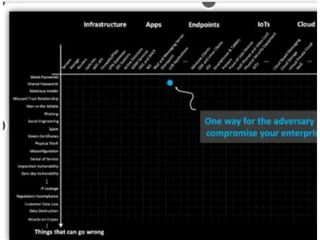
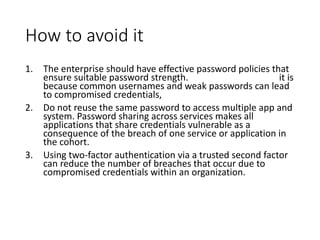
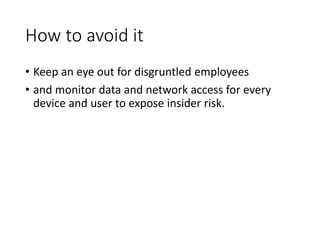
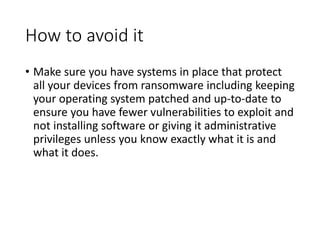
The document discusses computer security and common cyber attack vectors. It defines key terms like attack surface, attack vectors, and security breaches. It then describes 8 common attack vectors: compromised credentials, weak/stolen credentials, malicious insiders, missing/poor encryption, misconfiguration, ransomware, phishing, and trust relationships. Typical symptoms of an attack are also listed, such as slow performance, strange files/programs, and automatic messages. The consequences of a successful attack compromise the goals of computer security - confidentiality, integrity and availability.