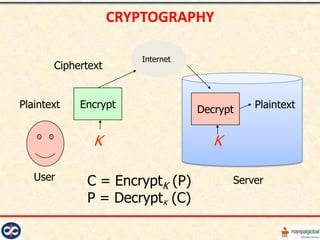
This document outlines IT security procedures and guidelines for data protection. It discusses the objectives of data security including availability, integrity, confidentiality, authenticity and auditability. It describes threats such as accidental damages from environmental hazards or errors, and malicious damages from disgruntled employees or fraudsters. It also covers specific security measures like cryptography, access controls, network security, physical security, document security and biometric authentication. The overall document provides a comprehensive overview of IT security best practices for organizations.