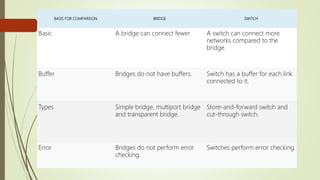
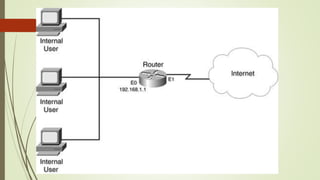
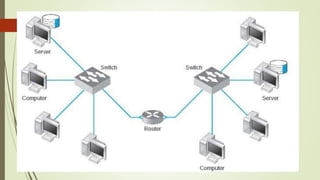
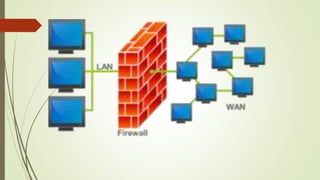
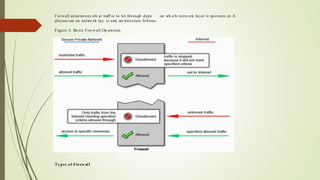
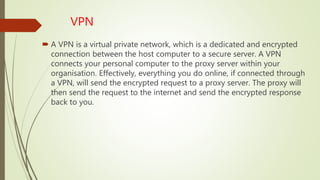
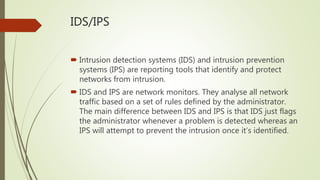
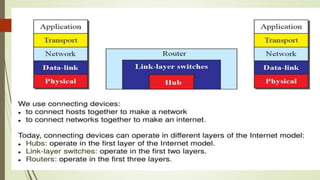
Network devices like hubs, switches, and routers connect computers in a network and help manage traffic flow. Hubs broadcast all received data to all ports but have limited bandwidth. Switches can connect more devices than hubs and have features like VLANs. Routers connect different networks and use IP addresses to direct traffic. Other devices like firewalls, VPNs, and IDS/IPS provide network security functions.














![Advantages :
1) Reduces the number of Broadcast domains
2) Supports VLAN's which can help in Logical segmentation
of ports[physical ports].Splitting up the broadcast domain.
3) Intellegent device[compared to Hub's] which can make use table
for Port to MAC mapping
4) Compared to Bridges ,Switches are more H/w oriented
therefore operations are less CPU intense[Basic operations]](https://image.slidesharecdn.com/unit5-190409094326/85/Network-Connecting-Devices-UNIT-5-23-320.jpg)
![Disadvantages :
1) Not as good as a router in limiting Broadcasts
2) Communication b/w VLAN's need interVLAN
routing [Router]
,but these days there are a number of Multilayer
switches available in the market.
3) Handling Multicast packets needs quite a bit
of configuration & proper designing.](https://image.slidesharecdn.com/unit5-190409094326/85/Network-Connecting-Devices-UNIT-5-24-320.jpg)