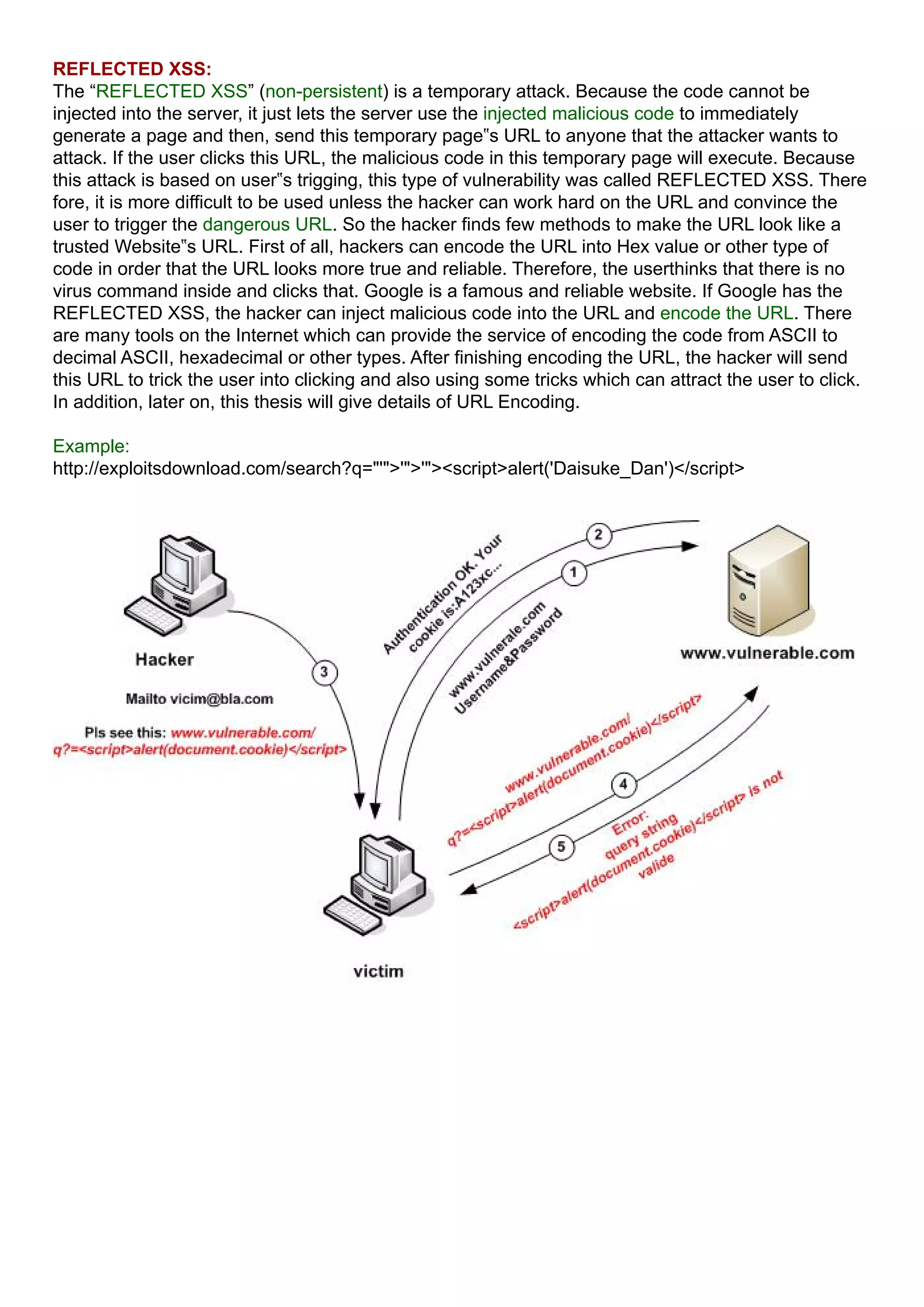
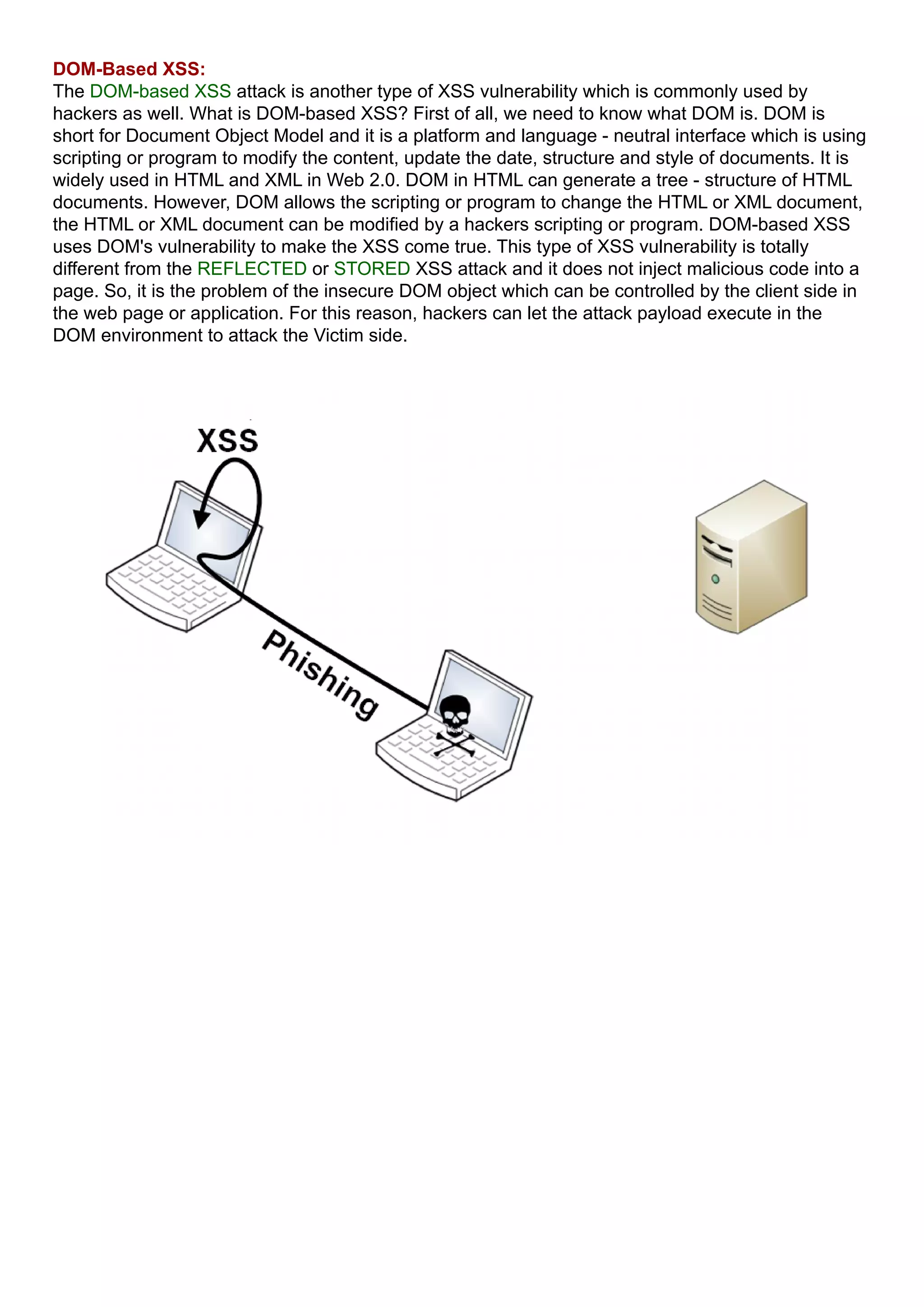
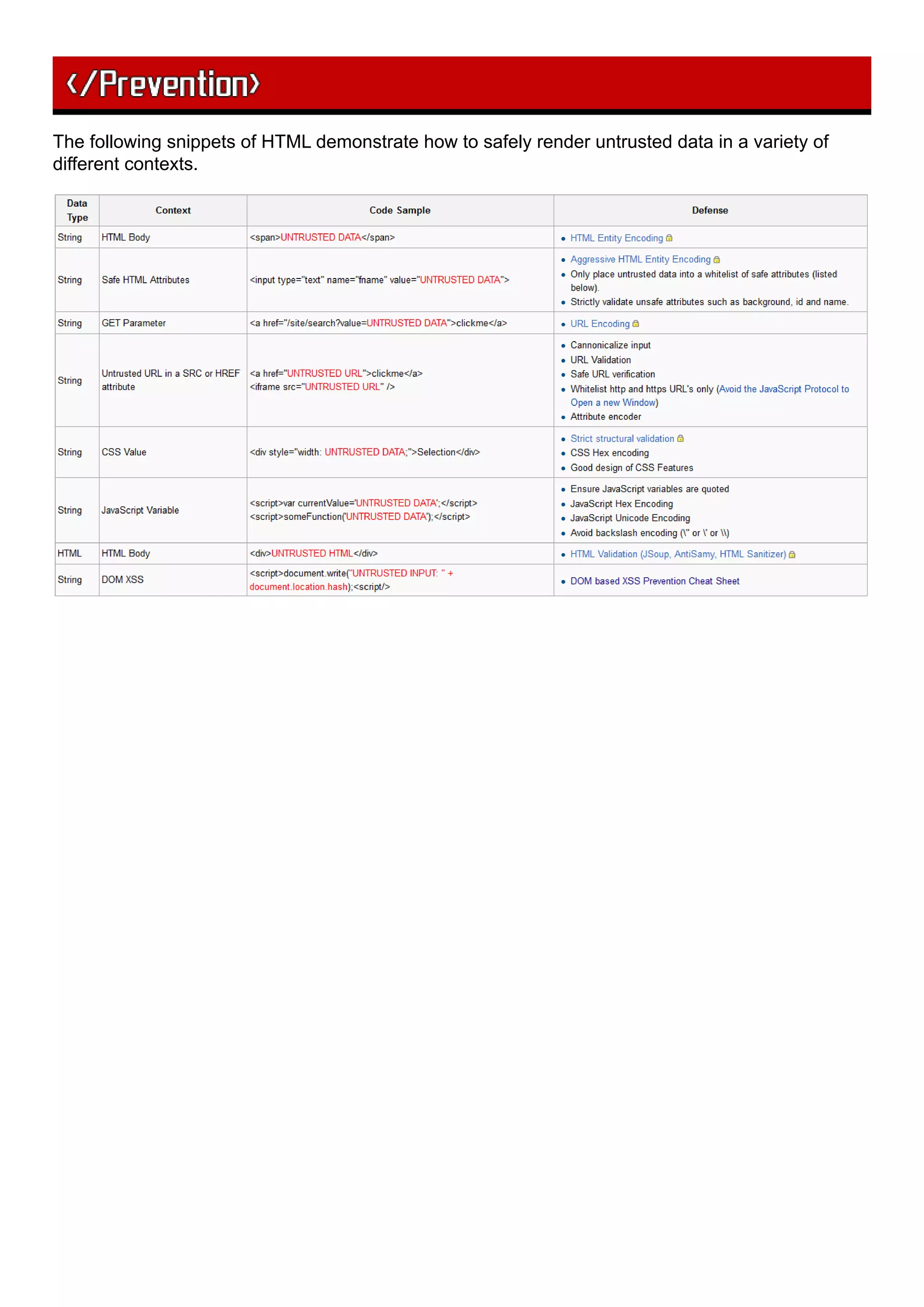
The document discusses cross-site scripting (XSS) attacks, how they work, and how to prevent them. XSS attacks involve injecting malicious HTML/JavaScript code into a website that is then executed by a user's browser and can be used to steal user data. The document covers different types of XSS attacks like stored and reflected XSS and how to prevent XSS vulnerabilities through sanitizing user input and only allowing safe HTML attributes.





![Example of Stored XSS: guestbook.php
Then page guestbook.php lists all entries returned by the previous function, without sanitizing the
content of the comments. It is only applied to the names (see function h() in the next section):
[---------------------------------------CODE---------------------------------------]
<?php
if ($guestbook)
{
foreach ($guestbook as $guest)
{
?>
<p class="comment"><?= $guest[" XSS SCRIPT "] ?></p>
<p> - by <?=h( $guest["name"] ) ?> </p>
<?php
} ?>
[---------------------------------------END CODE---------------------------------------]](https://image.slidesharecdn.com/16rtalkcs9cdb2jrovc8-140604101932-phpapp01/75/The-Cross-Site-Scripting-Guide-6-2048.jpg)