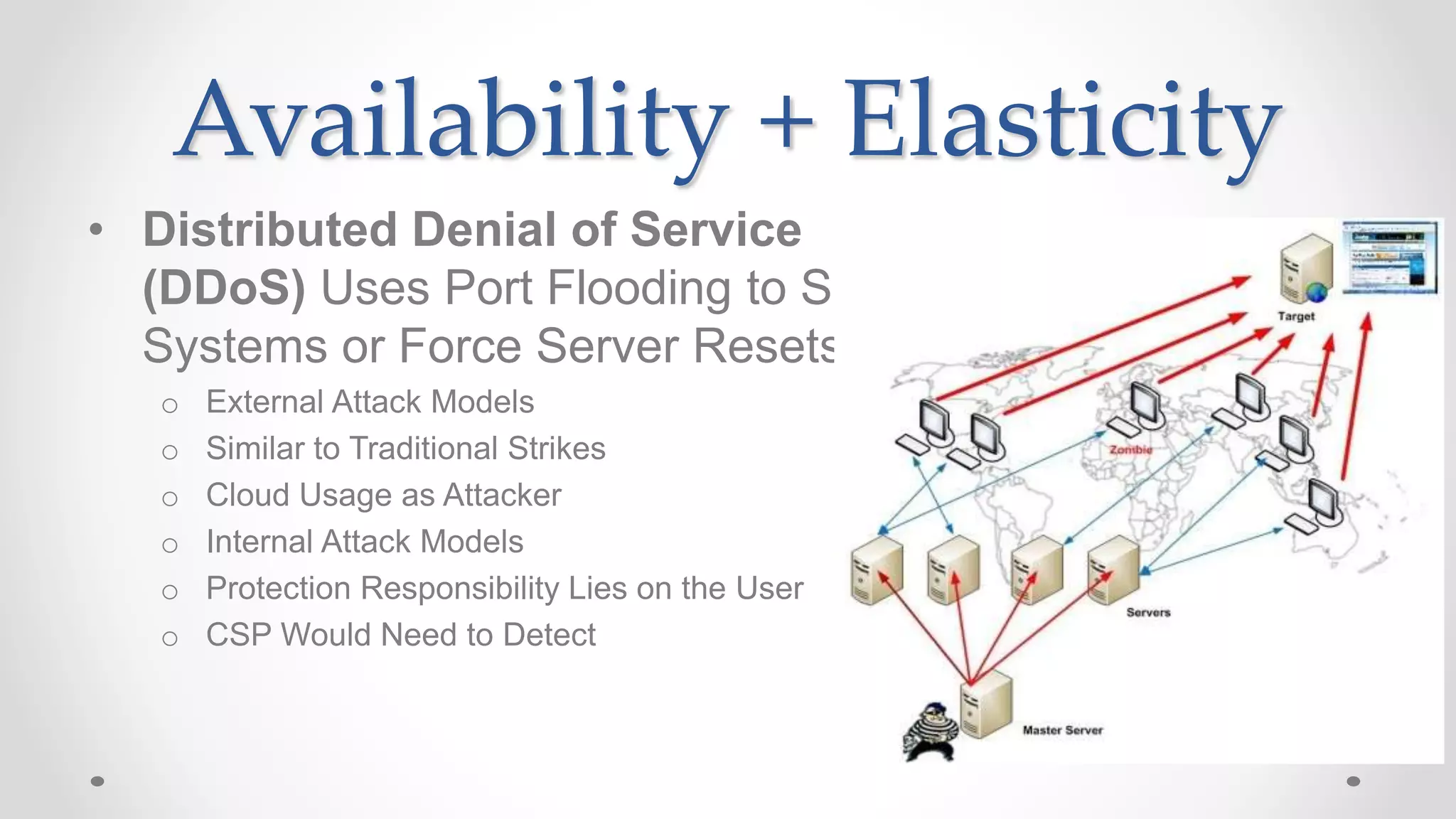
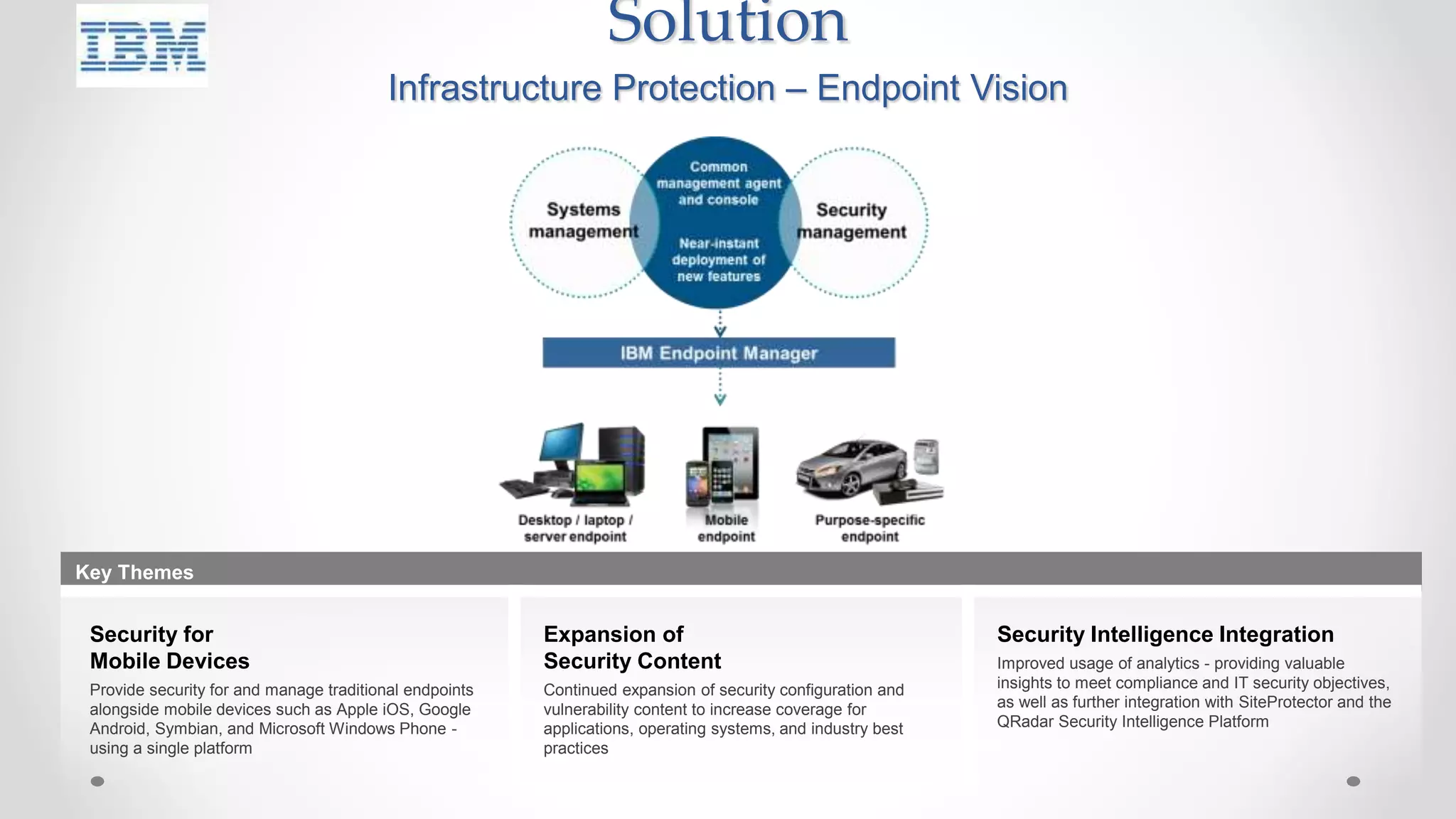
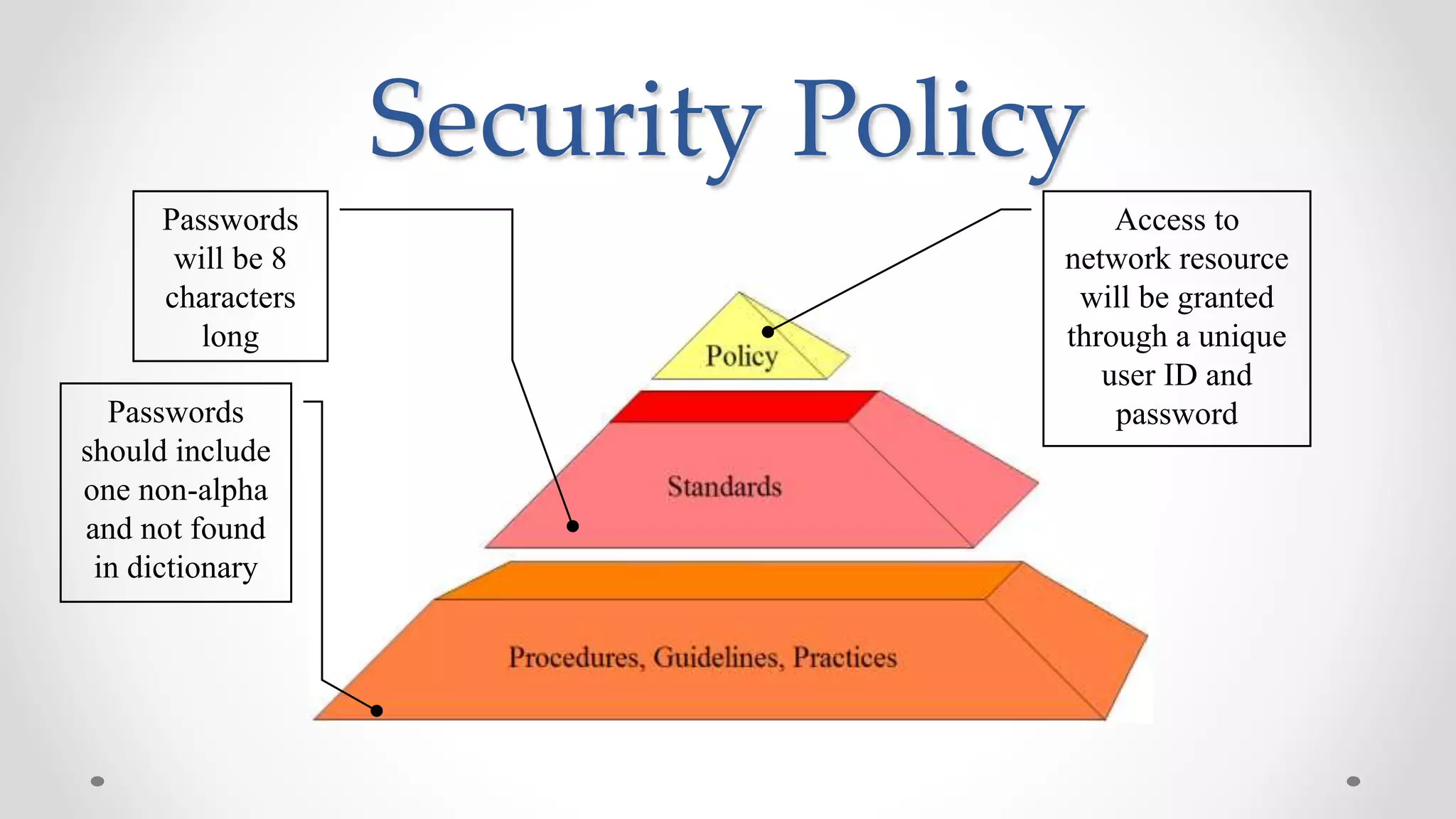
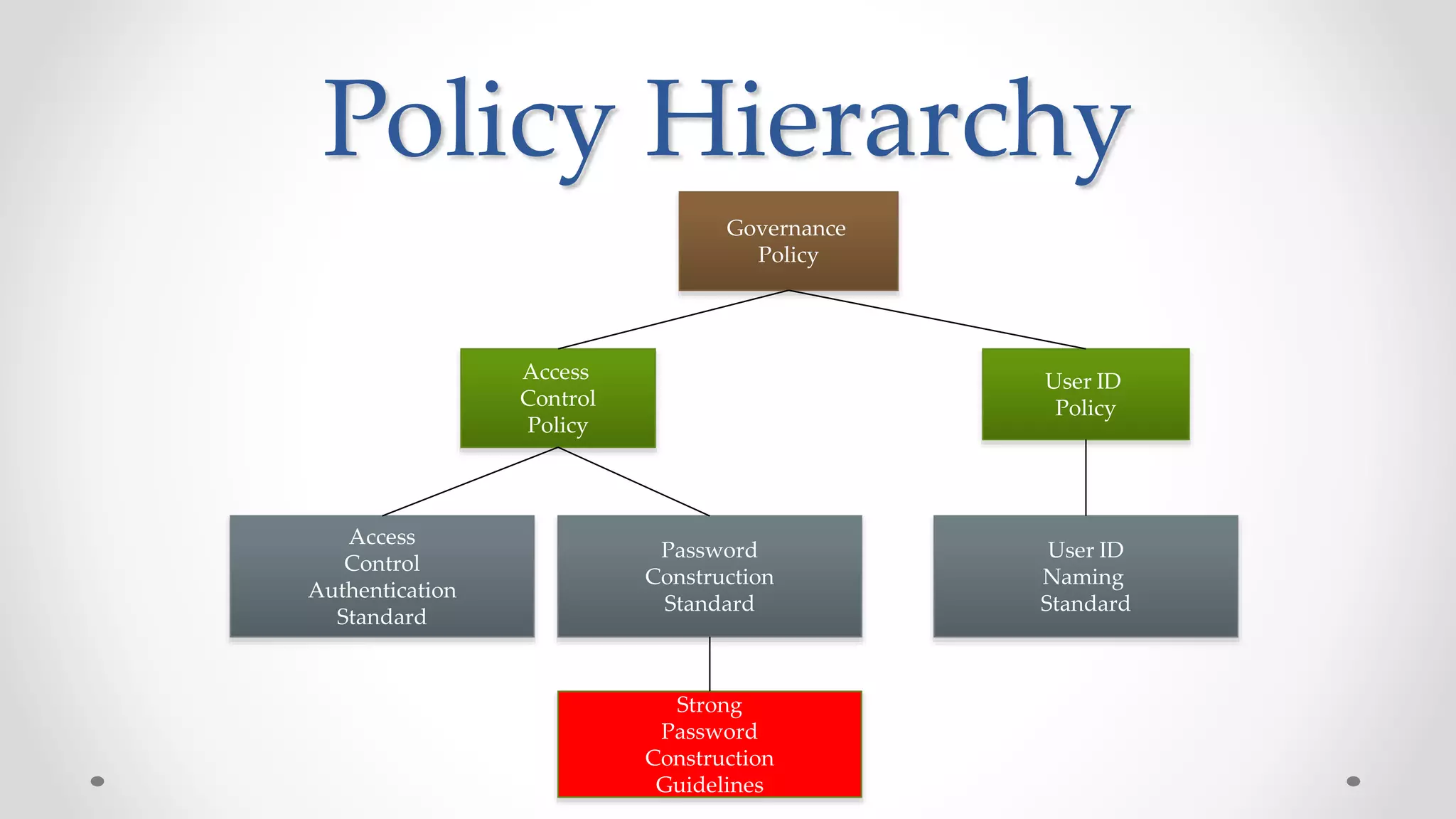
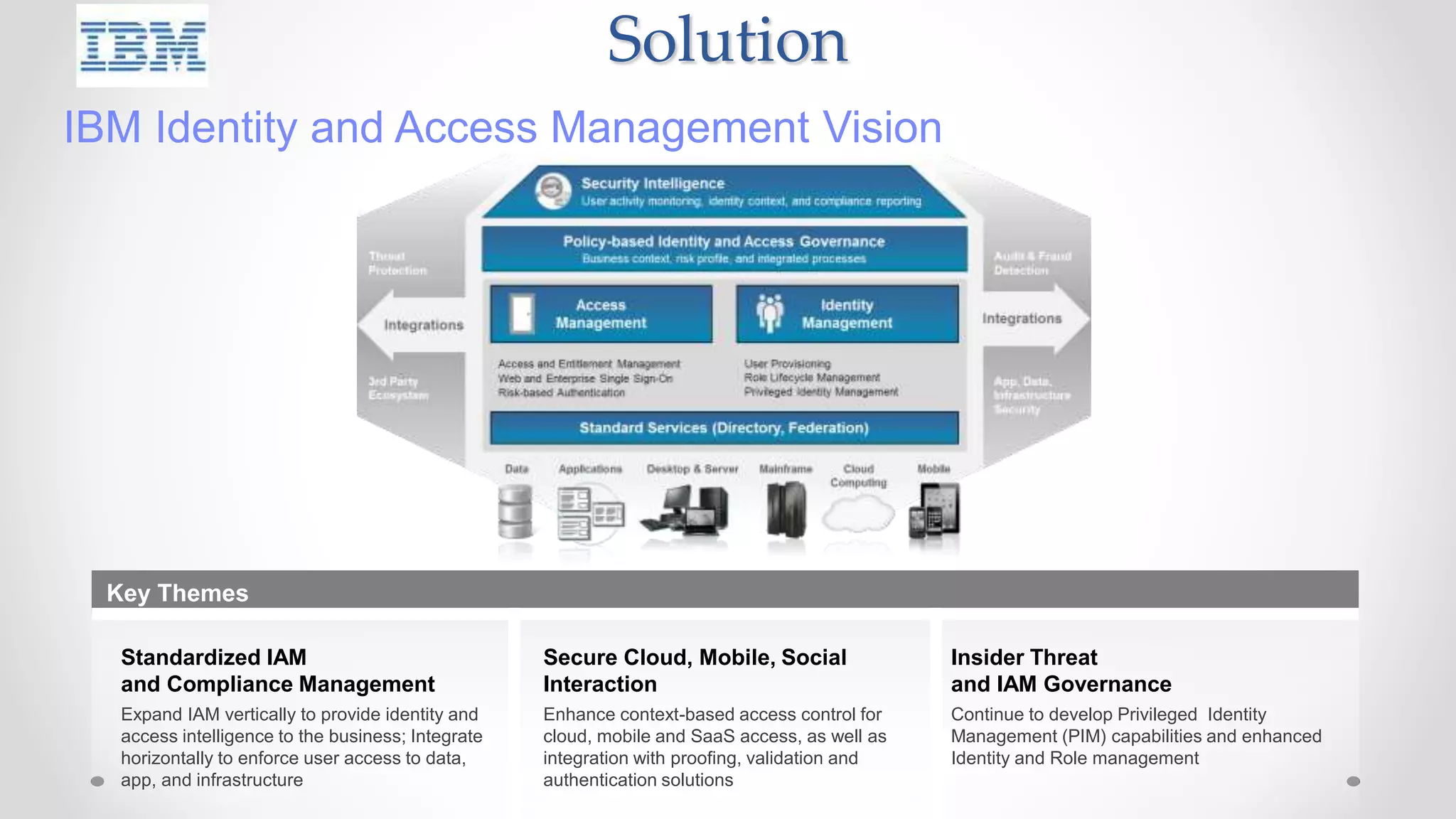
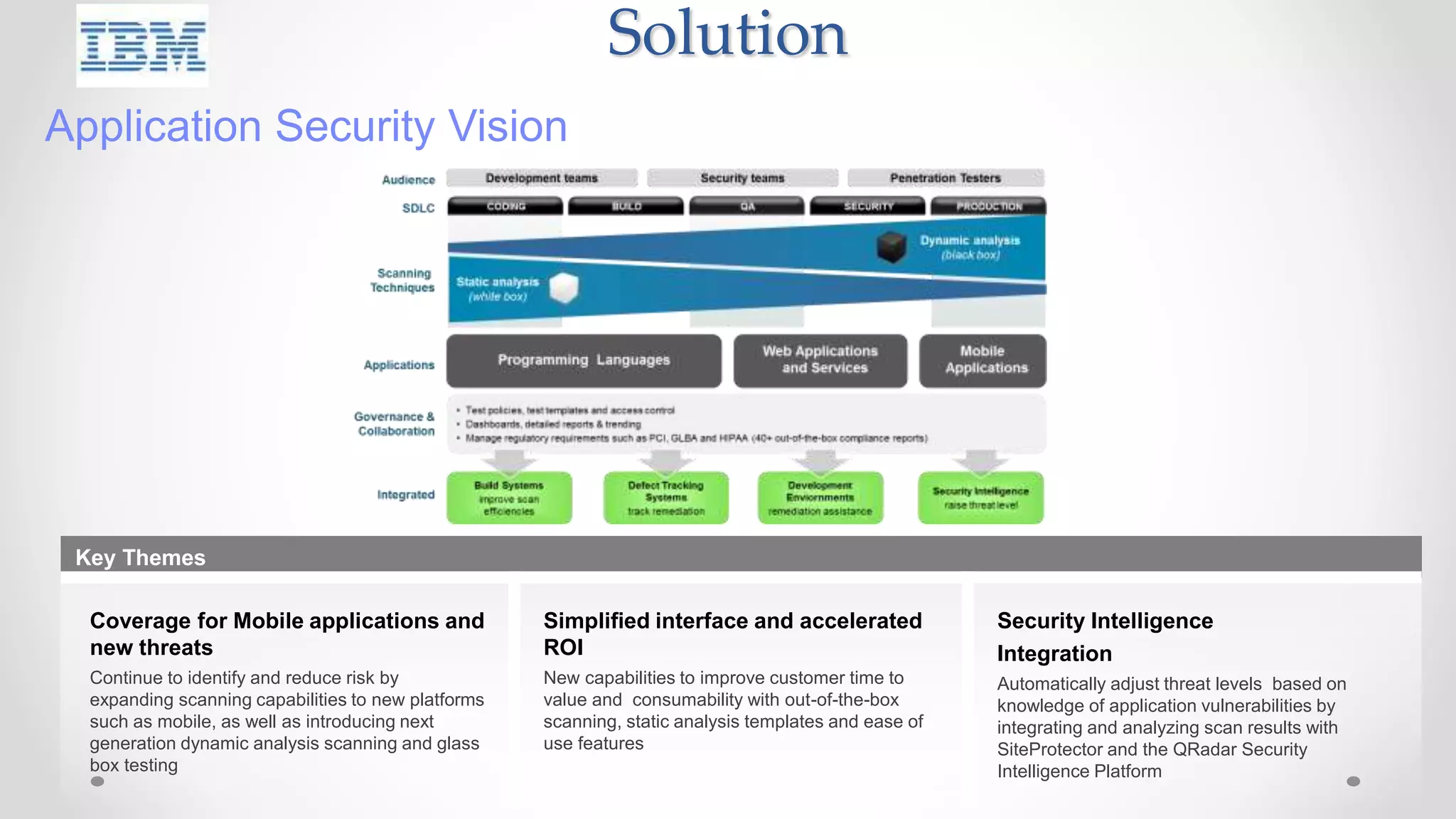
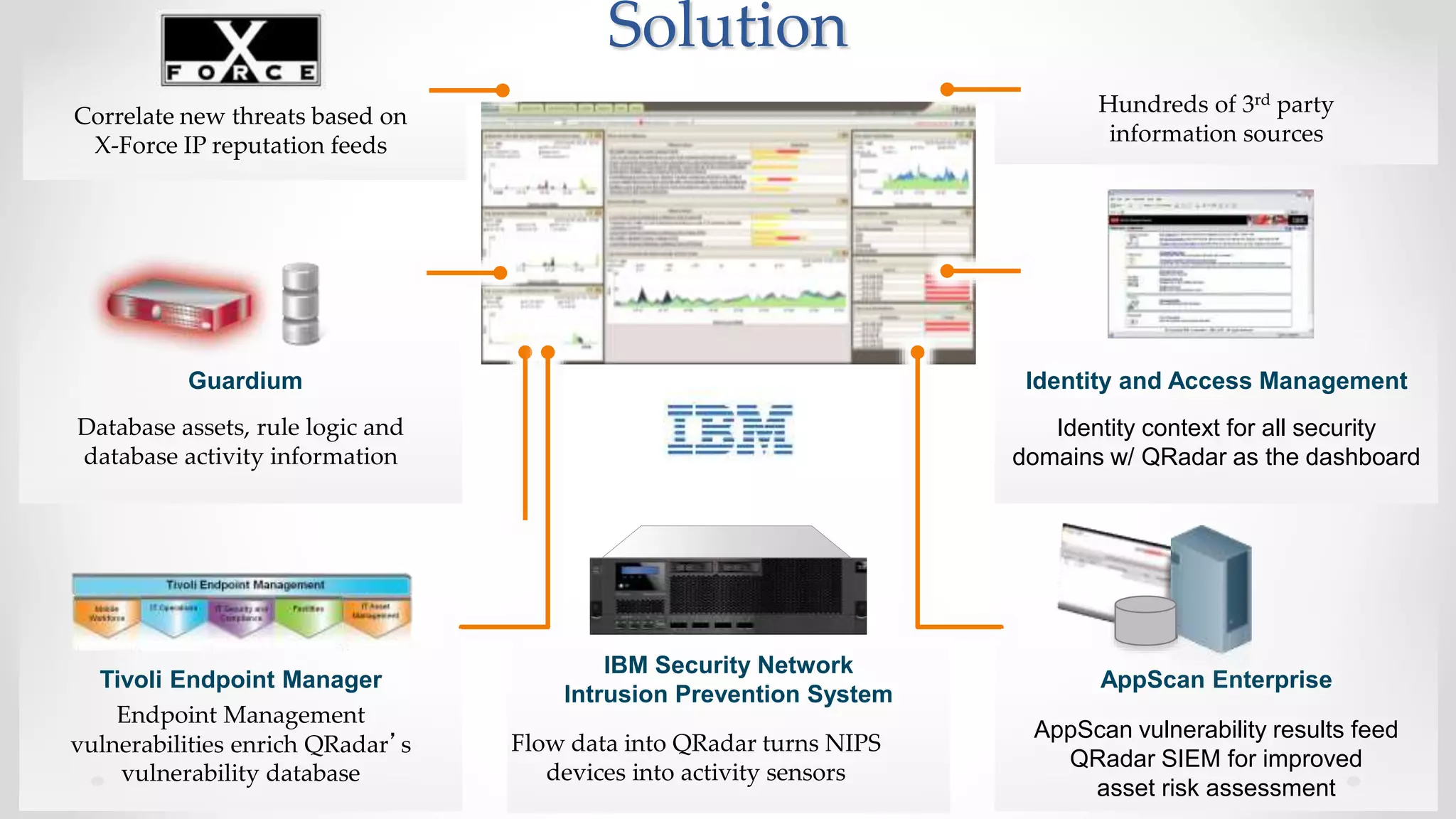
The document discusses the concept of cloud computing, detailing the various types of services it offers (IaaS, PaaS, SaaS, etc.) and highlighting security challenges such as data integrity, availability, and co-residence risks. It emphasizes the importance of security policies and awareness in managing these challenges, alongside discussing techniques for mitigating security threats in cloud environments. Additionally, it covers the necessity for robust identity and access management strategies to protect both traditional and mobile endpoints.