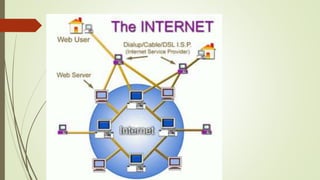
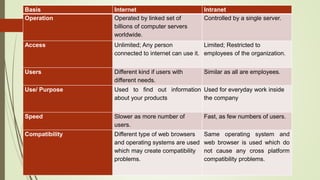
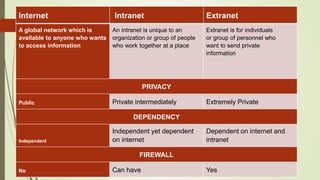
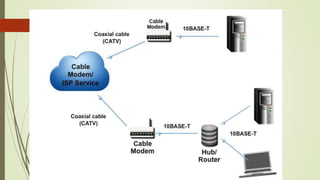
The Internet is a global system of interconnected computer networks that use the Internet protocol suite to link devices worldwide. It was created by the US Department of Defense in the 1960s but has since grown to be a public, self-sustaining facility. An intranet is a private network that uses Internet protocols to securely share part of a company's information or operations, while an extranet extends an intranet to external users for specific limited collaboration. Internet service providers give customers access to the Internet for a monthly fee. Common types of connections include broadband, cable, dial-up, DSL, fiber, and wireless.