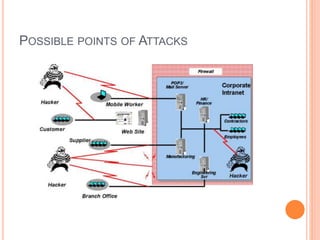
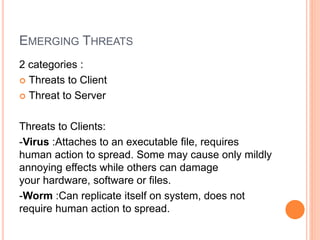
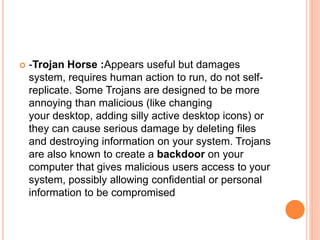
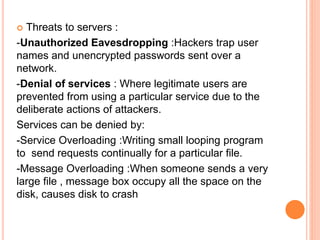
This document discusses security threats in client-server networks. It identifies several types of security risks like unauthorized access, insider threats, and intercepted communications. Specific threats to clients include viruses, worms, and Trojan horses, while threats to servers involve eavesdropping, denial of service attacks through overloading or packet modification. The document then outlines some methods to protect against these threats, such as trust-based security, security through obscurity, password schemes, and biometric systems.